A new DNS threat actor dubbed Savvy Seahorse is leveraging subtle techniques to entice targets into bogus investment decision platforms and steal funds.
“Savvy Seahorse is a DNS risk actor who convinces victims to make accounts on bogus investment platforms, make deposits to a private account, and then transfers all those deposits to a financial institution in Russia,” Infoblox reported in a report revealed previous week.
Targets of the campaigns include things like Russian, Polish, Italian, German, Czech, Turkish, French, Spanish, and English speakers, indicating that the menace actors are casting a wide net in their assaults.
Consumers are lured through advertisements on social media platforms like Facebook, though also tricking them into parting with their private facts in return for alleged higher-return investment options via bogus ChatGPT and WhatsApp bots.

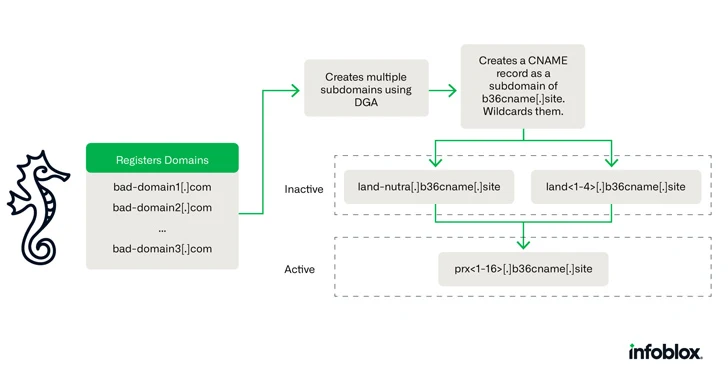
The financial fraud strategies are noteworthy for using DNS canonical name (CNAME) documents to generate a website traffic distribution program (TDS), therefore allowing for risk actors to evade detection because at the very least August 2021.
A CNAME file is applied to map a area or subdomain to an additional area (i.e., an alias) alternatively of pointing to an IP tackle. A single edge with this technique is that when the IP handle of the host modifications, only the DNS A file for the root area requirements to be up to date.
Savvy Seahorse leverages this technique to its advantage by registering many quick-lived subdomains that share a CNAME document (and so an IP tackle). These precise subdomains are made applying a domain technology algorithm (DGA) and are affiliated with the major campaign domain.
The ever-transforming nature of the domains and IP addresses also helps make the infrastructure resistant to takedown initiatives, permitting the menace actors to constantly build new domains or change their CNAME information to a distinctive IP deal with as their phishing websites are disrupted.
When risk actors like VexTrio have made use of DNS as a TDS, the discovery marks the initially time CNAME information have been used for these kinds of reasons.

Victims who end up clicking the back links embedded on Fb advertisements are urged to give their names, email addresses, and phone numbers, immediately after which they are redirected to the bogus trading system for including cash to their wallets.
“An important detail to observe is the actor validates the user’s information to exclude targeted visitors from a predefined checklist of international locations, including Ukraine, India, Fiji, Tonga, Zambia, Afghanistan, and Moldova, although their reasoning for deciding upon these particular nations is unclear,” Infoblox noted.
The progress will come as Guardio Labs disclosed that hundreds of domains belonging to genuine brand names and institutions have been hijacked making use of a technique known as CNAME takeover to propagate spam campaigns.
Uncovered this write-up fascinating? Stick to us on Twitter and LinkedIn to read through extra special written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Over 225,000 Compromised ChatGPT Credentials Up for Sale on Dark Web Markets
Over 225,000 Compromised ChatGPT Credentials Up for Sale on Dark Web Markets