Startups and scales-ups are usually cloud-initially corporations and almost never have sprawling legacy on-prem environments. Furthermore, being aware of the agility and flexibility that cloud environments provide, the mid-current market is predominantly functioning in a hybrid condition, partly in the cloud but with some on-prem property.
Whilst there has been a bit of a backswing towards the pricing and lock-in offered when making use of cloud infrastructure, cloud is nevertheless the most well-liked company for the the vast majority of SMBs.
As a final result, external attack surfaces are progressively elaborate and distributed and, thus, harder to observe and protected. This expanded attack surface area provides hackers plenty of blind spots and gaps to exploit. Security teams are on the back again, reacting, generally far too little by little, to improvements in their personal attack floor as engineering groups continually spin up and expose new programs, providers, and details to the internet.
This is compounded by the actuality that the risk landscape is usually switching. Countless numbers of new vulnerabilities are discovered each individual thirty day period, which includes vulnerabilities that make it possible for an attacker to gain full command more than units that have to be internet-experiencing and are intended to support security teams or facilitate secure connections (choose the spate of Citrix and Ivanti vulnerabilities that have not long ago emerged). How can you react to a new critical vulnerability which is becoming exploited by ransomware gangs if you never even know if your firm is using that technology and exposing it to the internet?
One of the explanations that security groups struggle is because procedures are reactive and understanding about the organization’s attack area is siloed in the heads of people people who are spinning up people cloud methods. Security teams rely on a sprawl of remedies that create hundreds of fragmented knowledge that is difficult to fully grasp, prioritize, and get motion. This is in which exposure management matches in as an extension of exterior attack floor management.
What is publicity administration in cybersecurity?
As environments evolve and come to be far more elaborate, so do the tools and procedures required to secure and guard them. Publicity management aims to reduce that complexity by giving you visibility of all details inside your attack floor that an attacker could use to breach your firm and finally pose a risk to the organization.
Publicity management aims to deliver a prioritized list of exposures, with context for each so that you can make an informed final decision on what to tackle initially and how to deal with it to lessen your company risk.
“Businesses who apply a constant exposure administration software will be three instances much less possible to be breached by 2026” (Gartner)
Exposure management can also assistance increase visibility of your full attack surface, like knowledge assets this kind of as code repositories like GitHub and GitLab, so you can far more precisely discover options for an attacker and shut them down in advance of they pose way too great of a risk to your business enterprise.
This suggests you can far better have an understanding of the threats you encounter, and prioritize the attacks that are not just a lot more very likely, but much more major. At a time when security groups are confused with data – above 25,000 vulnerabilities have been published in 2022, and we saw that maximize to in excess of 26,500 in 2023 – having a crystal clear photo of in which to target your time and hard work is becoming crucial.
Publicity management vs attack surface administration
Whilst both of those have the very same target, there are vital distinctions amongst the two. Exterior Attack Surface Management (ASM) is the ongoing procedure of exploring and figuring out property which can be viewed by an attacker on the internet, demonstrating in which security gaps exist, the place they can be employed to execute an attack, and wherever defenses are powerful plenty of to repel an attack. If you can scan for it making use of vulnerability scanning then it generally falls within attack area administration.
Exposure administration will take this a stage even further to include facts property, person identities, and cloud account configuration, which helps you fully grasp your publicity and decrease it wherever important.
Below the attack area contains any of the SaaS products and solutions you use. If just one of these will get compromised or just one of your accounts in your SaaS supplier gets compromised, they have information and facts that can be utilized to aid other assaults. So it should not be neglected when assessing risk to the business.
Visualize and lower your publicity with Intruder
Try to remember what was mentioned about a large attack surface remaining harder to defend? You can lessen yours by consistently checking for changes with an automatic vulnerability management resource like Intruder. Get finish management of your vulnerability administration to:
- Uncover property: when new cloud expert services are spun up and exposed to the internet, Intruder will kick off a scan to find any vulnerabilities so you can deal with them a lot quicker
- Know what is uncovered: get total visibility of your network perimeter, monitor energetic and unresponsive targets, identify alterations, monitor expiring certificates, and see any ports, products and services or protocols that shouldn’t be exposed to the internet
- Detect extra: Intruder employs many scanners to identify vulnerabilities and exposures throughout your attack surface area supplying you the biggest visibility
- Focus on the large issues: get final results prioritized centered on context, so you can aim on the most urgent issues devoid of wasting time sifting by means of the sounds
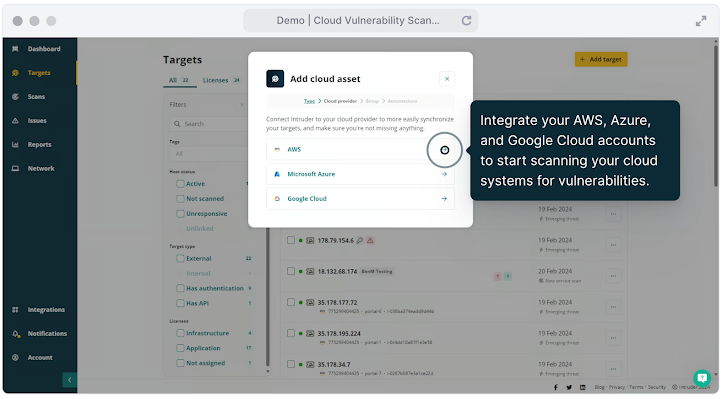 Intruder consistently screens and mechanically scans your environments as new vulnerabilities emerge
Intruder consistently screens and mechanically scans your environments as new vulnerabilities emerge
Premium and Vanguard consumers can also improve their exposure management with bug hunting, exactly where Intruder’s testers appear for the weaknesses and exposures that automated scanners can pass up. Get began with a 14-day free of charge trial right now.
Found this article fascinating? Adhere to us on Twitter and LinkedIn to read through additional unique material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Cybercriminals Using Novel DNS Hijacking Technique for Investment Scams
Cybercriminals Using Novel DNS Hijacking Technique for Investment Scams