Cybersecurity researchers have disclosed a new attack approach identified as Silver SAML that can be effective even in situations where by mitigations have been used against Golden SAML attacks.
Silver SAML “allows the exploitation of SAML to launch assaults from an identity company like Entra ID towards programs configured to use it for authentication, these kinds of as Salesforce,” Semperis researchers Tomer Nahum and Eric Woodruff mentioned in a report shared with The Hacker Information.
Golden SAML (short for Security Assertion Markup Language) was very first documented by CyberArk in 2017. The attack vector, in a nutshell, entails the abuse of the interoperable authentication regular to impersonate nearly any identification in an organization.
It is also comparable to the Golden Ticket attack in that it grants attackers the skill to acquire unauthorized accessibility to any services in a federation with any privileges and to keep persistent in this environment in a stealthy fashion.

“Golden SAML introduces to a federation the benefits that golden ticket offers in a Kerberos atmosphere – from attaining any sort of entry to stealthily protecting persistency,” security researcher Shaked Reiner pointed out at the time.
Serious-environment attacks leveraging the system have been scarce, the to start with recorded use currently being the compromise of SolarWinds infrastructure to obtain administrative accessibility by forging SAML tokens utilizing compromised SAML token signing certificates.
Golden SAML has also been weaponized by an Iranian danger actor codenamed Peach Sandstorm in a March 2023 intrusion to entry an unnamed target’s cloud methods sans necessitating any password, Microsoft discovered in September 2023.

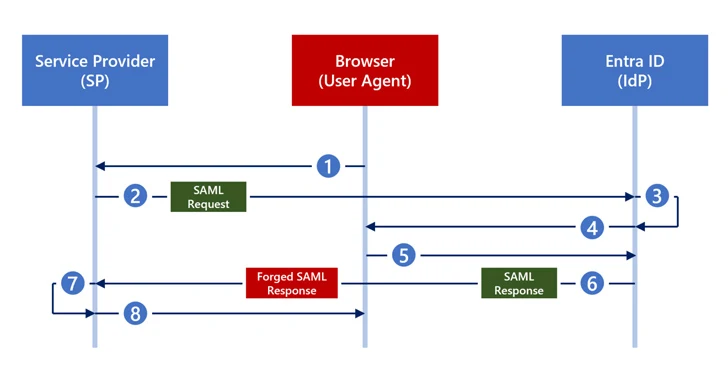
The hottest method is a spin on Golden SAML that functions with an identity service provider (IdP) like Microsoft Entra ID (previously Azure Energetic Directory) and would not involve entry to the Active Directory Federation Services (Ad FS). It has been assessed as a reasonable-severity threat to corporations.
“Inside Entra ID, Microsoft offers a self-signed certificate for SAML response signing,” the scientists mentioned. “Alternatively, corporations can pick out to use an externally created certificate such as those from Okta. Even so, that option introduces a security risk.”
“Any attacker that obtains the private critical of an externally produced certificate can forge any SAML reaction they want and sign that reaction with the exact personal critical that Entra ID holds. With this kind of cast SAML reaction, the attacker can then access the software — as any person.”
Next liable disclosure to Microsoft on January 2, 2024, the firm explained the issue does not meet up with its bar for rapid servicing, but observed it will take suitable action as needed to safeguard buyers.

While there is no proof that Silver SAML has been exploited in the wild, businesses are needed to use only Entra ID self-signed certificates for SAML signing applications. Semperis has also created out there a evidence-of-idea (PoC) dubbed SilverSAMLForger to build customized SAML responses.
“Corporations can observe Entra ID audit logs for changes to PreferredTokenSigningKeyThumbprint beneath ApplicationManagement,” the researchers stated.
“You will need to have to correlate individuals occasions to Incorporate provider principal credential situations that relate to the support principal. The rotation of expired certificates is a frequent method, so you will will need to figure out irrespective of whether the audit occasions are authentic. Applying modify handle procedures to doc the rotation can support to minimize confusion throughout rotation occasions.”
Observed this article appealing? Follow us on Twitter and LinkedIn to go through far more exceptional content material we post.
Some parts of this article are sourced from:
thehackernews.com

 GTPDOOR Linux Malware Targets Telecoms, Exploiting GPRS Roaming Networks
GTPDOOR Linux Malware Targets Telecoms, Exploiting GPRS Roaming Networks