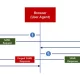
Risk hunters have found a new Linux malware referred to as GTPDOOR that is intended to be deployed in telecom networks that are adjacent to GPRS roaming exchanges (GRX)
The malware is novel in the actuality that it leverages the GPRS Tunnelling Protocol (GTP) for command-and-regulate (C2) communications.
GPRS roaming will allow subscribers to entry their GPRS products and services though they are outside of the access of their household cell network. This is facilitated by usually means of a GRX that transports the roaming website traffic utilizing GTP among the visited and the property Public Land Cell Network (PLMN).

Security researcher haxrob, who discovered two GTPDOOR artifacts uploaded to VirusTotal from China and Italy, explained the backdoor is likely linked to a identified threat actor tracked as LightBasin (aka UNC1945), which was earlier disclosed by CrowdStrike in October 2021 in relationship with a sequence of attacks focusing on the telecom sector to steal subscriber facts and contact metadata.

“When run, the first detail GTPDOOR does is course of action-title stomps itself – transforming its approach identify to ‘[syslog]’ – disguised as syslog invoked from the kernel,” the researcher explained. “It suppresses little one indicators and then opens a uncooked socket [that] will make it possible for the implant to get UDP messages that hit the network interfaces.”
Set otherwise, GTPDOOR will allow a danger actor that already has recognized persistence on the roaming exchange network to make contact with a compromised host by sending GTP-C Echo Request messages with a malicious payload.
This magic GTP-C Echo Request information functions as a conduit to transmit a command to be executed on the contaminated equipment and return the benefits back again to the distant host.

GTPDOOR “Can be covertly probed from an external network to elicit a reaction by sending a TCP packet to any port selection,” the researcher noted. “If the implant is lively a crafted vacant TCP packet is returned alongside with info if the desired destination port was open/responding on the host.”
“This implant seems like it is intended to sit on compromised hosts that immediately contact the GRX network – these are the methods that communicate to other telecommunication operator networks by using the GRX.”
Uncovered this write-up exciting? Abide by us on Twitter and LinkedIn to read through extra exceptional content we post.
Some parts of this article are sourced from:
thehackernews.com

 Lazarus Hackers Exploited Windows Kernel Flaw as Zero-Day in Recent Attacks
Lazarus Hackers Exploited Windows Kernel Flaw as Zero-Day in Recent Attacks