The infamous Lazarus Group actors exploited a just lately patched privilege escalation flaw in the Windows Kernel as a zero-day to attain kernel-level accessibility and disable security application on compromised hosts.
The vulnerability in concern is CVE-2024-21338 (CVSS score: 7.8), which can allow an attacker to get System privileges. It was settled by Microsoft earlier this thirty day period as aspect of Patch Tuesday updates.
“To exploit this vulnerability, an attacker would initial have to log on to the system,” Microsoft mentioned. “An attacker could then run a specifically crafted application that could exploit the vulnerability and consider handle of an afflicted procedure.”

Whilst there have been no indications of active exploitation of CVE-2024-21338 at the time of the launch of the updates, Redmond on Wednesday revised its “Exploitability assessment” for the flaw to “Exploitation Detected.”
Cybersecurity vendor Avast, which identified an in-the-wild admin-to-kernel exploit for the bug, stated the kernel read through/generate primitive realized by weaponizing the flaw permitted the Lazarus Team to “carry out immediate kernel item manipulation in an up-to-date edition of their knowledge-only FudModule rootkit.”
The FudModule rootkit was initial claimed by ESET and AhnLab in October 2022 as able of disabling the monitoring of all security remedies on infected hosts by signifies of what’s termed a Bring Your Possess Vulnerable Driver (BYOVD) attack, wherein an attacker a driver prone to a regarded or zero-day flaw to escalate privileges.
What helps make the latest attack significant is that it goes “further than BYOVD by exploiting a zero-day in a driver that’s identified to be currently set up on the concentrate on equipment.” That inclined driver is appid.sys, which is important to the performing of a Windows component known as AppLocker which is accountable for application command.
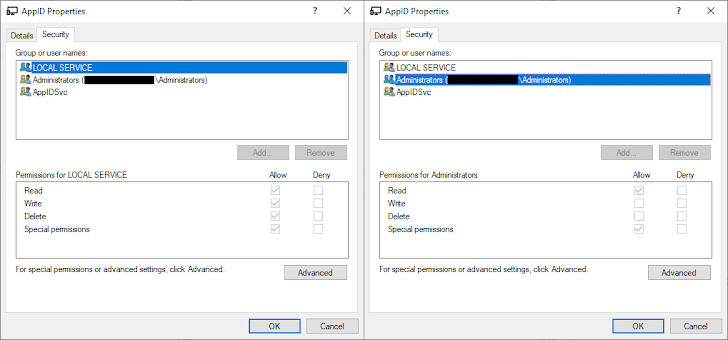
The authentic-planet exploit devised by the Lazarus Group entails utilizing CVE-2024-21338 in the appid.sys driver to execute arbitrary code in a manner that bypasses all security checks and operates the FudModule rootkit.
“FudModule is only loosely built-in into the rest of Lazarus’ malware ecosystem and that Lazarus is very mindful about employing the rootkit, only deploying it on demand less than the correct situation,” security researcher Jan Vojtěšek mentioned, describing the malware as less than energetic growth.
Apart from taking methods to sidestep detection by disabling system loggers, FudModule is engineered to flip off particular security software package this kind of as AhnLab V3 Endpoint Security, CrowdStrike Falcon, HitmanPro, and Microsoft Defender Antivirus (formerly Windows Defender).

The development marks a new amount of specialized sophistication connected with North Korean hacking teams, repeatedly iterating its arsenal for enhanced stealth and functionality. It also illustrates the elaborate tactics utilized to hinder detection and make their monitoring considerably more durable.
The adversarial collective’s cross-system target is also exemplified by the reality that it has been observed applying bogus calendar meeting invite backlinks to stealthily install malware on Apple macOS methods, a campaign that was beforehand documented by SlowMist in December 2023.
“Lazarus Team continues to be amid the most prolific and long-standing advanced persistent risk actors,” Vojtěšek claimed. “The FudModule rootkit serves as the most recent case in point, symbolizing a single of the most sophisticated equipment Lazarus retains in their arsenal.”
Located this write-up fascinating? Adhere to us on Twitter and LinkedIn to browse much more special content material we post.
Some parts of this article are sourced from:
thehackernews.com


 New Backdoor Targeting European Officials Linked to Indian Diplomatic Events
New Backdoor Targeting European Officials Linked to Indian Diplomatic Events