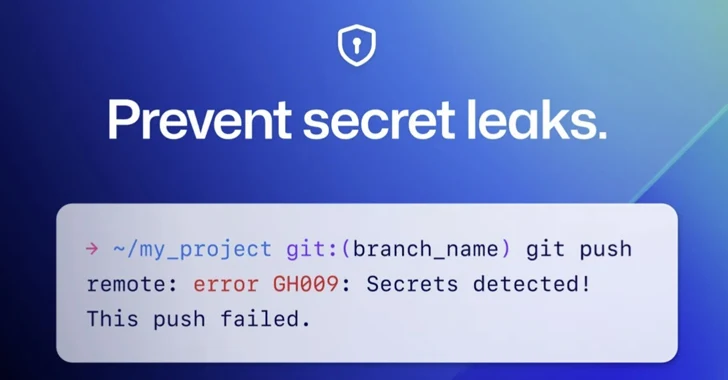
GitHub on Thursday announced that it is really enabling top secret scanning force protection by default for all pushes to public repositories.
“This implies that when a supported solution is detected in any drive to a community repository, you will have the choice to remove the mystery from your commits or, if you deem the top secret protected, bypass the block,” Eric Tooley and Courtney Claessens claimed.
Press safety was to start with piloted as an decide-in element in August 2023, even though it has been beneath screening due to the fact April 2022. It became typically obtainable in May perhaps 2023.
The magic formula scanning aspect is developed to establish above 200 token sorts and designs from much more than 180 company providers in buy to avert their fraudulent use by destructive actors.

The progress comes nearly 5 months after the Microsoft subsidiary expanded secret scanning to include things like validity checks for popular providers this sort of as Amazon Web Solutions (AWS), Microsoft, Google, and Slack.
It also follows the discovery of an ongoing “repo confusion” attack targeting GitHub that’s inundating the supply code hosting system with thousands of repositories made up of obfuscated malware capable of stealing passwords and cryptocurrency from developer devices.
The assaults symbolize one more wave of the exact malware distribution campaign that was disclosed by Phylum and Trend Micro previous yr, leveraging bogus Python offers hosted on the cloned, trojanized repositories to produce a stealer malware named BlackCap Grabber.
“Repo confusion attacks simply depend on individuals to mistakenly decide the malicious variation more than the authentic 1, sometimes utilizing social engineering tactics as nicely,” Apiiro reported in a report this 7 days.
Identified this post attention-grabbing? Observe us on Twitter and LinkedIn to go through additional distinctive written content we post.
Some parts of this article are sourced from:
thehackernews.com

 New Silver SAML Attack Evades Golden SAML Defenses in Identity Systems
New Silver SAML Attack Evades Golden SAML Defenses in Identity Systems