The 5 Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber menace actors exploiting known security flaws in Ivanti Hook up Protected and Ivanti Policy Protected gateways, noting that the Integrity Checker Instrument (ICT) can be deceived to present a wrong feeling of security.
“Ivanti ICT is not adequate to detect compromise and that a cyber danger actor could be ready to achieve root-degree persistence even with issuing factory resets,” the companies stated.
To date, Ivanti has disclosed five security vulnerabilities impacting its goods given that January 10, 2024, out of which four have occur under active exploitation by many threat actors to deploy malware –
- CVE-2023-46805 (CVSS score: 8.2) – Authentication bypass vulnerability in web element
- CVE-2024-21887 (CVSS rating: 9.1) – Command injection vulnerability in web part
- CVE-2024-21888 (CVSS score: 8.8) – Privilege escalation vulnerability in web part
- CVE-2024-21893 (CVSS rating: 8.2) – SSRF vulnerability in the SAML part
- CVE-2024-22024 (CVSS score: 8.3) – XXE vulnerability in the SAML element
Mandiant, in an assessment released this 7 days, described how an encrypted variation of malware recognised as BUSHWALK is put in a directory excluded by ICT in /info/runtime/cockpit/diskAnalysis.

The listing exclusions had been also beforehand highlighted by Eclypsium this month, stating the device skips a dozen directories from staying scanned, therefore permitting an attacker to go away driving backdoors in 1 of these paths and nonetheless move the integrity look at.
“The safest training course of action for network defenders is to assume a innovative risk actor may deploy rootkit level persistence on a product that has been reset and lay dormant for an arbitrary amount of money of time,” businesses from Australia, Canada, New Zealand, the U.K., and the U.S. explained.
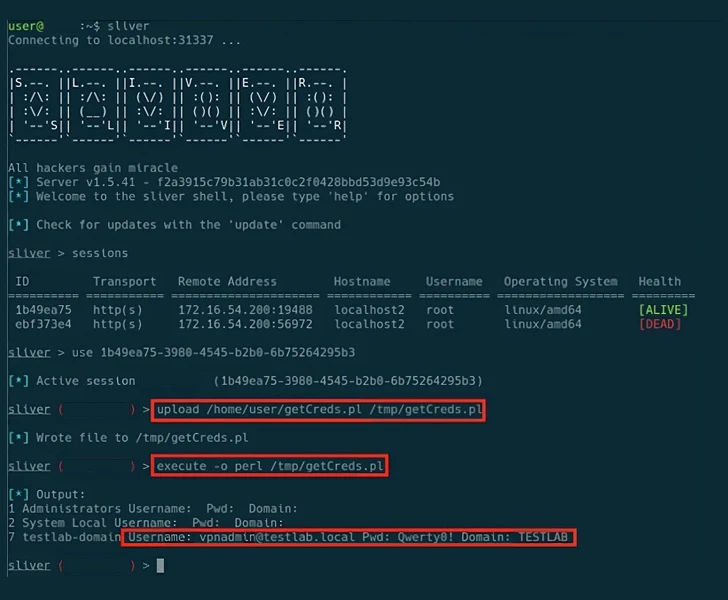
They also urged corporations to “take into account the sizeable risk of adversary obtain to, and persistence on, Ivanti Join Protected and Ivanti Plan Safe gateways when deciding whether or not to go on functioning these products in an enterprise ecosystem.”
Ivanti, in reaction to the advisory, stated it can be not knowledgeable of any scenarios of prosperous menace actor persistence subsequent the implementation of security updates and factory resets. It truly is also releasing a new version of ICT that it claimed “supplies further visibility into a customer’s equipment and all files that are present on the program.”
Located this posting attention-grabbing? Abide by us on Twitter and LinkedIn to go through much more distinctive articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 GitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories
GitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories