Cybersecurity scientists have learned a new Linux variant of a remote access trojan (RAT) called BIFROSE (aka Bifrost) that works by using a deceptive area mimicking VMware.
“This newest version of Bifrost aims to bypass security actions and compromise targeted devices,” Palo Alto Networks Device 42 researchers Anmol Maurya and Siddharth Sharma reported.
BIFROSE is one of the extended-standing threats that has been active since 2004. It has been made available for sale in underground forums for up to $10,000 in the earlier, according to a report from Craze Micro in December 2015.
The malware has been place to use by a point out-backed hacking team from China tracked as BlackTech (aka Circuit Panda, HUAPI, Manga Taurus, Palmerworm, PLEAD, Red Djinn, and Temp.Overboard), which has a history of placing companies in Japan, Taiwan, and the U.S.

It truly is suspected that the danger actor procured the supply code or acquired access to it all over 2010, and repurposed the malware for use in its personal strategies through custom made backdoors like KIVARS and XBOW.
Linux variants of BIFROSE (aka ELF_BIFROSE) have been noticed because at the very least 2020 with abilities to launch remote shells, obtain/upload files, and complete file functions.
“Attackers generally distribute Bifrost through email attachments or malicious web sites,” the scientists said. “After mounted on a victim’s laptop or computer, Bifrost permits the attacker to collect sensitive information and facts, like the victim’s hostname and IP address.”
What will make the newest variant noteworthy is that it reaches out to a command-and-regulate (C2) server with the title “down load.vmfare[.]com” in an try to masquerade as VMware. The misleading domain is solved by getting in contact with a Taiwan-centered general public DNS resolver with the IP tackle 168.95.1[.]1.
Unit 42 claimed it detected a spike in Bifrost action considering the fact that October 2023, determining no fewer than 104 artifacts in its telemetry. It more learned an Arm model of the malware, suggesting the menace actors are most likely wanting to grow their attack area.
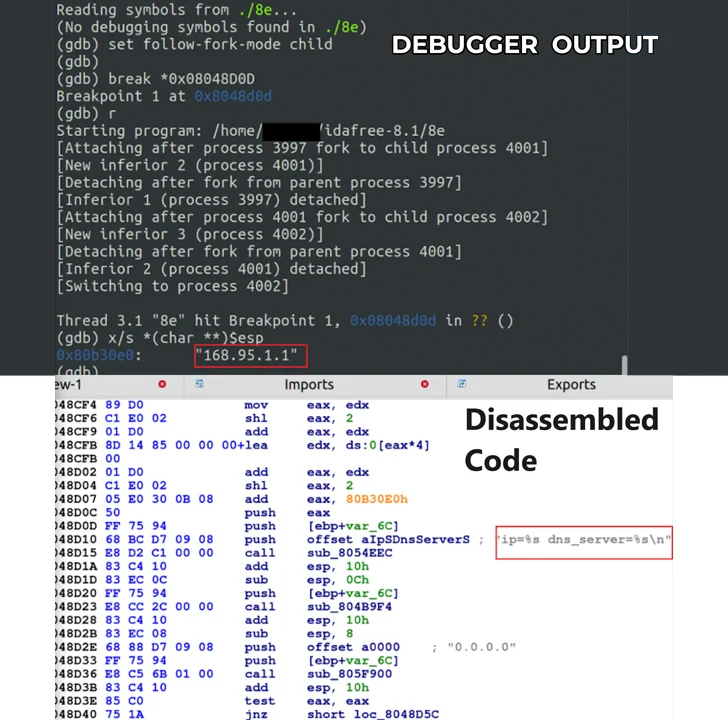
“With new variants that hire misleading area approaches like typosquatting, a modern spike in Bifrost action highlights the dangerous mother nature of this malware,” the scientists reported.
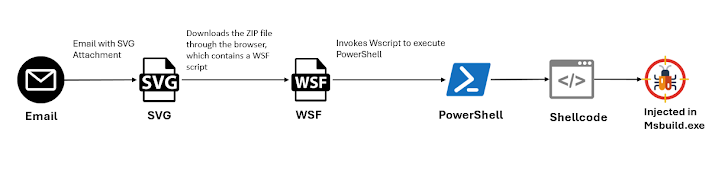
The improvement arrives as McAfee Labs in-depth a new GuLoader marketing campaign that propagates the malware by means of malicious SVG file attachments in email messages. The malware has also been noticed currently being dispersed by way of VBS scripts as component of a multi-phase payload delivery.

“This modern surge highlights its evolving techniques for broader reach and evasion,” Trustwave SpiderLabs explained in a write-up on X before this 7 days.
The Bifrost and GuLoader attacks coincide with the release of a new edition of the Warzone RAT, which not too long ago experienced two of its operators arrested and its infrastructure dismantled by the U.S. government.
Uncovered this write-up intriguing? Comply with us on Twitter and LinkedIn to read additional exceptional articles we post.
Some parts of this article are sourced from:
thehackernews.com


 Five Eyes Agencies Warn of Active Exploitation of Ivanti Gateway Vulnerabilities
Five Eyes Agencies Warn of Active Exploitation of Ivanti Gateway Vulnerabilities