Making sure delicate details stays confidential, secured from unauthorized access, and compliant with data privacy polices is paramount. Info breaches consequence in monetary and reputational injury but also direct to authorized outcomes. Hence, strong info obtain security measures are necessary to safeguard an organization’s belongings, maintain customer belief, and fulfill regulatory prerequisites.
A extensive Information Security Platform is critical for full visibility and regulate of delicate details. A person example is Satori’s Common Information Permissions Scanner (UDPS), an open-supply authorization evaluation instrument. UDPS, readily available on GitHub, allows common visibility into info accessibility permissions across different facts stores. With this software, it can be less complicated to determine who has the opportunity to entry delicate facts, which can aid corporations acquire a proactive technique to improving their security posture, streamline compliance, and make sure very well-ruled information accessibility.
Knowing the Want for Universal Data Permissions
In managing facts access permissions throughout substantial volumes of details, data engineers have to offer with various difficulties.
One such problem is the complexity of granting and revoking permissions to a variety of buyers throughout quite a few information repositories. As companies scale up their functions and details grows exponentially, holding monitor of who has accessibility to what becomes more and more demanding.
This complexity can guide to errors, security vulnerabilities, and troubles in keeping an audit trail of information access, which is vital for compliance and security purposes. Information engineers are frequently tasked with preserving a high-quality stability amongst providing entry to licensed consumers and safeguarding info from unauthorized access.
Dispersed Data Outlets
The facts accessibility permissions management landscape has turn out to be a lot more difficult in new decades owing to the popular adoption of cloud computing. Information engineers experience a remarkably distributed info landscape, with data now residing in on-prem data centers, multiple cloud platforms, and edge devices. Ensuring data security and governance across these numerous environments involves a extra unified strategy to knowledge obtain permissions.
The dynamic nature of the cloud signifies that regular access handle products might no longer suffice, and information engineers should undertake new paradigms that involve granular command, visibility, and governance.
Satori’s UDPS
Satori’s open up-resource UDPS takes a proactive and in depth tactic to information entry authorization. It scans and analyzes the permissions product of each and every information system to retrieve a human-readable checklist of buyers and their entry amount to info assets, which include database tables, cloud storage buckets, information, and a lot more.
As a substitute of demanding knowledge engineers to navigate the intricacies of every single specific details store’s accessibility controls, UDPS gives a unified platform to perspective and control facts permissions throughout all facts repositories. Data engineers no lengthier need to use distinctive obtain command mechanisms, decreasing the possible for mistakes and unauthorized access.
The standout feature of UDPS is its common visibility into info accessibility permissions. Soon after scanning all databases, knowledge warehouses, cloud accounts, and knowledge lakes, UDPS analyzes the permissions and retrieves a listing of people, their access levels, and what they have access to.
The Universal Data Permissions Scanner is out there in two ways:
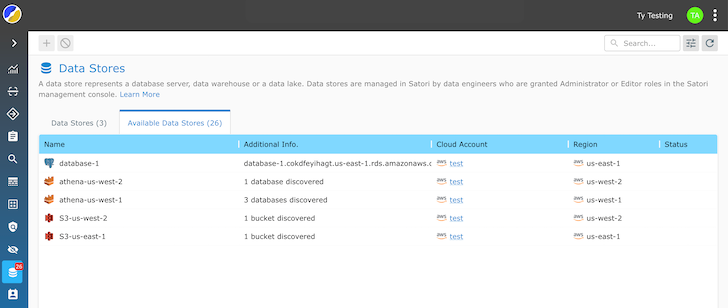
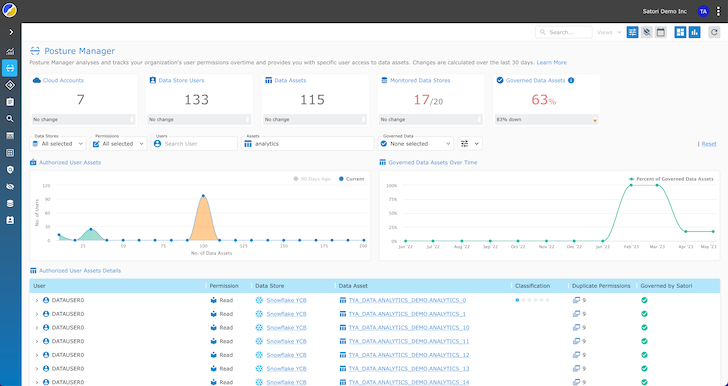
Facts engineers get bigger visibility, permitting them to speedily discover overprivileged end users, unauthorized accessibility, or unconventional actions in genuine time. Universal visibility simplifies the auditing course of action and assures that details access stays transparent and compliant with security and privacy regulations.
Facts engineers can effectively deal with facts security and governance, decreasing secure and compliant information obtain issues.
Advantages of Applying an OS UDPS
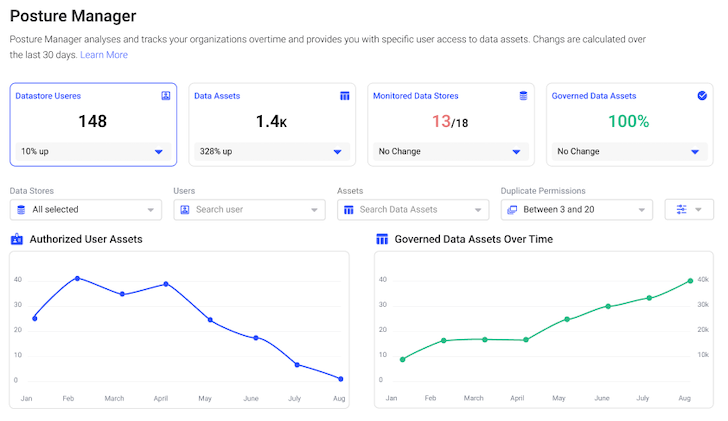
Ease of Implementation
Some essential insights into the relieve of employing Satori’s option:
- Agentless Deployment: There is no will need to install brokers or added software program on your data shops or techniques. This agentless solution simplifies the deployment method and eliminates the have to have for complicated configurations or alterations to your current infrastructure.
- Zero Code Improvements: It does not demand any alterations to existing details constructions or schemas. The facts continues to be intact and retains its structure.
- Consumer-Helpful Interface: The interface simplifies the definition and enforcement of info access procedures. Security and info engineering groups can very easily configure and take care of good-grained insurance policies to regulate who can entry specific information aspects devoid of requiring specialized coding or extensive complex expertise.
- Serious-time Policy Updates: Makes it possible for for real-time coverage updates so that security actions are tailored on the fly to handle rising threats or shifting compliance demands. This agility simplifies the ongoing management of details security controls.
- Non-Intrusive Info Encryption: Transparent information encryption that does not disrupt current consumer interactions. Information continues to be available to licensed consumers without apparent modifications in how they interact.
- Compatibility and Scalability: Appropriate with many details outlets, databases, knowledge lakes, and cloud platforms. It also scales with your organization’s requirements.
Implementation is a easy and headache-absolutely free procedure. It doesn’t call for alterations to your data buildings or person interactions. The ease of implementation helps make Satori an beautiful answer for companies searching to improve their facts security effortlessly.
Summary
Satori’s Universal Facts Permissions Scanner (UDPS) simplifies details entry authorization complexities by delivering a centralized, non-intrusive solution. It gives universal visibility into info access permissions across varied facts repositories, enabling companies to identify overprivileged consumers, streamline compliance reporting, and increase data security. It is uncomplicated to implement, with no modifications to current data constructions or person interactions read through additional about the UDPS in the task documentation.
Businesses can detect uncommon actions, track facts use, and simplify authorization management, contributing to a more robust security posture and streamlined information governance.
Observed this report intriguing? Adhere to us on Twitter and LinkedIn to examine a lot more special content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 GitHub’s Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack
GitHub’s Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack