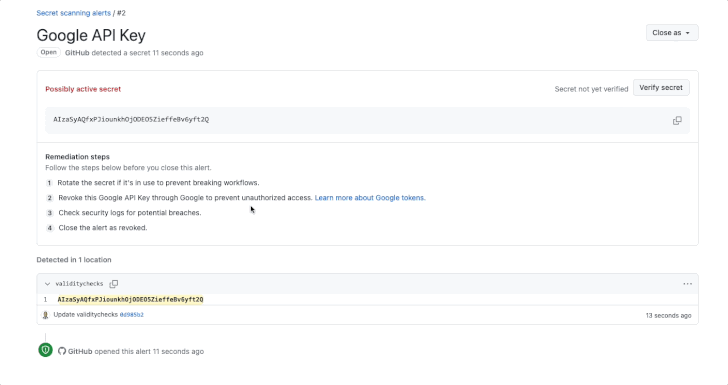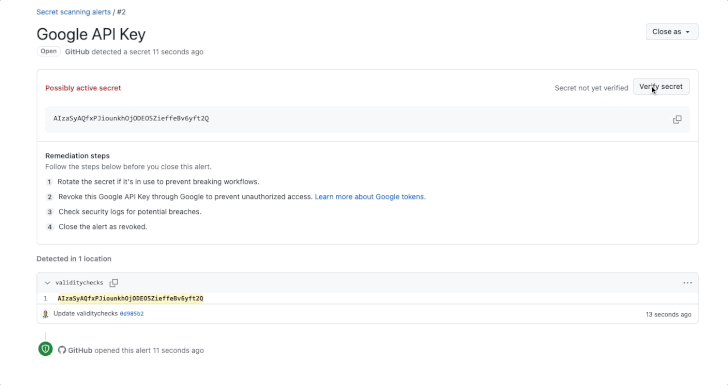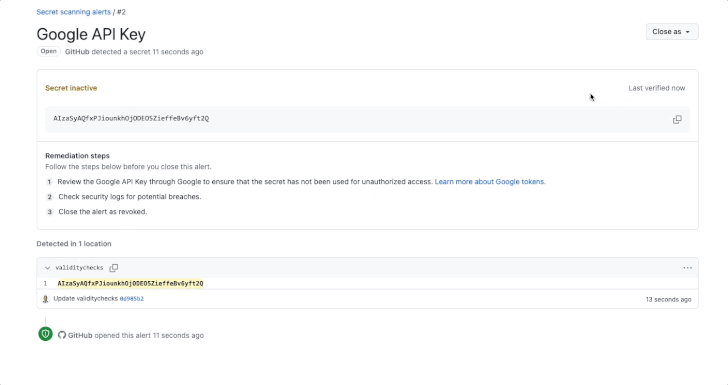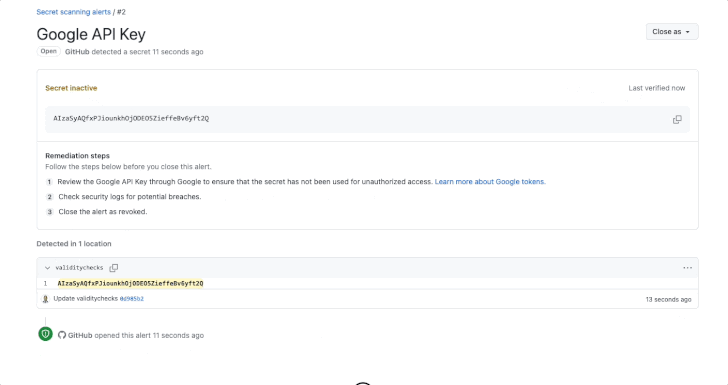
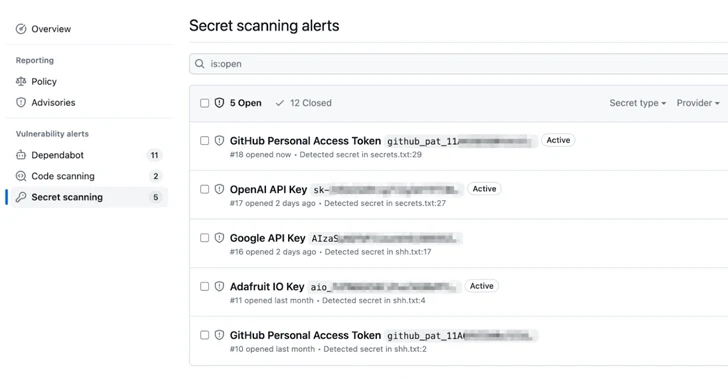
GitHub has announced an improvement to its key scanning characteristic that extends validity checks to popular providers this kind of as Amazon Web Providers (AWS), Microsoft, Google, and Slack.
Validity checks, released by the Microsoft subsidiary before this 12 months, notify consumers whether or not uncovered tokens discovered by mystery scanning are active, therefore allowing for for helpful remediation steps. It was to start with enabled for GitHub tokens.
The cloud-primarily based code hosting and version manage company said it intends to assist a lot more tokens in the foreseeable future.
To toggle the location, organization or organization owners and repository directors can head to Options > Code security and examination > Key scanning and check out the possibility “Instantly verify if a magic formula is legitimate by sending it to the suitable companion.”
Previously this calendar year, GitHub also expanded secret scanning alerts for all community repositories and introduced the availability of press defense to support builders and maintainers proactively protected their code by scanning for hugely identifiable strategies ahead of they are pushed.

The growth will come as Amazon previewed enhanced account defense prerequisites that will enforce privileged consumers (aka root consumers) of an AWS Business account to swap on multi-issue authentication (MFA) commencing in mid-2024.
“MFA is one particular of the most basic and most helpful methods to improve account security, giving an extra layer of security to aid avoid unauthorized people from getting accessibility to techniques or information,” Steve Schmidt, main security officer at Amazon, claimed.
Weak or misconfigured MFA procedures also observed a put amid the leading 10 most frequent network misconfigurations, according to a new joint advisory issued by the U.S. National Security Agency (NSA) and Cybersecurity and Infrastructure Security Company (CISA).
“Some varieties of MFA are vulnerable to phishing, ‘push bombing,’ exploitation of Signaling Procedure 7 (SS7) protocol vulnerabilities, and/or ‘SIM swap’ strategies,” the agencies claimed.
“These tries, if successful, might allow for a risk actor to attain accessibility to MFA authentication credentials or bypass MFA and entry the MFA-guarded techniques.”
The other widespread cybersecurity misconfigurations are as follows –
- Default configurations of program and purposes
- Improper separation of consumer/administrator privilege
- Inadequate inner network monitoring
- Lack of network segmentation
- Very poor patch management
- Bypass of procedure obtain controls
- Insufficient accessibility handle lists (ACLs) on network shares and services
- Inadequate credential hygiene
- Unrestricted code execution
As mitigations, it truly is proposed that corporations eradicate default credentials and harden configurations disable unused providers and apply obtain controls prioritize patching audit and check administrative accounts and privileges.

Program suppliers have also been urged to put into action secure by layout concepts, use memory-safe and sound programming languages wherever feasible, stay away from embedding default passwords, present superior-high-quality audit logs to prospects at no extra charge, and mandate phishing-resistant MFA solutions.
“These misconfigurations illustrate (1) a craze of systemic weaknesses in lots of massive corporations, which include these with mature cyber postures, and (2) the importance of program makers embracing secure-by-design and style ideas to reduce the burden on network defenders,” the companies observed.
Observed this short article intriguing? Comply with us on Twitter and LinkedIn to read extra exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Supermicro’s BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities
Supermicro’s BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities