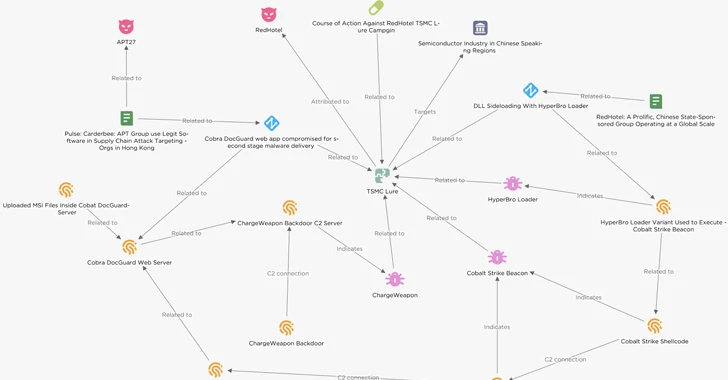
Menace actors have been noticed concentrating on semiconductor providers in East Asia with lures masquerading as Taiwan Semiconductor Manufacturing Corporation (TSMC) that are designed to provide Cobalt Strike beacons.
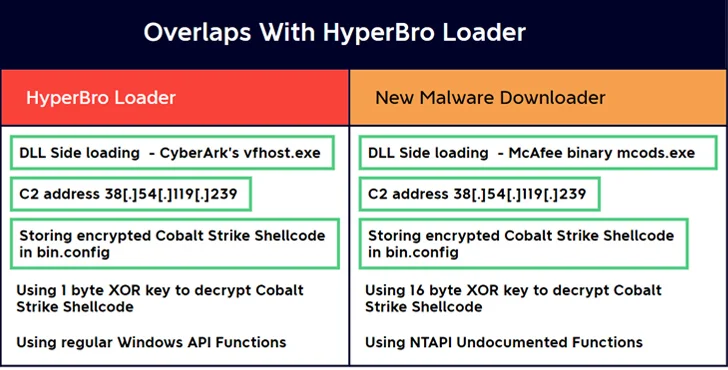
The intrusion established, for each EclecticIQ, leverages a backdoor named HyperBro, which is then made use of as a conduit to deploy the industrial attack simulation computer software and put up-exploitation toolkit.
An alternate attack sequence is explained to have utilized a previously undocumented malware downloader to deploy Cobalt Strike, indicating that the menace actors devised several strategies to infiltrate targets of fascination.
The Dutch cybersecurity agency attributed the campaign to a China-joined menace actor owing to the use of HyperBro, which has been pretty much completely put to use by a risk actor acknowledged as Lucky Mouse (aka APT27, Budworm, and Emissary Panda).
Tactical overlaps have also been unearthed in between the adversary guiding the assaults and a different cluster tracked by RecordedFuture beneath the name RedHotel, which also overlaps with a hacking crew known as Earth Lusca.

Yet another Chinese link will come from the use of a possible compromised Cobra DocGuard web server to host 2nd-stage binaries, which include a Go-based implant dubbed ChargeWeapon, for distribution through the downloader.
“ChargeWeapon is built to get remote accessibility and ship product and network info from an contaminated host to an attacker managed [command-and-control] server,” EclecticIQ researcher Arda Büyükkaya stated in a Thursday evaluation.
It really is really worth noting that a trojanized version of EsafeNet’s Cobra DocGuard encryption computer software has also been linked to the deployment of PlugX, with Symantec linking it to a suspected China-nexus actor codenamed Carderbee.
In the attack chain documented by EclecticIQ, a TSMC-themed PDF doc is exhibited as a decoy subsequent the execution of HyperBro, indicating the use of social engineering strategies to activate the an infection.
“By presenting a standard wanting PDF though covertly functioning malware in the qualifications, the probabilities of the victim developing suspicious are minimized,” Büyükkaya spelled out.
A noteworthy aspect of the attack is that the C2 server deal with challenging-coded into the Cobalt Strike beacon is disguised as a authentic jQuery CDN in an exertion to bypass firewall defenses.
The disclosure will come as the Financial Periods documented that Belgium’s intelligence and security company, the Condition Security Service (VSSE), is working to “detect and fight towards probable spying and/or interference functions carried out by Chinese entities together with Alibaba” at the country’s Liège cargo airport.

Alibaba has denied any wrongdoing.
“China’s actions in Belgium are not minimal to the typical spy stealing condition techniques or the hacker paralyzing an essential sector or federal government section from behind his Computer system,” the agency observed in an intelligence report. “In an try to impact conclusion-producing procedures, China utilizes a assortment of state and non-point out resources.”
A report unveiled by the U.S. Department of Protection (DoD) very last thirty day period described China as posing a “broad and pervasive cyber espionage danger,” and that it steals technology techniques and undertakes surveillance endeavours to get a strategic gain.
“Utilizing cyber usually means, the PRC has engaged in extended strategies of espionage, theft, and compromise from essential protection networks and broader U.S. critical infrastructure, especially the Protection Industrial Foundation (DIB),” DoD said.
Uncovered this posting interesting? Comply with us on Twitter and LinkedIn to read far more exclusive material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 New OS Tool Tells You Who Has Access to What Data
New OS Tool Tells You Who Has Access to What Data