As much as $7 billion in cryptocurrency has been illicitly laundered as a result of cross-chain crime, with the North Korea-joined Lazarus Team linked to the theft of around $900 million of people proceeds amongst July 2022 and July of this yr.
“As traditional entities such as mixers continue to be subject to seizures and sanctions scrutiny, the crypto criminal offense displacement to chain- or asset-hopping typologies is also on the increase,” blockchain analytics business Elliptic said in a new report revealed this 7 days.
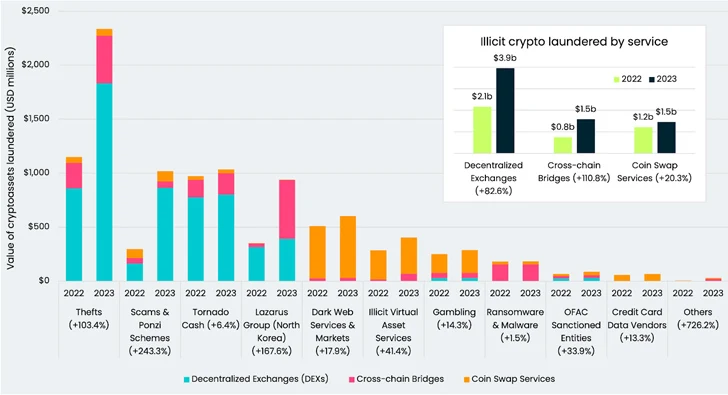
Cross-chain criminal offense refers to the conversion of crypto property from one particular token or blockchain to a further, often in immediate succession, in an try to obfuscate their origin, generating it a valuable strategy for revenue laundering for crypto thefts and an choice to Acc strategies like mixers.
According to info collected by Elliptic, the Lazarus Group’s use of cross-chain bridges contributed to a bulk of the 111% increase in the proportion of money despatched by means of this sort of solutions.

The North Korean hacking crew is estimated to have stolen almost $240 million in cryptocurrency considering that June 2023, subsequent a collection of attacks focusing on Atomic Wallet ($100 million), CoinsPaid ($37.3 million), Alphapo ($60 million), Stake.com ($41 million), and CoinEx ($31 million).
“The range, number, and eccentricity in implementation of Lazarus strategies outline this team, as properly as that it performs all three pillars of cybercriminal routines: cyber espionage, cyber sabotage, and pursuit of economic attain,” ESET said of the danger actor late final month.
The menace actor has also been joined to the use of Avalanche Bridge to deposit additional than 9,500 bitcoin, even though at the same time utilizing cross-chain alternatives to go some of the plundered property.

“As is evidenced by the belongings ending up on the very same blockchain on several instances, these transactions have no authentic business reason other than to obfuscate their origin,” Elliptic said. “Bridging back again-and-forth for the sake of obfuscation – i.e. ‘chain-hopping’ – is now a acknowledged revenue laundering typology.”
The disclosure arrives as South Korea’s Countrywide Intelligence Support (NIS) has warned of North Korea attacking its shipbuilding sector given that the get started of the year.
“The hacking techniques generally applied by North Korean hacking companies were being to occupy and bypass the PCs of IT servicing corporations, and to install malicious code right after distributing phishing e-mails to inner staff members,” the company stated.
Found this posting intriguing? Follow us on Twitter and LinkedIn to study more exceptional articles we put up.
Some parts of this article are sourced from:
thehackernews.com


