The destructive code inserted into the open-resource library XZ Utils, a greatly employed deal present in significant Linux distributions, is also able of facilitating distant code execution, a new analysis has unveiled.
The audacious offer chain compromise, tracked as CVE-2024-3094 (CVSS rating: 10.), came to gentle last 7 days when Microsoft engineer and PostgreSQL developer Andres Freund alerted to the presence of a backdoor in the info compression utility that offers remote attackers a way to sidestep safe shell authentication and attain complete obtain to an influenced program.
XZ Utils is a command-line resource for compressing and decompressing knowledge in Linux and other Unix-like functioning devices.
The malicious code is mentioned to have been deliberately released by a person of the undertaking maintainers named Jia Tan (aka Jia Cheong Tan or JiaT75) in what seems to be a meticulous attack spanning a number of several years. The GitHub consumer account was developed in 2021. The identification of the actor(s) is presently unidentified.

“The threat actor started off contributing to the XZ venture pretty much two several years back, gradually making believability right until they ended up supplied maintainer responsibilities,” Akamai mentioned in a report.
In a more act of clever social engineering, sockpuppet accounts like Jigar Kumar and Dennis Ens are believed to have been applied to ship element requests and report a wide range of issues in the program in buy to pressure the original maintainer – Lasse Collin of the Tukaani Challenge – to incorporate a new co-maintainer to the repository.
Enter Jia Tan, who launched a series of modifications to XZ Utils in 2023, which ultimately produced their way to release variation 5.6. in February 2024. They also harbored a complex backdoor.
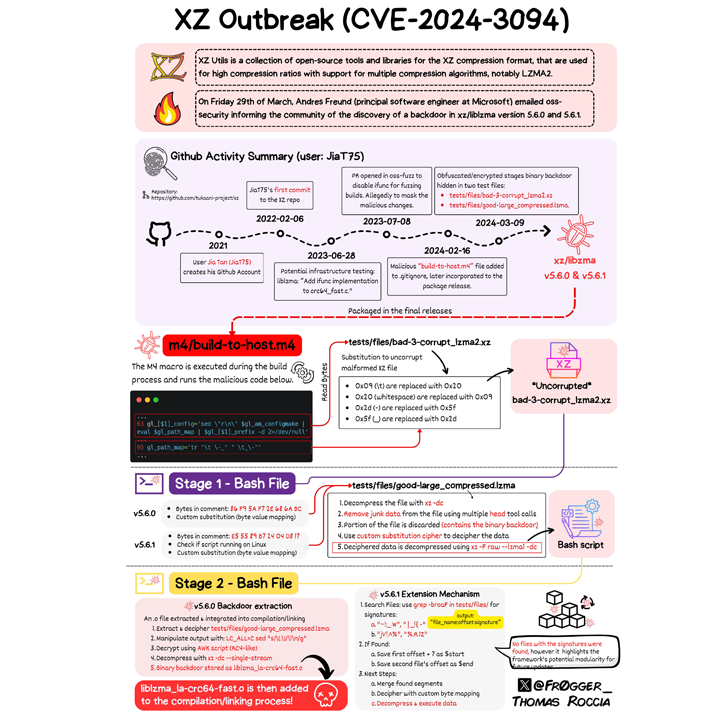 Source: Thomas Roccia
Source: Thomas Roccia
“As I have hinted in before e-mails, Jia Tan may well have a greater purpose in the project in the long run,” Collin mentioned in an exchange with Kumar in June 2022.
“He has been encouraging a lot off-listing and is virtually a co-maintainer by now. 🙂 I know that not significantly has occurred in the git repository still but things come about in modest methods. In any circumstance some modify in maintainership is by now in progress at least for XZ Utils.”
The backdoor has an effect on XZ Utils 5.6. and 5.6.1 release tarballs, the latter of which consists of an enhanced version of the exact same implant. Collins has because acknowledged the project’s breach, stating each the tarballs had been produced and signed by Jia Tan and that they experienced obtain only to the now-disabled GitHub repository.
“This is plainly a incredibly complex point out-sponsored operation with amazing sophistication and multi-year arranging,” firmware security enterprise Binarly claimed. “These types of a intricate and skillfully made extensive implantation framework is not designed for a just one-shot operation.”
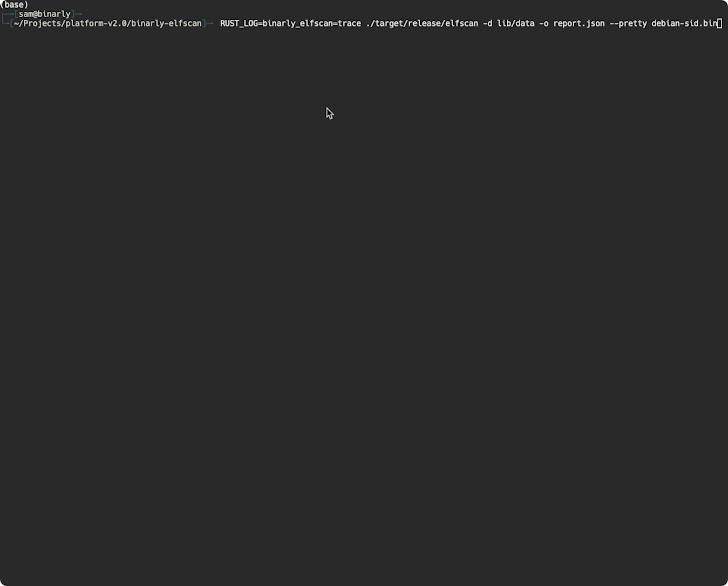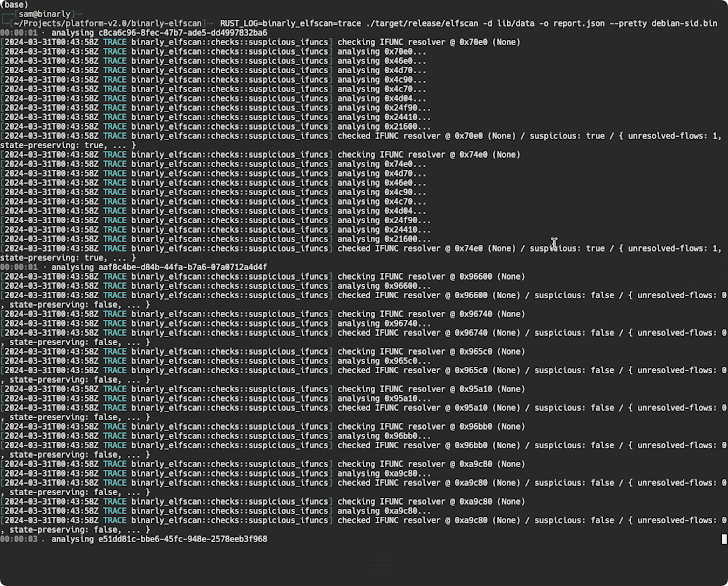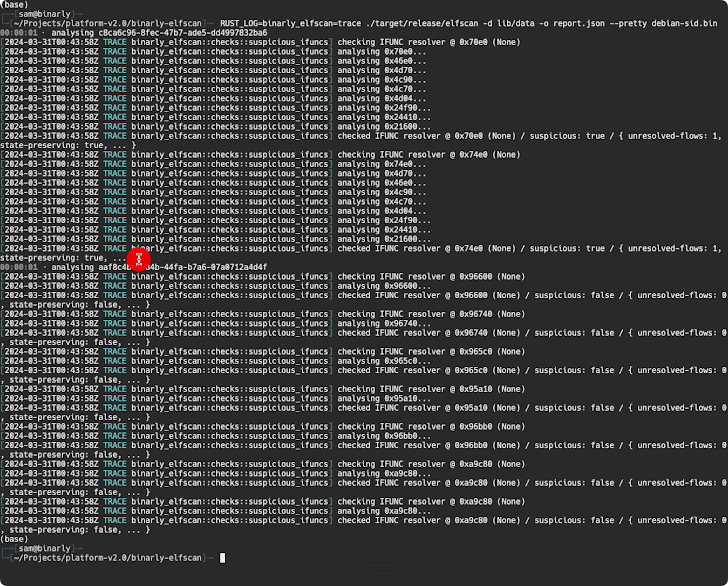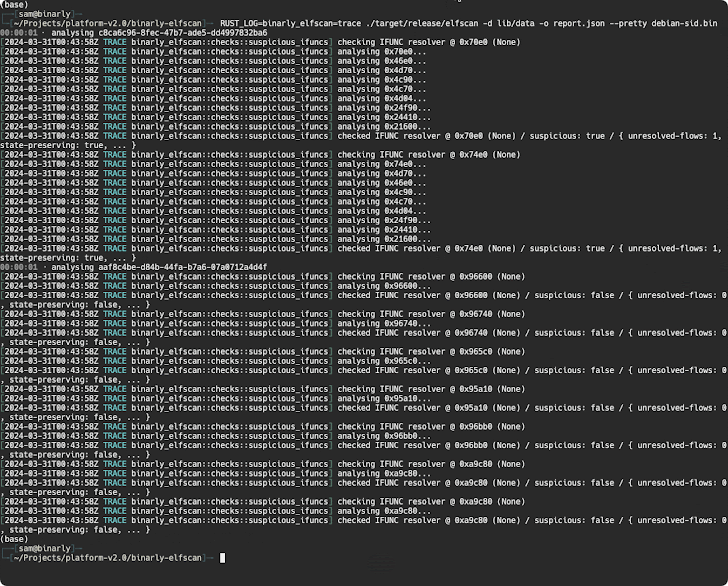
A further examination of the backdoor by open-resource cryptographer Filippo Valsorda has also disclosed that the afflicted variations allow unique remote attackers to mail arbitrary payloads by means of an SSH certificate which will be executed in a manner that circumvents authentication protocols, proficiently seizing management in excess of the target machine.
“It appears as nevertheless the backdoor is additional to the SSH daemon on the susceptible equipment, enabling a distant attacker to execute arbitrary code,” Akamai mentioned. “This suggests that any machine with the susceptible offer that exposes SSH to the internet is probably vulnerable.”

Pointless to say, the accidental discovery by Freund is one of the most sizeable source chain assaults identified to day and could have been a critical security catastrophe had the deal been integrated into steady releases of Linux distributions.
“The most notable part of this source chain attack is the excessive levels of perseverance of the attacker, working a lot more than two several years to set up them selves as a respectable maintainer, featuring to decide up get the job done in many OSS jobs and committing code throughout numerous projects in get to stay clear of detection,” JFrog claimed.
As with the situation of Apache Log4j, the incident at the time again highlights the reliance on open-supply software package and volunteer-operate projects, and the repercussions that could entail should they suffer a compromise or have a important vulnerability.
“The larger ‘fix’ is for organizations to undertake equipment and processes that allow them to detect symptoms of tampering and destructive capabilities inside each open resource and business code utilized in their have progress pipeline,” ReversingLabs explained.
Found this article attention-grabbing? Observe us on Twitter and LinkedIn to read through a lot more distinctive material we publish.
Some parts of this article are sourced from:
thehackernews.com

 Harnessing the Power of CTEM for Cloud Security
Harnessing the Power of CTEM for Cloud Security