A critical security flaw impacting the LayerSlider plugin for WordPress could be abused to extract delicate information and facts from databases, such as password hashes.
The flaw, selected as CVE-2024-2879, carries a CVSS score of 9.8 out of a highest of 10.. It has been explained as a situation of SQL injection impacting variations from 7.9.11 by means of 7.10..
The issue has been resolved in edition 7.10.1 launched on March 27, 2024, subsequent responsible disclosure on March 25. “This update features critical security fixes,” the maintainers of LayerSlider explained in their release notes.
LayerSlider is a visible web content material editor, a graphic layout application, and a electronic visual results that permits end users to make animations and loaded content material for their internet websites. According to its personal web-site, the plugin is employed by “millions of users all over the world.”

The flaw identified in the instrument stems from a case of insufficient escaping of consumer supplied parameters and the absence of wpdb::prepare(), enabling unauthenticated attackers to append further SQL queries and glean sensitive information and facts, Wordfence stated.
The advancement follows the discovery of an unauthenticated saved cross-internet site scripting (XSS) flaw in the WP-Members Membership Plugin (CVE-2024-1852, CVSS score: 7.2) that could aid the execution of arbitrary JavaScript code. It has been resolved in edition 3.4.9.3.
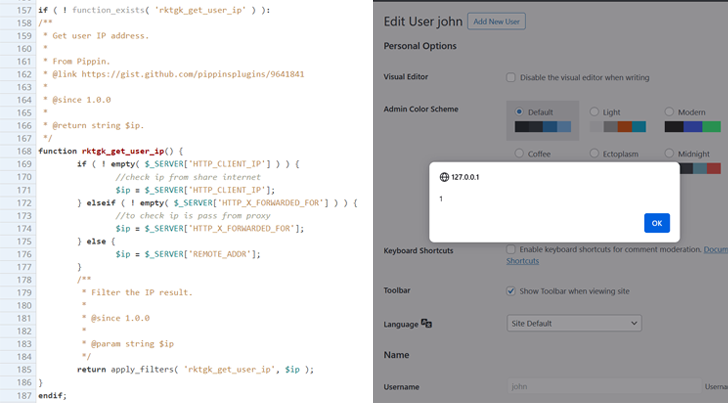
The vulnerability, due to insufficient input sanitization and output escaping, “helps make it achievable for unauthenticated attackers to inject arbitrary web scripts in internet pages that will execute anytime a person accesses an injected web page which is the edit consumers web page,” the WordPress security corporation reported.
Should the code be executed in the context of an administrator’s browser session, it can be made use of to generate rogue consumer accounts, redirect site people to other malicious web sites, and carry out other assaults, it included.
More than the past handful of weeks, security vulnerabilities have also been disclosed in other WordPress plugins such as Tutor LMS (CVE-2024-1751, CVSS score: 8.8) and Call Sort Entries (CVE-2024-2030, CVSS rating: 6.4) that could be exploited for information disclosure and inject arbitrary web scripts, respectively.
Found this report interesting? Adhere to us on Twitter and LinkedIn to examine much more distinctive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Malicious Code in XZ Utils for Linux Systems Enables Remote Code Execution
Malicious Code in XZ Utils for Linux Systems Enables Remote Code Execution