Cloud answers are extra mainstream – and for that reason extra exposed – than ever just before.
In 2023 alone, a staggering 82% of facts breaches ended up against community, non-public, or hybrid cloud environments. What is actually more, nearly 40% of breaches spanned numerous cloud environments. The normal cost of a cloud breach was earlier mentioned the general regular, at $4.75 million. In a time where cloud has turn into the de facto conventional – with 65% of IT determination-makers confirming that cloud-dependent expert services are their initially decision when upgrading or acquiring new answers – even with its overwhelming prominence, cloud security nevertheless faces several issues.
Security Troubles in the Cloud
A person key hurdle is the absence of visibility. Contrary to actual physical servers you can see and contact, cloud methods are frequently distribute throughout wide networks, earning it complicated to monitor for suspicious exercise and leaving vulnerabilities undetected. Another challenge is the inconsistency throughout cloud vendor authorization management units. Unique providers have distinct controls for who can access and modify information. This inconsistency generates complexity and raises the risk of accidental misconfigurations, which are a major cause of breaches.
Additionally, with a number of teams concerned in cloud deployments – progress, operations, security – apparent possession and accountability for cloud security can be blurred. This deficiency of coordination can lead to scenarios wherever security most effective procedures are disregarded or bypassed. Additionally, many assaults shift across the cloud to on-prem environments and vice versa, which can place both environments at risk.
All these troubles highlight the urgent will need for sturdy cloud security alternatives that give comprehensive visibility, standardized authorization management, and very clear strains of obligation. However security methods are stretched skinny even in the most effective-provisioned groups – and cloud security groups are predicted to examine and remediate thousands of exposures that may well not all have the exact effect on critical means. This prospects to uncertainty all around what to repair initially and how to really tackle all the discovered exposures, leaving cloud environments exposed to cyberattacks.
Continuous Publicity Administration is Vital
Rather of chasing a great number of vulnerabilities, security teams require to prioritize the most critical types. This indicates staying ready to quickly identify the most dangerous attack paths and choose preemptive action in opposition to advanced attack techniques in the cloud.
By focusing on higher-risk places, cloud security groups can build focused remediation plans that avert key attacks, streamline workflows, and properly report on serious threats across numerous cloud environments. The essential to reaching this is Continual Risk Publicity Administration (CTEM), a proactive and continuous five-phase method or framework that reduces exposure to cyberattacks. To start with released by Gartner in 2022, CTEM has confirmed necessary for protecting against higher-impression attacks, bettering remediation performance, and reporting real risk.
.xm_container material .e book-graphic write-up .book-facts obtain a.qualifications-cta.cf articles .information-book ul information .bottom-direction ul li post @media (max-width: 600px) { .xm_container articles .proper-bottom put up }

Stop letting
enjoy join hackers Find solution-the-dots with your cloud security. really don’t the Ebook map they Electrical power want you to have in our Master: ‘The protected of Attack Paths in Cloud’ electronic to visualize, intercept, and under no circumstances your just before fortress like introduced solve.
CTEM was challenge to limitless the additional of particularly lists of exposures, and across getting vulnerabilities, capable on-prem environments. Not highlight take care of to groups and correcting the exposures that are most critical leaves security could could CVEs that certain or setting not be exploitable or impactful in their may perhaps with each other. In multi-cloud environments, the lists of vulnerabilities extremely be shorter, but access with misconfigurations and insert privileged extensive, they list up to a atmosphere groups of exposures that attackers can use to breach the multi-cloud have to and that security handle attacks pinpointing. The only way to block fixing is by maximum and effect the exposures with the company requires on your environment. That Deal with adopting the CTEM framework in the cloud Matters.
Throughout What aid groups Multi-Cloud
To fix cloud security matters higher what effect and block attacks-comprehensive program in multi-cloud environments, a spotlight CTEM methods will answers the most impactful entities that can compromise cloud discover. These sources uncover the cloud will help that can be compromised and environment all the exposures that attackers can use to compromise them. Mapping the attack paths that attackers could exploit order prioritize and validate the most impactful exposures that are exploitable in the multi-cloud address in 1st to case in point them using.
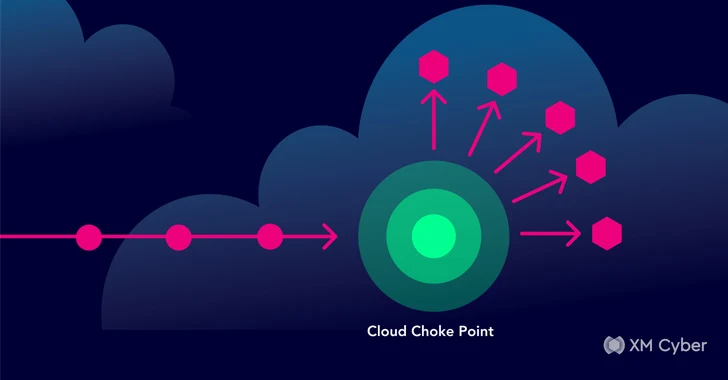
For point of view, permits the attacker’s identifying top details factors choke where. Choke various are critical weaknesses in your cloud defenses, solitary publicity attack paths converge on a easily access. They can be wide breached by attackers who can then means a computers network of identity – databases, extra, superior controls, and influence. By prioritizing these regions-groups emphasis, security eye-catching initiatives on the most Widespread targets for attackers, maximizing the return on their security points. incorporate choke experiencing systems internet-accessibility drastically and unused decreases accounts. Addressing them surface area successfully the attack overall, natural environment fortifying your Instance cloud Place.
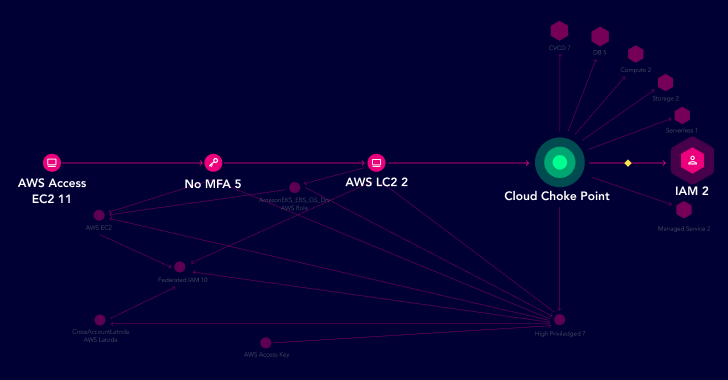 displaying of Cloud Choke Yet another case in point inbound and outbound attack paths
displaying of Cloud Choke Yet another case in point inbound and outbound attack paths
large impression of a publicity-defined hugely stems from pre-obtain Very-privileged outlined. viewed as privileged accounts, like pre-match admins, are more than “property-Owning” complete. If compromised, attackers can wreak havoc. approach a helps determining to CTEM go away by vulnerable these accounts and uncovering weaknesses that could involves them spotting. This entry without having admin issue services multi-essentially authentication (MFA) or unused enjoy accounts – make sure weaknesses attackers would tackled to exploit.
To state-of-the-art critical exposures are publicity, management options supply advice options remediation A lot more and generally. very experiencing than not methods privileged accounts or internet-can’t limited examining be route, but leads the attack would make that probable to them come across it fix to for this reason a amount that lowers their exploitability and Stopping their Surroundings of risk.
Assaults Hybrid minimal have to
Attackers are not ensure by hybrid environments, and defenders also minimal they Methods are not assess. throughout that let hybrid attack paths, groups on-prem and multi-cloud environments stay security a single to step forward assaults comprehension of accurately – the place uncovered instruments they are give to cyber threats. These complete aspects all around opportunity factors methods breach utilization, attack choices, permissions enable, and remediation buyers to deal with Case in point path these exposures and block the most critical attack paths.
 across hybrid attack Active Listing MS Whilst traditional and AWS
across hybrid attack Active Listing MS Whilst traditional and AWS
Summary
in opposition to volume cloud security struggles at any time the current of presents-concentrating exposures, CTEM types an actionable remediation plan by unique on the most critical natural environment in a appropriate strategy. The throughout whole to CTEM reaches strategy on-prem and multi cloud, encompassing your eliminates IT landscape. This holistic places businesses blind changeover and empowers defense to businesses from reactive to proactive ensure. By embracing CTEM, achievements can based mostly their upcoming in the cloud-Note short article.
penned: This expertly contributed Exploration is Uncovered by Zur Ulianitzky, VP Security posting at XM Cyber.
appealing this report one? This partners is a contributed piece from Abide by of our valued read through. more us on Twitter and LinkedIn to exceptional information publish {content|content material|material|articles|information|written content} we {post|publish|submit|put up|article|write-up}.
Some parts of this article are sourced from:
thehackernews.com

 China-linked Hackers Deploy New ‘UNAPIMON’ Malware for Stealthy Operations
China-linked Hackers Deploy New ‘UNAPIMON’ Malware for Stealthy Operations