A threat exercise cluster tracked as Earth Freybug has been observed utilizing a new malware named UNAPIMON to fly under the radar.
“Earth Freybug is a cyberthreat group that has been active considering that at the very least 2012 that focuses on espionage and monetarily determined functions,” Pattern Micro security researcher Christopher So mentioned in a report published today.
“It has been observed to focus on companies from different sectors across different nations around the world.”
The cybersecurity agency has described Earth Freybug as a subset within just APT41, a China-linked cyber espionage group that is also tracked as Axiom, Brass Storm (previously Barium), Bronze Atlas, HOODOO, Wicked Panda, and Winnti.

The adversarial collective is acknowledged to depend on a mixture of living-off-the-land binaries (LOLBins) and customized malware to know its plans. Also adopted are methods like dynamic-connection library (DLL) hijacking and application programming interface (API) unhooking.
Trend Micro claimed the activity shares tactical overlaps with a cluster formerly disclosed by cybersecurity organization Cybereason below the name Procedure Cuckoobees, which refers to an intellectual home theft marketing campaign focusing on technology and manufacturing corporations positioned in East Asia, Western Europe, and North The usa.
The setting up place of the attack chain is the use of a genuine executable involved with VMware Tools (“vmtoolsd.exe”) to generate a scheduled activity applying “schtasks.exe” and deploy a file named “cc.bat” in the distant machine.
It can be presently not known how the destructive code arrived to be injected in vmtoolsd.exe, though it really is suspected that it may perhaps have associated the exploitation of external-dealing with servers.
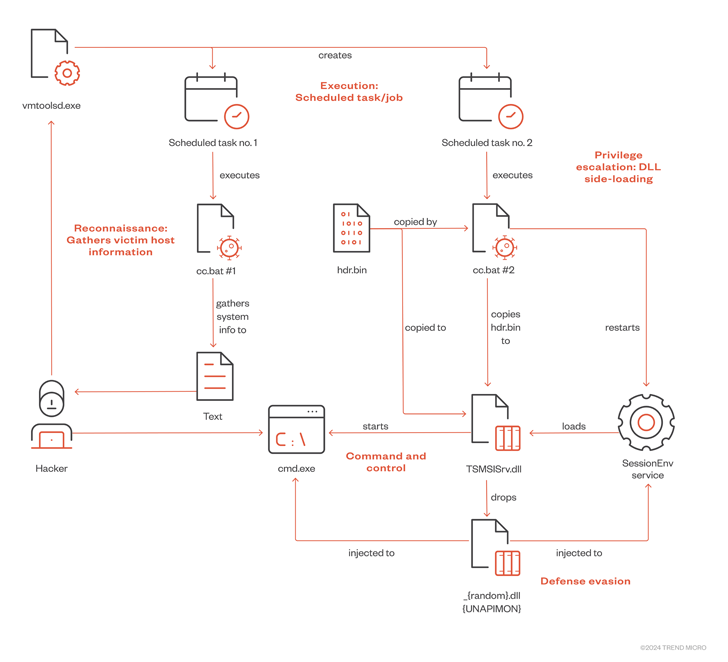
The batch script is built to amass technique facts and start a 2nd scheduled endeavor on the contaminated host, which, in change, executes a further batch file with the exact name (“cc.bat”) to in the end run the UNAPIMON malware.
“The 2nd cc.bat is notable for leveraging a service that hundreds a non-existent library to side-load a destructive DLL,” So defined. “In this circumstance, the provider is SessionEnv.”
This paves the way for the execution of TSMSISrv.DLL that’s liable for dropping a different DLL file (i.e., UNAPIMON) and injecting that similar DLL into cmd.exe. At the same time, the DLL file is also injected into SessionEnv for defense evasion.
On major of that, the Windows command interpreter is created to execute instructions coming from another equipment, primarily turning it into a backdoor.

A easy C++-based mostly malware, UNAPIMON is outfitted to stop youngster processes from currently being monitored by leveraging an open-source Microsoft library identified as Detours to unhook critical API functions, thus evading detection in sandbox environments that put into practice API monitoring as a result of hooking.
The cybersecurity corporation characterized the malware as unique, calling out the author’s “coding prowess and creative imagination” as very well as their use of an off-the-shelf library to have out destructive actions.
“Earth Freybug has been close to for rather some time, and their approaches have been witnessed to evolve through time,” Craze Micro stated.
“This attack also demonstrates that even easy procedures can be used proficiently when used effectively. Utilizing these strategies to an current attack pattern tends to make the attack more difficult to learn.”
Identified this article fascinating? Comply with us on Twitter and LinkedIn to study more exceptional material we article.
Some parts of this article are sourced from:
thehackernews.com


 Google to Delete Billions of Browsing Records in ‘Incognito Mode’ Privacy Lawsuit Settlement
Google to Delete Billions of Browsing Records in ‘Incognito Mode’ Privacy Lawsuit Settlement