The threat actors guiding the LockBit ransomware procedure have resurfaced on the dark web employing new infrastructure, times right after an global law enforcement exercise seized manage of its servers.
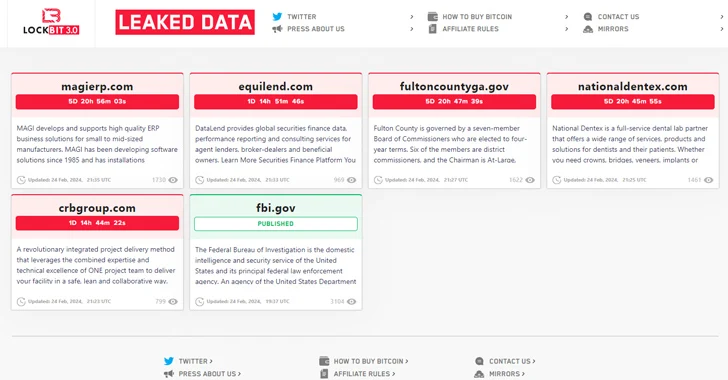
To that end, the infamous group has moved its details leak portal to a new .onion deal with on the TOR network, listing 12 new victims as of creating.
The administrator powering LockBit, in a lengthy abide by-up concept, explained some of their web-sites were being confiscated by most possible exploiting a critical PHP flaw tracked as CVE-2023-3824, acknowledging that they failed to update PHP due to “personalized carelessness and irresponsibility.”
“I understand that it may perhaps not have been this CVE, but a little something else like -working day for PHP, but I won’t be able to be 100% sure, due to the fact the model installed on my servers was presently regarded to have a recognized vulnerability, so this is most most likely how the victims’ admin and chat panel servers and the website server have been accessed,” they mentioned.

They also claimed the U.S. Federal Bureau of Investigation (FBI) “hacked” their infrastructure due to the fact of a ransomware attack on Fulton County in January and the “stolen files have a great deal of attention-grabbing items and Donald Trump’s court situations that could impact the upcoming U.S. election.”
They also termed for attacking the “.gov sector” extra generally, when also stating that the server from which the authorities acquired a lot more than 1,000 decryption keys held almost 20,000 decryptors, most of which were shielded and accounted for about 50 % of the whole quantity of decryptors generated since 2019.
The group even further went on to incorporate that the nicknames of the affiliate marketers have “nothing at all to do with their genuine nicknames on community forums and even nicknames in messengers.”
That is not all. The post also attempted to discredit law enforcement companies, boasting the authentic “Bassterlord” has not been recognized, and that the FBI steps are “aimed at destroying the name of my affiliate system.”
“Why did it take 4 days to get well? Mainly because I had to edit the resource code for the most up-to-date version of PHP, as there was incompatibility,” they claimed.
“I will cease being lazy and make it so that definitely each individual establish loker will be with utmost safety, now there will be no automated trial decrypt, all trial decrypts and the issuance of decryptors will be built only in guide manner. Thus in the probable subsequent attack, the FBI will not be equipped to get a one decryptor for no cost.”
Russia Arrests 3 SugarLocker Users
The growth will come as Russian legislation enforcement officials have arrested 3 folks, including Aleksandr Nenadkevichite Ermakov (aka blade_runner, GustaveDore, or JimJones), in link with the SugarLocker ransomware group.
“The attackers worked underneath the guise of a reputable IT agency Shtazi-IT, which provides providers for the enhancement of landing internet pages, cellular apps, scripts, parsers, and on-line stores,” Russian cybersecurity business F.A.C.C.T. claimed. “The organization openly posted ads for choosing new employees.”
The operators have also been accused of acquiring custom made malware, generating phishing internet sites for on the web shops, and driving person visitors to fraudulent strategies common in Russia and the Commonwealth of Impartial States (CIS) nations.
SugarLocker very first appeared in early 2021 and later began to be made available underneath the ransomware-as-a-service (RaaS) product, leasing its malware to other companions beneath an affiliate program to breach targets and deploy the ransomware payload.

Approximately a few-fourths of the ransom proceeds go to the affiliates, a figure that jumps to 90% if the payment exceeds $5 million. The cybercrime gang’s links to Shtazi-IT were earlier disclosed by Intel 471 final thirty day period.
The arrest of Ermakov is notable, as it comes in the wake of Australia, the U.K., and the U.S. imposing economical sanctions against him for his alleged purpose in the 2022 ransomware attack versus health and fitness insurance plan supplier Medibank.
The ransomware attack, which took area in late October 2022 and attributed to the now-defunct REvil ransomware crew, led to the unauthorized obtain of around 9.7 million of its recent and previous consumers.
The stolen data integrated names, dates of start, Medicare figures, and delicate clinical details, including data on mental wellbeing, sexual wellness, and drug use. Some of these documents also discovered their way to the dark web.
It also follows a report from information company TASS, which discovered that a 49-calendar year-previous Russian national is set to experience trial on expenses of carrying out a cyber attack on technological manage techniques that remaining 38 settlements of the Vologda with no energy.
Located this short article intriguing? Comply with us on Twitter and LinkedIn to read additional exceptional content material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Authorities Claim LockBit Admin “LockBitSupp” Has Engaged with Law Enforcement
Authorities Claim LockBit Admin “LockBitSupp” Has Engaged with Law Enforcement