LockBitSupp, the person(s) powering the persona symbolizing the LockBit ransomware provider on cybercrime boards this kind of as Exploit and XSS, “has engaged with regulation enforcement,” authorities mentioned.
The development will come next the takedown of the prolific ransomware-as-a-assistance (RaaS) procedure as aspect of a coordinated worldwide operation codenamed Cronos. Around 14,000 rogue accounts on 3rd-social gathering solutions like Mega, Protonmail, and Tutanota employed by the criminals have been shuttered.
“We know who he is. We know wherever he life. We know how a great deal he is worth. LockbitSupp has engaged with legislation enforcement,” according to a message posted on the now-seized (and offline) dark web info leak web-site.
The move has been interpreted by lengthy-term watchers of LockBit as an endeavor to generate suspicion and sow the seeds of distrust between affiliate marketers, ultimately undermining have confidence in in the team in the cybercrime ecosystem.
According to exploration published by Analyst1 in August 2023, there is evidence to advise that at the very least three different individuals have operated the “LockBit” and “LockBitSupp” accounts, a person of them becoming the gang’s leader alone.

On the other hand, talking to malware research group VX-Underground, LockBit mentioned “they did not consider legislation enforcement know his/her/their identities.” They also raised the bounty it made available to anybody who could concept them their actual names to $20 million. It truly is worthy of noting that the reward was greater from $1 million USD to $10 million late final month.
LockBit – also named Gold Mystic and Water Selkie – has experienced a number of iterations considering the fact that its inception in September 2019, namely LockBit Red, LockBit Black, and LockBit Eco-friendly, with the cybercrime syndicate also secretly creating a new edition termed LockBit-NG-Dev prior to its infrastructure currently being dismantled.
“LockBit-NG-Dev is now penned in .NET and compiled utilizing CoreRT,” Pattern Micro stated. “When deployed along with the .NET ecosystem, this allows the code to be a lot more platform-agnostic. It eliminated the self-propagating abilities and the means to print ransom notes by using the user’s printers.”
One particular of the notable additions is the inclusion of a validity interval, which proceeds its procedure only if the latest date is within just a unique date vary, suggesting tries on the aspect of the builders to stop the reuse of the malware as well as resist automated analysis.
Perform on the next era variant is mentioned to have been spurred by a range of logistical, complex, and reputational issues, prominently pushed by the leak of the ransomware builder by a disgruntled developer in September 2022 and also misgivings that one particular of its administrators may perhaps have been changed by govt agents.
It also did not help that the LockBit-managed accounts have been banned from Exploit and XSS towards the conclude of January 2024 for failing to shell out an preliminary entry broker who provided them with accessibility.
“The actor arrived across as a person who was ‘too significant to fail’ and even confirmed disdain to the arbitrator who would make the choice on the final result of the claim,” Pattern Micro claimed. “This discourse demonstrated that LockBitSupp is possible utilizing their status to carry much more fat when negotiating payment for entry or the share of ransom payouts with affiliate marketers.”
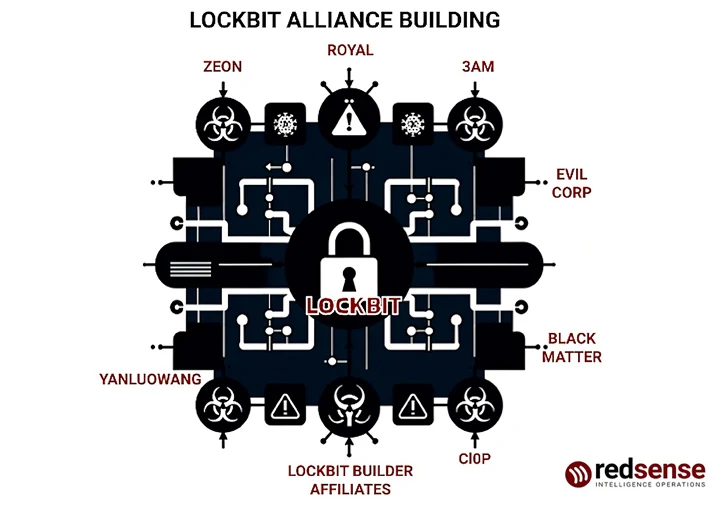
PRODAFT, in its have analysis of the LockBit operation, explained it discovered about 28 affiliate marketers, some of whom share ties with other Russian e-criminal offense groups like Evil Corp, FIN7, and Wizard Spider (aka TrickBot).
These connections are also evidenced by the fact that the gang operated as a “nesting doll” with three unique levels, providing an outward perception of an founded RaaS scheme compromising dozens of affiliates although stealthily borrowing hugely qualified pen testers from other ransomware groups by forging private alliances.

The smokescreen materialized in the type of what is referred to as a Ghost Team product, in accordance to RedSense researchers Yelisey Bohuslavskiy and Marley Smith, with LockBitSupp serving “as a mere distraction for genuine operations.”
“A Ghost Group is a group that has incredibly high capabilities but transfers them to a different manufacturer by allowing the other team to outsource functions to them,” they claimed. “The clearest edition of this is Zeon, who has been outsourcing their abilities to LockBit and Akira.”
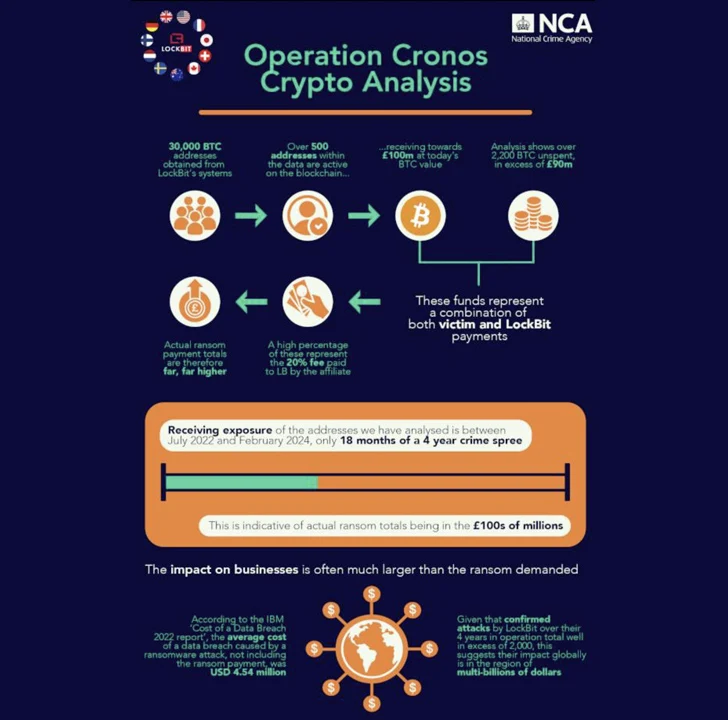
The team is estimated to have made extra than $120 million in illicit revenue in its multi-year operate, rising as the most lively ransomware actor in record.
“Presented that verified assaults by LockBit in excess of their four several years in procedure overall perfectly over 2,000, this suggests that their effects globally is in the area of multi-billions of bucks,” the U.K. Nationwide Crime Agency (NCA) claimed.
Useless to say, Operation Cronos has probable induced irreparable injury to the criminal outfit’s ability to keep on with ransomware pursuits, at minimum underneath its present manufacturer.
“The rebuilding of the infrastructure is pretty not likely LockBit’s management is really technically incapable,” RedSense explained. “Men and women to whom they delegated their infrastructural growth have very long still left LockBit, as observed by the primitivism of their infra.”
“[Initial access brokers], which ended up the key resource of LockBit’s venture, will not trust their entry to a team immediately after a takedown, as they want their accessibility to be turned into hard cash.”
Observed this report interesting? Abide by us on Twitter and LinkedIn to read through additional exclusive articles we post.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Expands Free Logging Capabilities for all U.S. Federal Agencies
Microsoft Expands Free Logging Capabilities for all U.S. Federal Agencies