Cybersecurity scientists are warning about a spike in email phishing strategies that are weaponizing the Google Cloud Run assistance to deliver different banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban (aka Javali) to targets throughout Latin The united states (LATAM) and Europe.
“The infection chains involved with these malware households attribute the use of malicious Microsoft Installers (MSIs) that operate as droppers or downloaders for the remaining malware payload(s),” Cisco Talos scientists disclosed past 7 days.
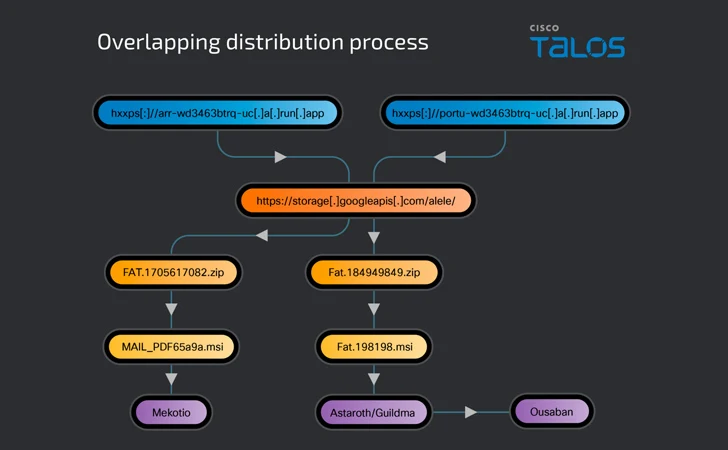
The large-volume malware distribution strategies, noticed given that September 2023, have employed the exact storage bucket inside of Google Cloud for propagation, suggesting opportunity inbound links amongst the menace actors at the rear of the distribution campaigns.
Google Cloud Operate is a managed compute system that allows users to operate frontend and backend companies, batch jobs, deploy internet sites and applications, and queue processing workloads without getting to handle or scale the infrastructure.
“Adversaries may watch Google Cloud Operate as an low-cost, yet helpful way to deploy distribution infrastructure on platforms that most businesses most likely do not prevent internal techniques from accessing,” the scientists mentioned.
A bulk of the devices employed to mail phishing messages originate from Brazil, followed by the U.S., Russia, Mexico, Argentina, Ecuador, South Africa, France, Spain, and Bangladesh. The emails bear themes linked to invoices or economic and tax paperwork, in some conditions purporting to be from nearby govt tax organizations.

Embedded within just these messages are links to a web site hosted on operate[.]app, resulting in the shipping of a ZIP archive containing a destructive MSI file both specifically or by using 302 redirects to a Google Cloud Storage spot, where the installer is stored.
The danger actors have also been noticed making an attempt to evade detection making use of geofencing methods by redirecting readers to these URLs to a legit internet site like Google when accessing them with a U.S. IP deal with.
Aside from leveraging the identical infrastructure to deliver both equally Mekotio and Astaroth, the infection chain involved with the latter acts as a conduit to distribute Ousaban.
Astaroth, Mekotio, and Ousaban are all created to single out money establishments, trying to keep tabs on users’ web browsing activity as effectively as logging keystrokes and getting screenshots ought to a person of the focus on bank web sites be open.
Ousaban has a record of weaponizing cloud providers to its gain, acquiring formerly used Amazon S3 and Microsoft Azure to download second-phase payloads, and Google Docs to retrieve command-and-control (C2) configuration.
The development comes amid phishing strategies propagating malware families these kinds of as DCRat, Remcos RAT, and DarkVNC that are able of harvesting delicate knowledge and using manage of compromised hosts.
It also follows an uptick in threat actors deploying QR codes in phishing and email-dependent assaults (aka quishing) to trick prospective victims into setting up malware on their mobile gadgets.
“In a individual attack, the adversaries despatched targets spear-phishing emails with destructive QR codes pointing to bogus Microsoft Workplace 365 login webpages that eventually steal the user’s login credentials when entered,” Talos mentioned.
“QR code assaults are significantly hazardous for the reason that they transfer the attack vector off a safeguarded laptop or computer and onto the target’s own cell unit, which typically has less security protections in area and in the long run has the sensitive info that attackers are immediately after.”
Phishing campaigns have also established their eyes on the oil and gasoline sector to deploy an details stealer known as Rhadamanthys, which has at this time arrived at edition .6., highlighting a constant stream of patches and updates by its builders.
“The marketing campaign begins with a phishing email utilizing a car or truck incident report to entice victims into interacting with an embedded hyperlink that abuses an open redirect on a legitimate area, primarily Google Maps or Google Photos,” Cofense reported.

Buyers who click on the link are then redirected to a web-site hosting a bogus PDF file, which, in actuality, is a clickable image that contacts a GitHub repository and downloads a ZIP archive containing the stealer executable.
“At the time a victim attempts to interact with the executable, the malware will unpack and begin a link with a command-and-command (C2) area that collects any stolen qualifications, cryptocurrency wallets, or other delicate information and facts,” the company additional.
Other campaigns have abused email promoting resources like Twilio’s SendGrid to get hold of consumer mailing lists and acquire benefit of stolen credentials to mail out convincing-looking phishing emails, for every Kaspersky.
“What will make this campaign specifically insidious is that the phishing e-mail bypass common security steps,” the Russian cybersecurity company pointed out. “Considering the fact that they are sent by a respectable service and have no evident symptoms of phishing, they may well evade detection by automated filters.”
These phishing routines are additional fueled by the simple availability of phishing kits these kinds of as Greatness and Tycoon, which have turn out to be a value-productive and scalable implies for aspiring cyber criminals to mount destructive strategies.
“Tycoon Group [phishing-as-a-service] is bought and promoted on Telegram for as small as $120,” Trustwave SpiderLabs researcher Rodel Mendrez explained final week, noting the company first arrived into getting close to August 2023.
“Its vital marketing options involve the capability to bypass Microsoft two-issue authentication, attain ‘link pace at the maximum amount,’ and leveraging Cloudflare to evade antibot actions, guaranteeing the persistence of undetected phishing backlinks.”
Identified this report appealing? Abide by us on Twitter and LinkedIn to study a lot more distinctive articles we article.
Some parts of this article are sourced from:
thehackernews.com

 LockBit Ransomware Group Resurfaces After Law Enforcement Takedown
LockBit Ransomware Group Resurfaces After Law Enforcement Takedown