Phishing assaults are steadily getting to be far more advanced, with cybercriminals investing in new methods of deceiving victims into revealing sensitive details or putting in destructive software. One particular of the most recent developments in phishing is the use of QR codes, CAPTCHAs, and steganography. See how they are carried out and learn to detect them.
Quishing
Quishing, a phishing procedure resulting from the mixture of “QR” and “phishing,” has turn into a preferred weapon for cybercriminals in 2023.
By concealing malicious back links within QR codes, attackers can evade standard spam filters, which are mainly geared toward pinpointing textual content-based phishing tries. The incapability of several security applications to decipher the information of QR codes more will make this technique a go-to option for cybercriminals.
 An email made up of a QR code with a destructive url
An email made up of a QR code with a destructive url
Examining a QR code with an embedded malicious website link in a protected setting is effortless with ANY.Operate:
The sandbox will then quickly start a new undertaking window, enabling you to evaluate the URL identified within the QR code.
Black Friday OfferTake benefit of ANY.RUN’s Black Friday Supply
Invest in an once-a-year Searcher or Hunter plan subscription and get a further for your colleague completely absolutely free of demand. Readily available November 20-26.
Get It Now
CAPTCHA-based assaults
CAPTCHA is a security resolution used on web sites to avert automated bots from producing pretend accounts or distributing spam. Attackers have managed to exploit this instrument to their advantage.
 A phishing attack CAPTCHA site demonstrated in the ANY.Operate sandbox
A phishing attack CAPTCHA site demonstrated in the ANY.Operate sandbox
Attackers are ever more working with CAPTCHAs to mask credential-harvesting kinds on fake internet websites. By producing hundreds of area names making use of a Randomized Domain Produced Algorithm (RDGA) and implementing CloudFlare’s CAPTCHAs, they can efficiently hide these kinds from automatic security devices, these as web crawlers, which are not able to bypass the CAPTCHAs.
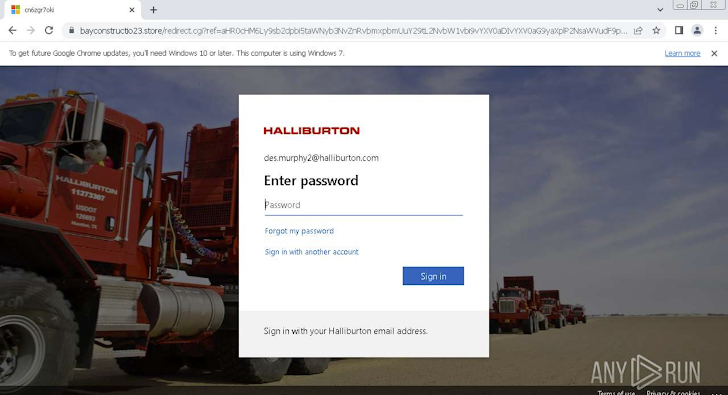 A pretend Halliburton login site
A pretend Halliburton login site
The instance higher than reveals an attack targeting Halliburton Corporation workers. It initial demands the user to go a CAPTCHA verify and then employs a practical Workplace 365 non-public login web site that is complicated to distinguish from the authentic page.
The moment the victim enters their login credentials, they are redirected to a respectable web page, although the attackers exfiltrate the credentials to their Command-and-Management server.
Discover much more about CAPTCHA assaults in this article.
Steganography malware strategies
Steganography is the exercise of hiding information within distinct media, this kind of as pictures, movies, or other data files.
A regular phishing attack that employs steganography starts with a meticulously crafted email built to seem legit. Embedded in just the email is an attachment, usually a Word document, accompanied by a hyperlink to a file-sharing system like Dropbox. In the instance below, you can see a phony email from a Colombian federal government corporation.
 A phishing email is typically the initially phase of an attack
A phishing email is typically the initially phase of an attack
The unsuspecting consumer that clicks the connection inside of the document downloads an archive, which consists of a VBS script file. Upon execution, the script retrieves an impression file, seemingly harmless but containing concealed destructive code. Once executed, the malware infects the victim’s technique.
To understand how steganography attacks are carried out and detected, look at out this article.
Expose phishing attacks with ANY.Run
ANY.Run is a malware investigation sandbox that is able of detecting a extensive variety of phishing tactics and allowing people look at them in detail.
Check out ANY.RUN’s Black Friday Offer, obtainable November 20-26.

The sandbox features:
- Totally interactive Windows 7,9,10,11 digital machines
- Extensive studies with IOCs and malware configs
- Non-public examination of an limitless variety of data files and links
Discovered this post attention-grabbing? Stick to us on Twitter and LinkedIn to browse a lot more distinctive material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Kinsing Hackers Exploit Apache ActiveMQ Vulnerability to Deploy Linux Rootkits
Kinsing Hackers Exploit Apache ActiveMQ Vulnerability to Deploy Linux Rootkits