New study has unveiled that threat actors are abusing Cloudflare Tunnels to set up covert conversation channels from compromised hosts and keep persistent obtain.
“Cloudflared is functionally incredibly similar to ngrok,” Nic Finn, a senior risk intelligence analyst at GuidePoint Security, stated. “Even so, Cloudflared differs from ngrok in that it provides a whole lot much more usability for absolutely free, together with the potential to host TCP connectivity in excess of cloudflared.”
A command-line resource for Cloudflare Tunnel, cloudflared makes it possible for consumers to make safe connections amongst an origin web server and Cloudflare’s closest information heart so as to conceal the web server IP addresses as effectively as block volumetric distributed denial-of-services (DDoS) and brute-pressure login attacks.

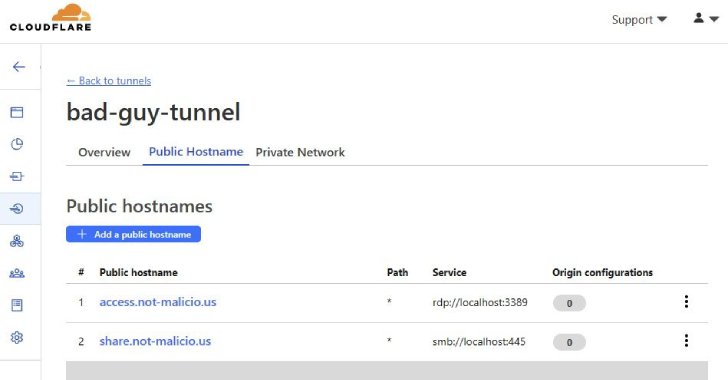
For a menace actor with elevated access on an contaminated host, this function presents a lucrative tactic to established up a foothold by producing a token essential to set up the tunnel from the victim equipment.
“The tunnel updates as shortly as the configuration adjust is produced in the Cloudflare Dashboard, enabling TAs to empower features only when they want to carry out routines on the victim equipment, then disable features to avert publicity of their infrastructure,” Finn spelled out.
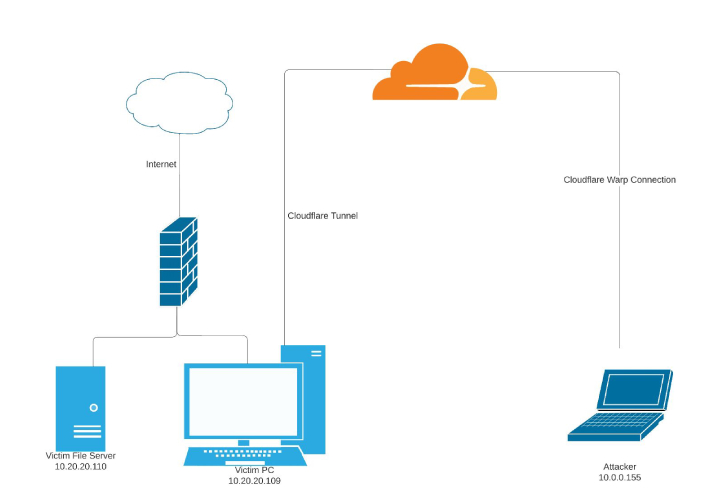
“For example, the TA could help RDP connectivity, collect facts from the target equipment, then disable RDP right up until the next working day, as a result decreasing the likelihood of detection or the potential to observe the domain used to establish the connection.”
Even extra troublingly, the adversary could get advantage of the tunnel’s Private Networks operation to stealthily access an selection of IP addresses (i.e., endpoints inside of a nearby network) as if they were “physically collocated with the sufferer equipment hosting the tunnel.”

That reported, the method has presently uncovered takers in the wild. Previously this yr, Phylum and Kroll detailed two diverse software program source chain assaults concentrating on the Python Package Index (PyPI) repository in which fraudulent offers were being noticed downloading cloudflared to remotely access the endpoint by means of a Flask web application.
“Companies applying Cloudflare solutions legitimately could perhaps limit their expert services to certain knowledge facilities and generate detections for targeted traffic like Cloudflared tunnels that route to any where besides their specified data centers,” Finn mentioned. “This method might assist in the detection of unauthorized tunnels.”
To recognize doable misuse of cloudflared, it is really encouraged that corporations implement suitable logging mechanisms to watch for anomalous instructions, DNS queries, and outbound connections, together with blocking makes an attempt to down load the executable.
Found this post exciting? Adhere to us on Twitter and LinkedIn to browse far more exclusive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Understanding Active Directory Attack Paths to Improve Security
Understanding Active Directory Attack Paths to Improve Security