The operators linked with the QakBot (aka QBot) malware have set up 15 new command-and-management (C2) servers as of late June 2023.
The findings are a continuation of the malware’s infrastructure analysis from Workforce Cymru, and arrive a minor in excess of two months right after Lumen Black Lotus Labs discovered that 25% of its C2 servers are only energetic for a solitary day.
“QakBot has a heritage of taking an extended split each and every summer time ahead of returning someday in September, with this year’s spamming functions ceasing all around 22 June 2023,” the cybersecurity firm stated.
“But are the QakBot operators really on trip when they usually are not spamming, or is this ‘break’ a time for them to refine and update their infrastructure and resources?”

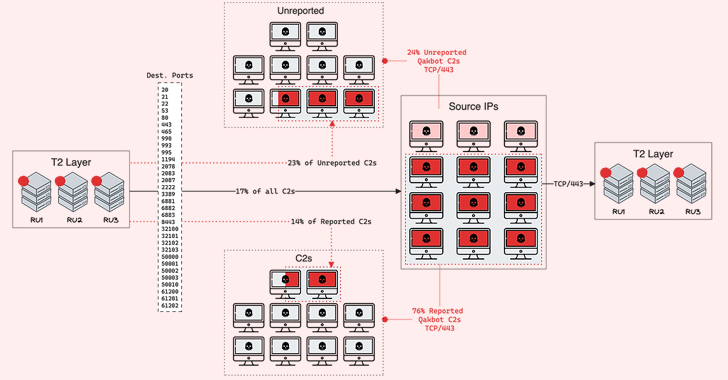
QakBot’s C2 network, like in the scenario of Emotet and IcedID, is characterised by a tiered architecture in which C2 nodes connect with upstream Tier 2 (T2) C2 nodes hosted on VPS vendors geolocated in Russia.
A majority of the bot C2 servers, which connect with the target hosts, are situated in India and the U.S. Place IP addresses determined from outbound T2 connections are principally based in the U.S., India, Mexico, and Venezuela.
Also present along with the C2s and the Tier 2 C2s is a BackConnect (BC) server that turns the contaminated bots into a proxy for other malicious purposes.

The most recent exploration from Workforce Cymru reveals that the selection of existing C2s speaking with the T2 layer has drastically lessened, with only eight remaining, in section driven by Black Lotus Labs’ null-routing of the greater-tier infrastructure in May 2023.
“We notice that on June 2, U.S. C2s all but disappeared, and targeted visitors from Indian C2s substantially reduced,” the business claimed, attributing the deficiency of U.S. exercise to null-routing the T2 layer.

Outdoors of the 15 C2 servers, 6 C2 servers active because prior to June and two C2 servers that came alive in June have continued to show action in July soon after spamming concluded.
A further investigation of NetFlow info exhibits a sample whereby “circumstances of increased outbound T2 connections often happen following spikes in exercise for inbound bot C2 connections” and “spikes in outbound T2 connections commonly correspond with a decline in bot C2 activity.”
“In elevating victims to be made use of as C2 infrastructure with T2 communication, QakBot proficiently punishes consumers twice, first in the original compromise, and 2nd in the prospective risk to status of a host being discovered publicly as destructive,” Group Cymru stated.
By chopping off communications to the upstream servers, the corporation pointed out, victims are prevented from getting C2 directions, thereby properly safeguarding recent and future buyers from compromise.
Identified this article attention-grabbing? Comply with us on Twitter and LinkedIn to examine extra special content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Hackers Abusing Cloudflare Tunnels for Covert Communications
Hackers Abusing Cloudflare Tunnels for Covert Communications