Launched in 1999, Microsoft Energetic Listing is the default identification and access management services in Windows networks, dependable for assigning and imposing security guidelines for all network endpoints. With it, people can obtain numerous assets across networks. As factors tend to do, moments, they are a’changin’ – and a number of yrs back, Microsoft introduced Azure Lively Directory, the cloud-based edition of Advert to prolong the Advertisement paradigm, giving businesses with an Identity-as-a-Assistance (IDaaS) resolution throughout both of those the cloud and on-prem applications. (Note that as of July 11th 2023, this assistance was renamed to Microsoft Entra ID, but for the sake of simplicity, we will refer to it as Azure Ad in this publish)
Each Energetic Listing and Azure Ad are critical to the operating of on-prem, cloud-based, and hybrid ecosystems, taking part in a key job in uptime and small business continuity. And with 90% of corporations working with the services for staff authentication, obtain handle and ID management, it has grow to be the keys to the proverbial castle.
Energetic Directory, Actively Problematic
But as central as it is, Energetic Directory security posture is frequently woefully lacking.
Let us just take a brief peek at how Lively Directory assigns consumers, which will drop some gentle on why this software has some shall we say, issues, linked with it.
At the main, what Energetic Directory does is establish groups that have roles and authorizations linked with them. End users are assigned a username and password, which is then connected to their Active Directory Account Object. Making use of Light-weight Directory Obtain Protocol, passwords are verified as right or incorrect and the usergroup is also confirmed. In typical, end users are assigned to the Domain Consumer group and will be granted access to the objects that domain people have authorization to entry. Then there are Admins – these are users assigned to the Domain Admins team. This group is very privileged and is so licensed to accomplish any steps in the network.
With these kinds of potentially powerful capabilities, it is really super critical to be certain that Active Directory is managed and configured optimally. Issues like skipped patches, lousy access administration and misconfigurations can allow attackers to accessibility even the most delicate systems, which can have dire consequences.
In 2022, our in-house exploration discovered that 73% of the top rated attack methods applied in the compromising of critical property included mismanaged or stolen credentials – and additional than 50 % of the attacks in businesses consist of some factor of Lively Listing compromise. And as soon as they have a foothold in Lively Listing, attackers can conduct hundreds of various destructive steps like:
- Hiding exercise in the network
- Executing destructive code
- Elevating privileges
- Having into the cloud setting to compromise critical property
Point is, if you really don’t know what is actually going on in your Lively Listing, and if you’re missing the appropriate processes and security controls, you might be very likely leaving the doorway large open up to attackers.
.e book-specifics padding: 20px .book-impression img border-radius: 5px .xm_container screen: flex align-objects: heart margin: 20px 10px 30px qualifications: #f9fbff colour: #160755 padding: 20px border: 2px strong #d9deff border-radius: 10px textual content-align: remaining box-shadow: 5px 5px #e2ebff -webkit-border-top rated-remaining-radius: 15px -moz-border-radius-topleft: 15px -webkit-border-bottom-proper-radius: 15px -moz-border-radius-bottomright: 15px .e book-graphic flex: 250pxmargin-right: 20px .e book-specifics flex: 1 .e-book-aspects ul margin: 15px .ebook-facts ul li margin-base: 5px @media (max-width: 600px) .xm_container flex-way: column .ebook-impression margin-ideal: margin-base: 20px

Down load our hottest exploration report, and learn
- How a lot of methods it normally takes for attackers to ordinarily compromise your critical belongings
- Top rated exposures and cleanliness issues that kind attack paths
- Important findings similar to attacks across hybrid, on-prem or multi-cloud networks.
Energetic Directory Attack Paths
From an attacker’s POV, Active Directory serves as a excellent option for conducting lateral motion, as getting that first access lets them to go from a minimal-privileged person to a additional beneficial target – or even to thoroughly just take over – by exploiting misconfigurations or overly too much permissions.
So now let’s choose a look into the anatomy of 3 real Lively Directory attack paths and see how attackers created their way by this ecosystem.
In this article is an attack route we arrived throughout in one of our customer’s ecosystem:
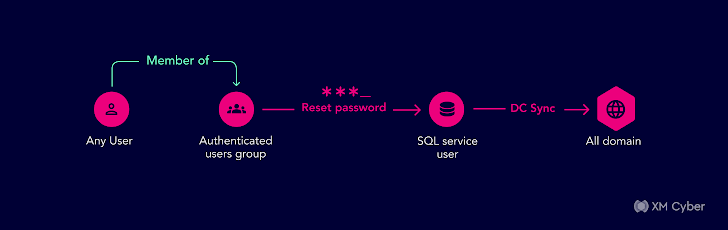
The firm was deeply dedicated to hardening their security posture but Lively Directory was a blind spot. In this situation, all authenticated consumers – basically any people at all – in the area experienced been unintentionally granted the suitable to reset passwords. So if an attacker took in excess of one Active Directory consumer by means of phishing or other social engineering methods, they could then reset any passwords for other buyers and consider over any account in the area.At the time they noticed this, they last but not least comprehended their Active Directory security strategy desired to amount-up so they locked down and hardened their security procedures.
Here’s another one particular from one of our customer’s Energetic Listing

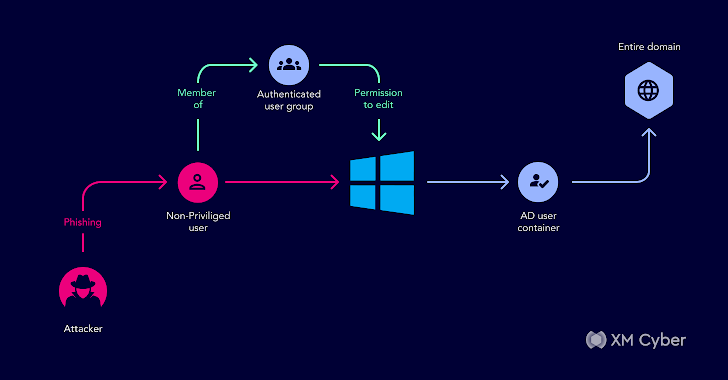
We uncovered an attack path working with the authenticated users group with permissions to modify the GPO policy’s gPCFileSysPath to a path with malicious insurance policies.
One particular of the influenced objects was the Advert Person Container, with a child item that was a consumer which was portion of the Area Admin group. Any consumer in the domain could get Domain Admin permissions — all they wanted was a single non-privileged consumer to slide prey to a phishing email to compromise the overall domain. This could have led to a comprehensive compromise of their area.
Prepared for 1 extra? Right here it is:
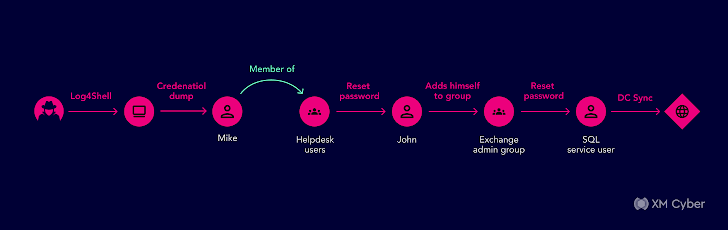
This a person commences with an attacker infiltrating an company ecosystem by using phishing mail that when opened, executed code employing a vulnerability on an unpatched machine. The upcoming move exploited the compromised Energetic Directory user’s neighborhood and area credentials by way of credential dumping approaches. The attacker then had the permissions to insert on their own to a team so they could include the compromised Active Directory person to an Energetic Listing helpdesk team.
The helpdesk team had the Energetic Directory permissions to reset other end users passwords and at this phase, the attacker could reset a password to a further person, ideally an aged, out of use admin. Now that they have been an admin, they could execute a lot of hazardous routines in the network, these kinds of as managing malicious code by including a script logon to other people in Active Listing.
These are just some comparatively straightforward approaches attackers make their way across Active Listing environments. By understanding these actual true-planet attack paths, companies can begin to see what their Active Listing and Advert Azure environments search like from the attacker’s place of look at.

Check out on-desire How To Conquer Energetic Directory Exploits And Avoid Attacks to understand:
- How Energetic Listing (Ad) exposures combined with other attack procedures type attack paths
- What type of steps the attacker can accomplish once they compromise an Advertisement person
- What to do for greater Active Listing Security
Conclusion
Hunting at attack paths can enable shore up these possibly tough environments. By having a detailed perspective of the attack paths that exist in Lively Listing across on-prem and cloud environments, businesses can understand how attackers shift laterally with a context-primarily based knowing of their setting – offering them visibility into how issues can incorporate to aid assaults and impersonate end users, escalate privileges, and acquire obtain to cloud environments.
With this comprehending, organizations can prioritize what really wants correcting and harden environments to stop Lively Directory weaknesses from becoming leveraged by risk actors.
Located this article attention-grabbing? Comply with us on Twitter and LinkedIn to browse a lot more distinctive articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 New Yashma Ransomware Variant Targets Multiple English-Speaking Countries
New Yashma Ransomware Variant Targets Multiple English-Speaking Countries