Google on Thursday announced an increased version of Secure Browsing to deliver true-time, privacy-preserving URL protection and safeguard customers from visiting most likely destructive sites.
“The Typical security method for Chrome on desktop and iOS will check out sites from Google’s server-aspect record of known negative internet sites in genuine-time,” Google’s Jonathan Li and Jasika Bawa said.
“If we suspect a site poses a risk to you or your machine, you’ll see a warning with far more data. By checking internet sites in true time, we be expecting to block 25% more phishing makes an attempt.”
Up until finally now, the Chrome browser applied a locally-stored listing of known unsafe web-sites which is current each individual 30 to 60 minutes, and then leveraging a hash-primarily based method to examine each internet site visited versus the databases.

Google initially discovered its plans to change to serious-time server-side checks without having sharing users’ searching heritage with the business in September 2023.
The purpose for the modify, the search large explained, is determined by the truth that the checklist of destructive internet websites is expanding at a speedy rate and that 60% of the phishing domains exist for less than 10 minutes, producing it difficult to block.
“Not all products have the methods needed to retain this rising listing, nor are they normally capable to acquire and apply updates to the checklist at the frequency vital to reward from whole protection,” it extra.
Consequently, with the new architecture, every time a person makes an attempt to go to a web-site, the URL is checked against the browser’s world-wide and community caches containing recognized risk-free URLs and the results of past Safe and sound Browsing checks in purchase to decide the site’s status.
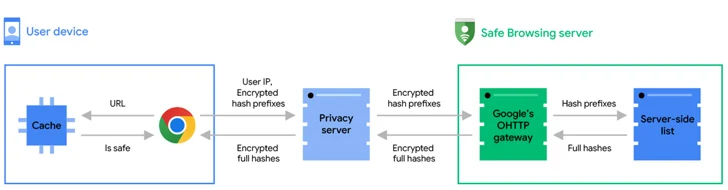
Need to the visited URL be absent from the caches, a serious-time verify is carried out by obfuscating the URL into 32-byte whole hashes, which are then truncated into 4-byte very long hash prefixes, encrypted, and sent to a privacy server.
“The privateness server gets rid of prospective consumer identifiers and forwards the encrypted hash prefixes to the Risk-free Browsing server by means of a TLS relationship that mixes requests with lots of other Chrome customers,” Google explained.
The Safe Searching server subsequently decrypts the hash prefixes and matches them towards the server-aspect databases to return entire hashes of all unsafe URLs that match one particular of the hash prefixes despatched by the browser.

Ultimately, on the shopper side, the entire hashes are as opposed towards the comprehensive hashes of the frequented URL, and a warning concept is exhibited if a match is observed.
Google also verified that the privateness server is nothing but an Oblivious HTTP (OHTTP) relay operated by Fastly that sits between Chrome and the Secure Browsing server to avoid the latter from accessibility users’ IP addresses, thus protecting against it from correlating the URL checks with a user’s internet browsing background.
“Ultimately, Risk-free Searching sees the hash prefixes of your URL but not your IP address, and the privateness server sees your IP tackle but not the hash prefixes,” the company emphasised. “No one bash has accessibility to both of those your id and the hash prefixes. As this sort of, your searching action remains non-public.”
Uncovered this post appealing? Comply with us on Twitter and LinkedIn to examine more exceptional written content we article.
Some parts of this article are sourced from:
thehackernews.com


 Malicious Ads Targeting Chinese Users with Fake Notepad++ and VNote Installers
Malicious Ads Targeting Chinese Users with Fake Notepad++ and VNote Installers