Chinese end users searching for reputable software package this kind of as Notepad++ and VNote on search engines like Baidu are becoming focused with malicious ads and bogus back links to distribute trojanized variations of the software package and finally deploy Geacon, a Golang-based implementation of Cobalt Strike.
“The destructive site discovered in the notepad++ search is dispersed as a result of an advertisement block,” Kaspersky researcher Sergey Puzan stated.
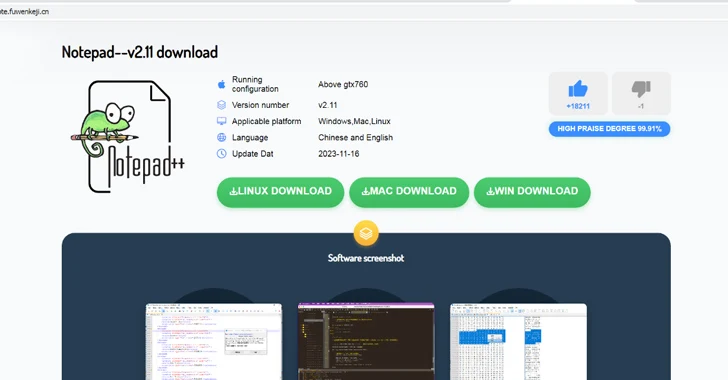
“Opening it, an attentive person will right away detect an amusing inconsistency: the website address is made up of the line vnote, the title features a down load of Notepad‐‐ (an analog of Notepad++, also dispersed as open up-supply computer software), when the image proudly demonstrates Notepad++. In fact, the packages downloaded from here contain Notepad‐‐.”

The site, named vnote.fuwenkeji[.]cn, consists of obtain back links to Windows, Linux, and macOS versions of the application, with the website link to the Windows variant pointing to the official Gitee repository made up of the Notepad– installer (“Notepad–v2.10.-plugin-Installer.exe”).
The Linux and macOS variations, on the other hand, guide to malicious installation deals hosted on vnote-1321786806.cos.ap-hongkong.myqcloud[.]com.
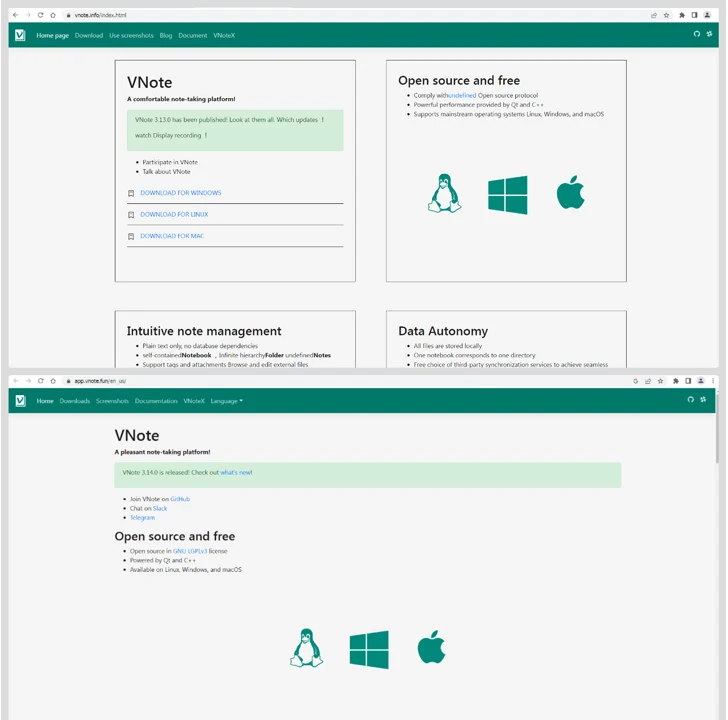
In a equivalent trend, the fake search-alike internet sites for VNote (“vnote[.]information” and “vnotepad[.]com”) lead to the similar set of myqcloud[.]com one-way links, in this case, also pointing to a Windows installer hosted on the domain. That stated, the back links to the probably malicious versions of VNote are no longer energetic.
An evaluation of the modified Notepad– installers reveals that they are developed to retrieve a up coming-stage payload from a distant server, a backdoor that reveals similarities with Geacon.

It can be capable of generating SSH connections, doing file operations, enumerating procedures, accessing clipboard articles, executing files, uploading and downloading files, taking screenshots, and even moving into into slumber mode. Command-and-command (C2) is facilitated by means of HTTPS protocol.
The enhancement arrives as malvertising strategies have also acted as a conduit for other malware such as FakeBat (aka EugenLoader) malware with the assistance of MSIX installer information masquerading as Microsoft OneNote, Idea, and Trello.
Found this posting exciting? Stick to us on Twitter and LinkedIn to read through far more special material we put up.
Some parts of this article are sourced from:
thehackernews.com

 LockBit Ransomware Hacker Ordered to Pay $860,000 After Guilty Plea in Canada
LockBit Ransomware Hacker Ordered to Pay $860,000 After Guilty Plea in Canada