Google has declared guidance for what is known as a V8 Sandbox in the Chrome web browser in an effort to handle memory corruption issues.
The sandbox, according to V8 Security complex direct Samuel Groß, aims to avoid “memory corruption in V8 from spreading inside the host method.”
The lookup behemoth has explained V8 Sandbox as a lightweight, in-process sandbox for the JavaScript and WebAssembly motor that is built to mitigate typical V8 vulnerabilities.
The plan is to limit the effect of V8 vulnerabilities by limiting the code executed by V8 to a subset of the process’ digital address place (“the sandbox”) and isolating it from the relaxation of the system.

Shortcomings affecting V8 have accounted for a major chunk of the zero-day vulnerabilities that Google has dealt with among 2021 and 2023, with as quite a few as 16 security flaws uncovered above the time interval.
“The sandbox assumes that an attacker can arbitrarily and concurrently modify any memory within the sandbox handle space as this primitive can be built from normal V8 vulnerabilities,” the Chromium workforce said.
“Even further, it is assumed that an attacker will be equipped to go through memory outside the house of the sandbox, for illustration, by way of hardware side channels. The sandbox then aims to guard the rest of the approach from these kinds of an attacker. As this kind of, any corruption of memory exterior of the sandbox address room is thought of a sandbox violation.”
Groß emphasised the challenges with tackling V8 vulnerabilities by switching to a memory-protected language like Rust or components memory security approaches, this kind of as memory tagging, supplied the “delicate logic issues” that can be exploited to corrupt memory, compared with vintage memory security bugs like use-following-frees, out-of-bounds accesses, and others.
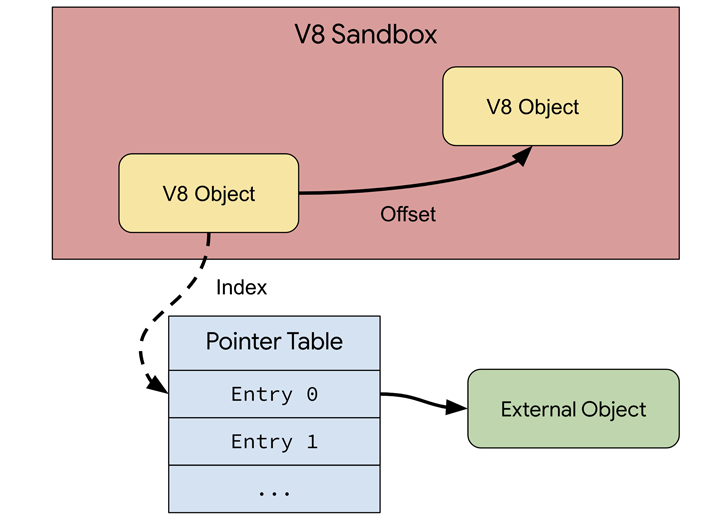
“Just about all vulnerabilities discovered and exploited in V8 today have a single issue in prevalent: the eventual memory corruption essentially happens inside the V8 heap simply because the compiler and runtime (pretty much) exclusively run on V8 HeapObject scenarios,” Groß said.
Given that these issues are unable to be guarded by the very same procedures utilized for standard memory-corruption vulnerabilities, the V8 Sandbox is made to isolate V8’s heap memory these kinds of that must any memory corruption manifest, it are unable to escape the security confines to other parts of the process’ memory.
This is achieved by replacing all information styles that can obtain out-of-sandbox memory with “sandbox-suitable” choices, therefore successfully avoiding an attacker from accessing other memory. The sandbox can be enabled by environment “v8_enable_sandbox” to real in the gn args.
Benchmark results from Speedometer and JetStream demonstrate that the security characteristic adds an overhead of about 1% on normal workloads, permitting it to be enabled by default starting up with Chrome variation 123, spanning Android, ChromeOS, Linux, macOS, and Windows.
“The V8 Sandbox involves a 64-bit process as it wants to reserve a massive volume of virtual handle house, at the moment one terabyte,” Groß reported.

“The sandbox is inspired by the fact that current memory protection systems are largely inapplicable to optimizing JavaScript engines. When these systems fail to reduce memory corruption in V8 itself, they can in point defend the V8 Sandbox attack surface area. The sandbox is hence a vital move to memory safety.”
The growth arrives as Google highlighted the part by Kernel Deal with Sanitizer (KASan) in detecting memory bugs in native code and support harden Android firmware security, adding it utilized the compiler-centered instrument for discovering additional than 40 bugs.
“Utilizing KASan enabled builds for the duration of testing and/or fuzzing can enable capture memory corruption vulnerabilities and steadiness issues just before they land on user units,” Eugene Rodionov and Ivan Lozano from the Android crew stated.
Observed this report appealing? Observe us on Twitter and LinkedIn to read far more exceptional material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Watch Out for ‘Latrodectus’ – This Malware Could Be In Your Inbox
Watch Out for ‘Latrodectus’ – This Malware Could Be In Your Inbox