Threat hunters have found a new malware named Latrodectus that has been dispersed as part of email phishing strategies given that at least late November 2023.
“Latrodectus is an up-and-coming downloader with many sandbox evasion operation,” scientists from Proofpoint and Crew Cymru claimed in a joint investigation released last week, including it is really built to retrieve payloads and execute arbitrary commands.
There is evidence to recommend that the malware is very likely prepared by the identical danger actors powering the IcedID malware, with the downloader set to use by preliminary access brokers (IABs) to aid the deployment of other malware.
Latrodectus has been principally joined to two distinct IABs tracked by Proofpoint under the names TA577 (aka H2o Curupira) and TA578, the previous of which has also been linked to the distribution of QakBot and PikaBot.
As of mid-January 2024, it is really been employed almost solely by TA578 in email risk strategies, in some instances delivered by way of a DanaBot an infection.

TA578, recognised to be energetic because at least May perhaps 2020, has been joined to email-based mostly strategies offering Ursnif, IcedID, KPOT Stealer, Buer Loader, BazaLoader, Cobalt Strike, and Bumblebee.
Attack chains leverage get hold of sorts on web sites to deliver authorized threats relating to alleged copyright infringement to specific corporations. The hyperlinks embedded in the messages immediate the recipients to a bogus web site to trick them into downloading a JavaScript file which is responsible for launching the primary payload working with msiexec.
“Latrodectus will post encrypted technique facts to the command-and-control server (C2) and request the obtain of the bot,” the scientists stated. “When the bot registers with the C2, it sends requests for commands from the C2.”
It also will come with capabilities to detect if it truly is functioning in a sandboxed atmosphere by checking if the host has a valid MAC tackle and there are at the very least 75 managing procedures on techniques operating Windows 10 or newer.
Like in the scenario of IcedID, Latrodectus is intended to ship the registration facts in a Post request to the C2 server wherever the fields are HTTP parameters stringed jointly and encrypted, right after which it awaits more instructions from the server.
The instructions permit the malware to enumerate data files and procedures, execute binaries and DLL documents, run arbitrary directives through cmd.exe, update the bot, and even shut down a jogging process.

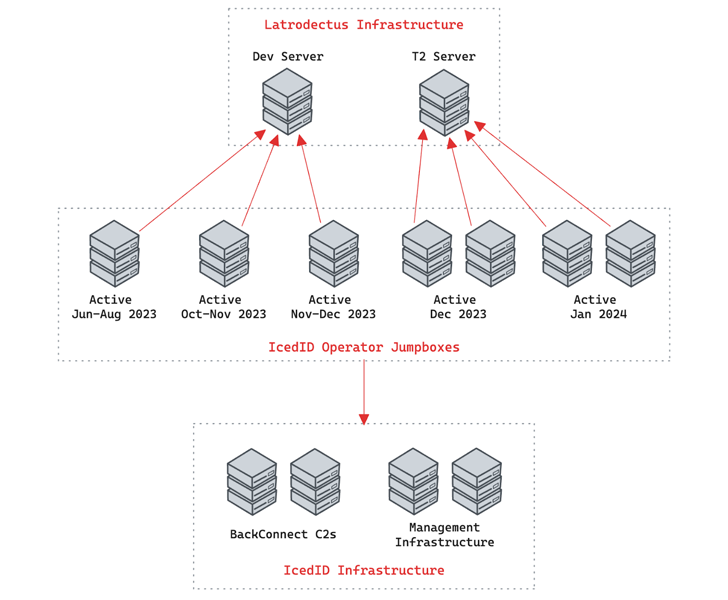
A even further evaluation of the attacker infrastructure reveals that the initial C2 servers came alive on September 18, 2023. These servers, in change, are configured to converse with an upstream Tier 2 server that was set up around August 2023.
Latrodectus’ connections to IcedID stems from the truth that the T2 server “maintains connections with backend infrastructure related with IcedID” and use of bounce packing containers previously related with IcedID operations.
“Latrodectus will come to be progressively applied by fiscally motivated threat actors across the criminal landscape, especially people who earlier distributed IcedID,” Crew Cymru assessed.
Located this write-up attention-grabbing? Abide by us on Twitter and LinkedIn to study more special content we article.
Some parts of this article are sourced from:
thehackernews.com


 The Drop in Ransomware Attacks in 2024 and What it Means
The Drop in Ransomware Attacks in 2024 and What it Means