Risk actors are actively scanning and exploiting a pair of security flaws that are claimed to affect as quite a few as 92,000 internet-exposed D-Hyperlink network-hooked up storage (NAS) units.
Tracked as CVE-2024-3272 (CVSS score: 9.8) and CVE-2024-3273 (CVSS score: 7.3), the vulnerabilities effects legacy D-Link products and solutions that have achieved finish-of-lifestyle (EoL) status. D-Hyperlink, in an advisory, explained it does not plan to ship a patch and in its place urges shoppers to change them.
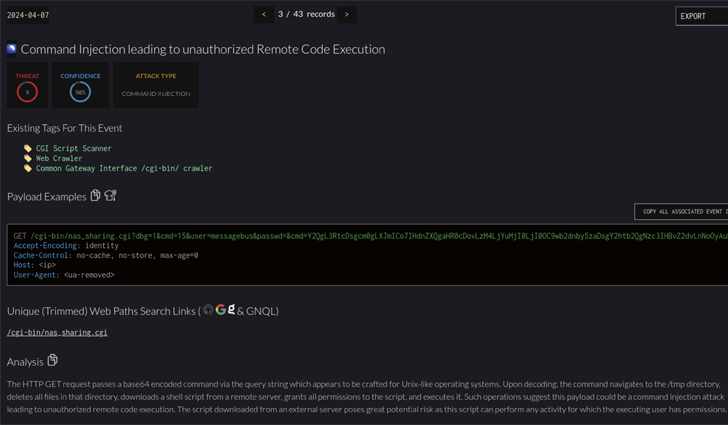
“The vulnerability lies in the nas_sharing.cgi uri, which is susceptible because of to two principal issues: a backdoor facilitated by difficult-coded qualifications, and a command injection vulnerability by means of the system parameter,” security researcher who goes by the name netsecfish said in late March 2024.

Prosperous exploitation of the flaws could guide to arbitrary command execution on the impacted D-Url NAS devices, granting danger actors the means to accessibility sensitive data, alter technique configurations, or even trigger a denial-of-services (DoS) ailment.
The issues impact the next models –
- DNS-320L
- DNS-325
- DNS-327L, and
- DNS-340L
Danger intelligence business GreyNoise reported it observed attackers making an attempt to weaponize the flaws to deliver the Mirai botnet malware, hence generating it attainable to remotely commandeer the D-Connection units.
In the absence of a resolve, the Shadowserver Basis is recommending that customers possibly just take these units offline or have remote obtain to the appliance firewalled to mitigate opportunity threats.

The conclusions once once again illustrate that Mirai botnets are continuously adapting and incorporating new vulnerabilities into their repertoire, with risk actors quickly producing new variants that are created to abuse these issues to breach as several equipment as doable.
With network products turning out to be frequent targets for fiscally enthusiastic and nation-condition-linked attackers, the growth comes as Palo Alto Networks Device 42 unveiled that menace actors are ever more switching to malware-initiated scanning attacks to flag vulnerabilities in focus on networks.
“Some scanning assaults originate from benign networks probably driven by malware on contaminated devices,” the enterprise claimed.
“By launching scanning assaults from compromised hosts, attackers can execute the following: Covering their traces, bypassing geofencing, increasing botnets, [and] leveraging the methods of these compromised gadgets to make a better quantity of scanning requests in comparison to what they could attain using only their very own units.”
Observed this posting attention-grabbing? Abide by us on Twitter and LinkedIn to browse more distinctive information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Google Chrome Adds V8 Sandbox – A New Defense Against Browser Attacks
Google Chrome Adds V8 Sandbox – A New Defense Against Browser Attacks