The menace actors behind RedLine and Vidar details stealers have been noticed pivoting to ransomware by way of phishing campaigns that spread initial payloads signed with Prolonged Validation (EV) code signing certificates.
“This suggests that the risk actors are streamlining functions by creating their techniques multipurpose,” Craze Micro scientists reported in a new evaluation printed this 7 days.
In the incident investigated by the cybersecurity company, an unnamed target is explained to have 1st obtained a piece of facts stealer malware with EV code signing certificates, followed by ransomware employing the identical shipping and delivery procedure.
In the past, QakBot bacterial infections have leveraged samples signed with legitimate code signing certificates to bypass security protections.
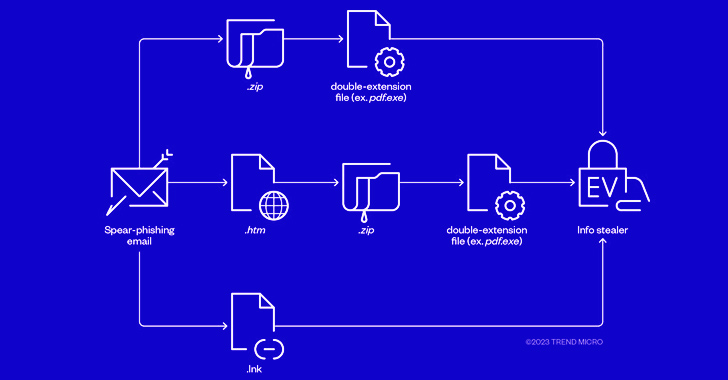
The attacks start off with phishing e-mail that utilize well-worn lures to trick victims into jogging destructive attachments that masquerade as PDF or JPG illustrations or photos but are in fact executables that leap-begin the compromise upon working.

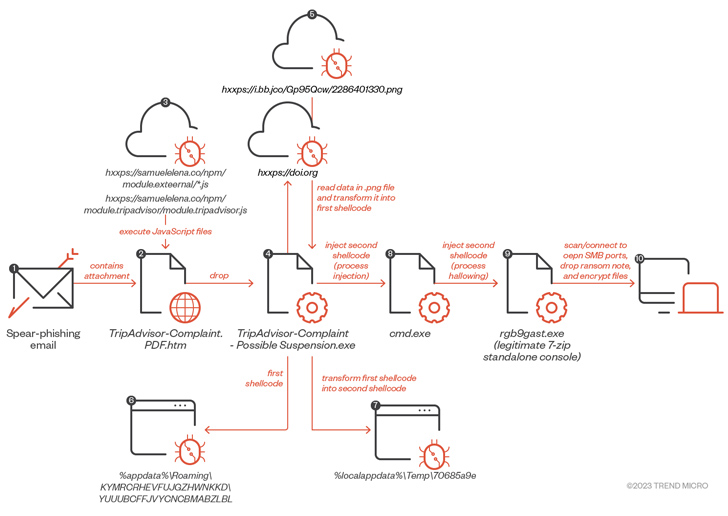
When the campaign targeting the target shipped stealer malware in July, a ransomware payload built its way in early August right after getting an email concept that contains a bogus TripAdvisor grievance email attachment (“TripAdvisor-Grievance.pdf.htm”), triggering a sequence of measures that culminated in the deployment of ransomware.
“At this issue, it is truly worth noting that compared with the samples of the data stealer we investigated, the documents utilised to fall the ransomware payload did not have EV certificates,” the scientists stated.
“Having said that, the two originate from the exact same menace actor and are spread using the very same supply system. We can thus assume a division of labor between the payload company and the operators.”
The improvement will come as IBM X-Pressure discovered new phishing strategies spreading an enhanced model of a malware loader named DBatLoader, which was employed as a conduit to distribute FormBook and Remcos RAR before this yr.
DBatLoader’s new capabilities aid UAC bypass, persistence, and procedure injection, indicating that it really is staying actively taken care of to fall destructive plans that can accumulate delicate data and help remote handle of techniques.
The latest established of assaults, detected due to the fact late June, are engineered to also deliver commodity malware this sort of as Agent Tesla and Warzone RAT. A bulk of the email messages have singled out English speakers, although email messages in Spanish and Turkish have also been spotted.
“In numerous observed strategies the menace actors leveraged ample control in excess of the email infrastructure to empower destructive emails to go SPF, DKIM, and DMARC email authentication methods,” the organization stated.
“A vast majority of campaigns leveraged OneDrive to phase and retrieve extra payloads, with a smaller fraction otherwise making use of transfer[.]sh or new/compromised domains.”
Approaching WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Modern-day Age
Dive deep into the potential of SaaS security with Maor Bin, CEO of Adaptive Protect. Find out why identification is the new endpoint. Safe your location now.
Supercharge Your Capabilities
In connected information, Malwarebytes uncovered that a new malvertising marketing campaign is concentrating on end users who are seeking for Cisco’s Webex video conferencing program on search engines like Google to redirect them to a faux web site that propagates the BATLOADER malware.
BATLOADER, for its element, establishes contact with a distant server to down load a next-phase encrypted payload, which is an additional regarded stealer and keylogger malware referred to as DanaBot.
A novel approach adopted by the menace actor is the use of monitoring template URLs as a filtering and redirection system to fingerprint and figure out prospective victims of fascination. Site visitors who really don’t fulfill the criteria (e.g., requests originating from a sandboxed surroundings) are directed to the genuine Webex internet site.
“Due to the fact the advertisements search so genuine, there is small doubt individuals will simply click on them and take a look at unsafe websites,” Jérôme Segura, director of risk intelligence at Malwarebytes, mentioned.
“The variety of software package getting utilized in these adverts point out that menace actors are interested in corporate victims that will give them with credentials handy for even further network ‘pentesting’ and, in some circumstances, ransomware deployment.”
Identified this posting intriguing? Observe us on Twitter and LinkedIn to go through extra exclusive articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 Iranian Nation-State Actors Employ Password Spray Attacks Targeting Multiple Sectors
Iranian Nation-State Actors Employ Password Spray Attacks Targeting Multiple Sectors