Iranian country-point out actors have been conducting password spray attacks towards countless numbers of companies globally between February and July 2023, new results from Microsoft expose.
The tech big, which is monitoring the activity underneath the name Peach Sandstorm (formerly Holmium), said the adversary pursued companies in the satellite, protection, and pharmaceutical sectors to probably facilitate intelligence assortment in assistance of Iranian condition passions.
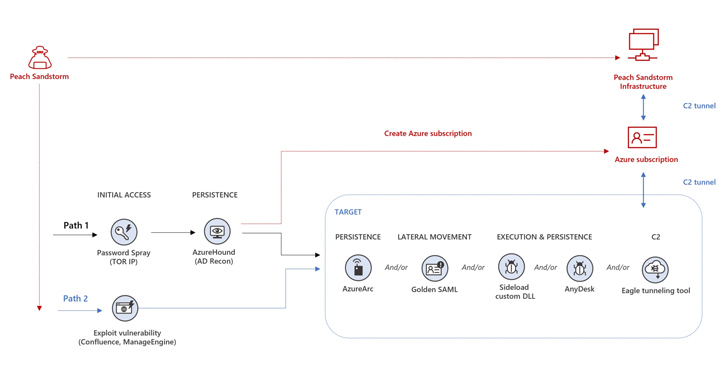
Must the authentication to an account be effective, the menace actor has been noticed employing a mix of publicly accessible and customized instruments for discovery, persistence, and lateral motion, followed by info exfiltration in constrained cases.
Peach Sandstorm, also recognized by the names APT33, Elfin, and Refined Kitten, has been connected to spear-phishing assaults from aerospace and electricity sectors in the earlier, some of which have entailed the use of the SHAPESHIFT wiper malware. It really is mentioned to be lively due to the fact at minimum 2013.

“In the first stage of this campaign, Peach Sandstorm conducted password spray strategies towards countless numbers of businesses across many sectors and geographies,” the Microsoft Risk Intelligence workforce claimed, noting some of the activity is opportunistic.
Password spraying refers to a strategy whereby a destructive actor tries to authenticate to quite a few diverse accounts utilizing a single password or a listing of generally-applied passwords. It can be unique from brute-power attacks in which a solitary account is specific with lots of credential combos.
“Action noticed in this marketing campaign aligned with an Iranian sample of daily life, notably in late May perhaps and June, where activity transpired practically exclusively concerning 9:00 AM and 5:00 PM Iran Regular Time (IRST),” Microsoft further more included.
Intrusions are characterized by the use of open up-source crimson workforce tools these kinds of as AzureHound, a Golang binary to perform reconnaissance, and ROADtools to obtain information in a target’s cloud ecosystem. The assaults additional have been observed using Azure Arc to establish persistence by connecting to an Azure membership managed by the threat actor.
Alternate attack chains mounted by Peach Sandstorm have entailed the exploitation of security flaws in Atlassian Confluence (CVE-2022-26134) or Zoho ManageEngine (CVE-2022-47966) to obtain preliminary entry.
Future WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Modern day Age
Dive deep into the future of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why id is the new endpoint. Protected your spot now.
Supercharge Your Competencies
Some other noteworthy elements of the put up-compromise activity problem the deployment of AnyDesk distant monitoring and management instrument to maintain entry, EagleRelay to tunnel website traffic back to their infrastructure, and leveraging Golden SAML attack methods for lateral movement.
“Peach Sandstorm also designed new Azure subscriptions and leveraged the access these subscriptions offered to conduct extra attacks in other organizations’ environments,” Microsoft said.
“As Peach Sandstorm increasingly develops and employs new capabilities, companies need to establish corresponding defenses to harden their attack surfaces and raise prices for these attacks.”
Identified this article exciting? Abide by us on Twitter and LinkedIn to read extra special articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Microsoft Uncovers Flaws in ncurses Library Affecting Linux and macOS Systems
Microsoft Uncovers Flaws in ncurses Library Affecting Linux and macOS Systems