Critical security flaws have been disclosed in the Open Authorization (OAuth) implementation of preferred on line companies such as Grammarly, Vidio, and Bukalapak, setting up upon previous shortcomings uncovered in Booking[.]com and Expo.
The weaknesses, now tackled by the respective companies subsequent dependable disclosure amongst February and April 2023, could have authorized malicious actors to obtain obtain tokens and likely hijack consumer accounts.
OAuth is a conventional that’s usually utilised as a system for cross-application accessibility, granting websites or apps access to their information on other websites, these as Fb, but without supplying them the passwords.

“When OAuth is used to give support authentication, any security breach in it can lead to identity theft, fiscal fraud, and entry to many personalized data such as credit rating card figures, private messages, health and fitness documents, and far more, dependent on the specific assistance getting attacked,” Salt Security researcher Aviad Carmel reported.
The issue discovered in Vidio stems from an absence of token verification, meaning an attacker can use an entry token produced for an additional App ID, a random identifier designed by Fb for each and every software or website that receives registered in its developer portal.
In a opportunity attack scenario, a danger actor could produce a rogue website that delivers a sign-in choice by Facebook to collect the access tokens and subsequently use them from Vidio.com (which has the Application ID 92356), thus making it possible for whole account takeover.
The API security company reported it also identified a comparable issue with token verification on Bukalapak.com by way of Facebook login that could consequence in unauthorized account entry.

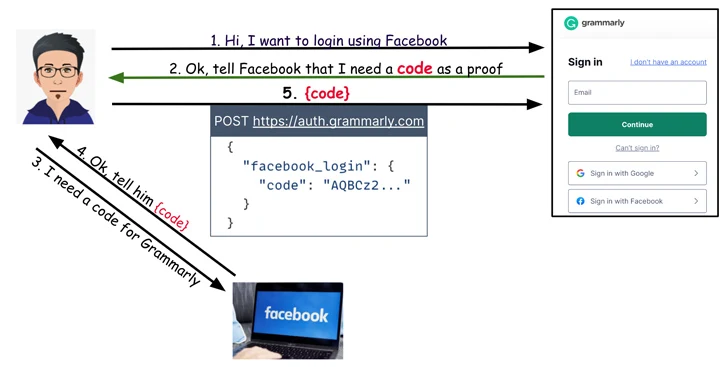
On Grammarly, it emerged that when buyers endeavor to login to their accounts applying the “Indicator in with Facebook” option, an HTTP Publish request is despatched to auth.grammarly[.]com to authenticate them employing a top secret code.
As a final result, even though Grammarly is not inclined to a token reuse attack like in the situation of Vidio and Bukalapak, it is even so vulnerable to a distinctive sort of trouble wherein the Article request can be altered to substitute the magic formula code with an access token acquired from the aforementioned destructive web site to acquire access to the account.
“And like with the other websites, the Grammarly implementation did not conduct token verification,” Carmel reported, including, “an account takeover would give an attacker access to the victim’s saved files.”
Uncovered this short article appealing? Follow us on Twitter and LinkedIn to read through a lot more unique material we submit.
Some parts of this article are sourced from:
thehackernews.com


 The Rise of S3 Ransomware: How to Identify and Combat It
The Rise of S3 Ransomware: How to Identify and Combat It