In today’s electronic landscape, all around 60% of corporate knowledge now resides in the cloud, with Amazon S3 standing as the backbone of info storage for quite a few significant corporations.
Despite S3 remaining a protected services from a dependable service provider, its pivotal part in managing vast amounts of sensitive data (buyer individual details, economic information, intellectual residence, and many others.), supplies a juicy focus on for threat actors. It remains susceptible to ransomware attacks which are generally initiated utilizing leaked entry keys that have unintentionally been uncovered by human mistake and have accessibility to the organization’s buckets.
To correctly overcome these evolving threats, it is crucial to make sure that your group has visibility into your S3 setting, that you are informed of how danger actors can compromise facts for ransom and most importantly, greatest techniques for minimizing the risk of cyber criminals properly executing this kind of an attack.
Guaranteeing Visibility: CloudTrail and Server Access Logs
Visibility serves as the basis for any productive detection technique. In Amazon S3, virtually each individual motion interprets to an API get in touch with, which are meticulously recorded in CloudTrail and documented in AWS documentation.
The two most important possibilities for logging activity in S3 buckets — CloudTrail Info Occasions and Server Accessibility Logs — keep a prosperity of info that security practitioners need to leverage to foresee and detect suspicious exercise. Each and every give distinctive benefits and trade-offs:
- Cloud Path Knowledge Situations: provide visibility into resource operations carried out on or in just a resource in genuine-time, but comes with likely cost implications thanks to significant API get in touch with volumes
- Server Accessibility Logs: free accessibility to records for each request made to your S3 bucket, but occur with potential delays in log availability and possible logging with fewer integrity.
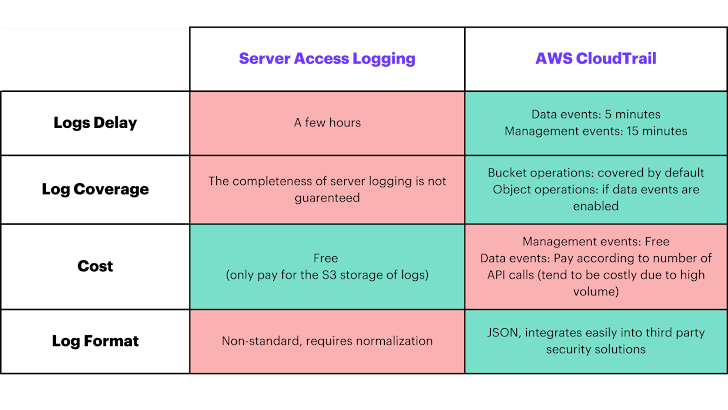 The pros and trade-offs amongst Server Access Logs and AWS CloudTrial logs.
The pros and trade-offs amongst Server Access Logs and AWS CloudTrial logs.
Mitigating Risk by Understanding the Attack Situations
Making use of the higher than logs to be certain suitable visibility, it is feasible to maintain an eye out for potential attack scenarios in get to mitigate risks successfully. There are a few principal attack scenarios that we notice with S3 ransomware assaults, all which can avoid an corporation from accessing its info. Beneath are the attack scenarios, together with back links to looking queries that the professional danger hunting crew from Hunters’ Workforce Axon has shared publicly that allow for everyone to search for these attack eventualities in their individual environments:
*Observe: Object Encryption and Object Deletion – Delete Functions call for enabling Cloudtrail Information Gatherings for the ideal buckets.
Each individual situation poses sizeable disruptions, probably blocking companies from accessing critical facts. By delving into the required permissions, attacker views, and detection solutions for every situation, organizations can proactively put together for probable threats.
Security and Very best Tactics
Being familiar with the attack eventualities will help to supply context for how to carry out proactive actions to significantly decrease the attack surface area. There are numerous things that can be completed to improve the security of S3 buckets from the risk of ransomware.
- Use IAM roles for shorter-time period credentials: avoid making use of static IAM access keys. If you are working with IAM users, be certain to enable Multi-Variable Authentication (MFA) for them.
- Abide by the principle of least privilege: this makes sure that users and roles only possess the permissions required for their jobs. Moreover, make the most of bucket insurance policies to limit entry to these critical assets.
- Allow S3 Versioning: this means retaining report of every single version of each and every object stored in your bucket in its place of right modifying it. This is extremely helpful towards unauthorized override or deletions.
- Enable S3 Object Lock: functioning on a create-the moment, read through-several (WORM) product, means that your data simply cannot be deleted by everyone (the details is “locked”) which safeguards versus modifications for described time periods.
- Established up AWS Backup/Bucket Replication: this can be any sort of backup that is separate in location and obtain manage from your genuine bucket.
- Apply server-aspect encryption with AWS KMS keys: this delivers your organization with precise handle about who can obtain bucket objects. This provides still a further level of safety towards who can encrypt and decrypt objects in your bucket.
Summary
As details volumes carry on to surge, securing Amazon S3 is paramount in safeguarding hundreds of thousands of companies in opposition to ransomware attacks and evolving cyber threats.
Prioritizing threats, making sure visibility as a result of CloudTrail and Server Access Logs, and applying proactive steps are essential measures in mitigating risk. By adopting these techniques, organizations can fortify their S3 buckets’ protection and make certain the integrity and security of their critical facts.
For a more in depth breakdown of typical attack scenarios and ideal practices, examine out a online video deep dive from Group Axon. Staff Axon is the qualified menace looking arm of the well-liked SIEM substitute Hunters, and features rapid response to emerging cyber threats, on-demand from customers cyber experience and proactive menace looking across customers’ environments. Follow Team Axon on X for timely updates on rising cyber threats and premiere cyber content.
More S3 Means:
- AWS Shopper Playbook (GitHub)
- Incident Response Workshop for S3 ransomware (AWS)
Located this write-up attention-grabbing? Follow us on Twitter and LinkedIn to study additional special content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Act Now: VMware Releases Patch for Critical vCenter Server RCE Vulnerability
Act Now: VMware Releases Patch for Critical vCenter Server RCE Vulnerability