A beforehand undocumented Chinese-speaking danger actor codenamed SneakyChef has been connected to an espionage marketing campaign principally focusing on govt entities throughout Asia and EMEA (Europe, Middle East, and Africa) with SugarGh0st malware since at minimum August 2023.
“SneakyChef makes use of lures that are scanned documents of government companies, most of which are related to various countries’ Ministries of Foreign Affairs or embassies,” Cisco Talos researchers Chetan Raghuprasad and Ashley Shen claimed in an analysis printed these days.
Functions similar to the hacking crew were very first highlighted by the cybersecurity organization in late November 2023 in relationship with an attack campaign that singled out South Korea and Uzbekistan with a tailor made variant of Gh0st RAT identified as SugarGh0st.
A subsequent evaluation from Proofpoint final month uncovered the use of SugarGh0st RAT from U.S. companies involved in synthetic intelligence endeavours, including those in academia, private marketplace, and governing administration support. It really is tracking the cluster underneath the identify UNK_SweetSpecter.

Talos reported that it has considering the fact that observed the very same malware currently being used to very likely concentrate on many govt entities throughout Angola, India, Latvia, Saudi Arabia, and Turkmenistan based on the lure paperwork made use of in the spear-phishing strategies, indicating a widening of the scope of the countries focused.
In addition to leveraging attack chains that make use of Windows Shortcut (LNK) information embedded inside of RAR archives to deliver SugarGh0st, the new wave has been identified to employ a self-extracting RAR archive (SFX) as an preliminary infection vector to start a Visible Basic Script (VBS) that eventually executes the malware by usually means of a loader even though at the same time displaying the decoy file.
The assaults in opposition to Angola are also noteworthy for the truth that it utilizes a new remote accessibility trojan codenamed SpiceRAT working with lures from Neytralny Turkmenistan, a Russian-language newspaper in Turkmenistan.
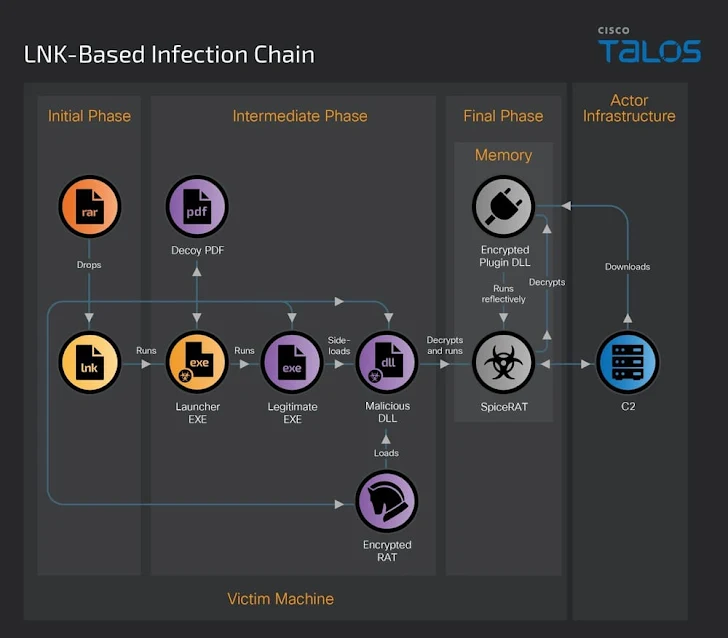
SpiceRAT, for its component, employs two different infection chains for propagation, a person of which uses an LNK file present inside of a RAR archive that deploys the malware working with DLL aspect-loading techniques.
“When the target extracts the RAR file, it drops the LNK and a concealed folder on their device,” the researchers reported. “Right after a victim opens the shortcut file, which masqueraded as a PDF document, it executes an embedded command to operate the malicious launcher executable from the dropped hidden folder.”

The launcher then proceeds to show the decoy document to the victim and run a legit binary (“dxcap.exe”), which subsequently sideloads a destructive DLL accountable for loading SpiceRAT.
The 2nd variant entails the use of an HTML Application (HTA) that drops a Windows batch script and a Base64-encoded downloader binary, with the former launching the executable by implies of a scheduled activity each and every five minutes.
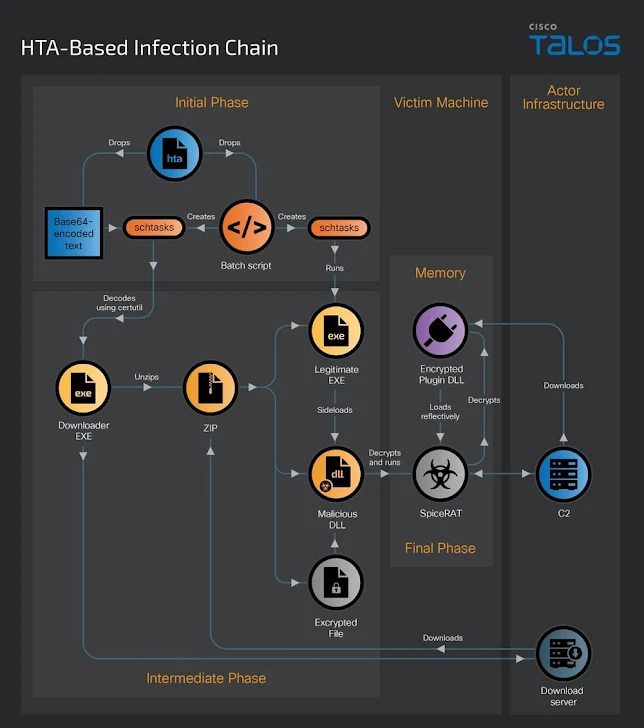
The batch script is also engineered to operate another genuine executable “ChromeDriver.exe” just about every 10 minutes, which then sideloads a rogue DLL that, in switch, hundreds SpiceRAT. Each and every of these elements – ChromeDriver.exe, the DLL, and the RAT payload – are extracted from a ZIP archive retrieved by the downloader binary from a remote server.
SpiceRAT also can take edge of the DLL aspect-loading method to start a DLL loader, which captures the checklist of jogging processes to test if it is staying debugged, followed by managing the major module from memory.
“With the ability to download and run executable binaries and arbitrary commands, SpiceRAT appreciably increases the attack area on the victim’s network, paving the way for even further attacks,” Talos explained.
Observed this article attention-grabbing? Adhere to us on Twitter and LinkedIn to read much more unique content material we article.
Some parts of this article are sourced from:
thehackernews.com


 Military-themed Email Scam Spreads Malware to Infect Pakistani Users
Military-themed Email Scam Spreads Malware to Infect Pakistani Users