A earlier undocumented China-aligned threat actor has been joined to a established of adversary-in-the-middle (AitM) assaults that hijack update requests from reputable software to deliver a complex implant named NSPX30.
Slovak cybersecurity company ESET is tracking the innovative persistent menace (APT) group less than the title Blackwood. It truly is stated to be lively due to the fact at the very least 2018.
The NSPX30 implant has been noticed deployed by using the update mechanisms of recognised software program these as Tencent QQ, WPS Office, and Sogou Pinyin, with the attacks focusing on Chinese and Japanese producing, buying and selling, and engineering corporations as very well as individuals found in China, Japan, and the U.K.
“NSPX30 is a multistage implant that features numerous components this kind of as a dropper, an installer, loaders, an orchestrator, and a backdoor,” security researcher Facundo Muñoz mentioned. “Equally of the latter two have their possess sets of plugins.”
“The implant was developed close to the attackers’ capability to conduct packet interception, enabling NSPX30 operators to conceal their infrastructure.”
The origins of the backdoor, which is also able of bypassing quite a few Chinese anti-malware alternatives by allowlisting alone, can be traced to an additional malware from January 2005 codenamed Job Wooden, which is designed to harvest program and network information and facts, report keystrokes, and get screenshots from victim programs.

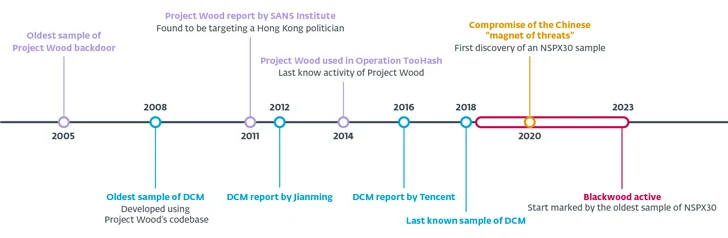
Project Wood’s codebase has acted as the foundation for quite a few implants, like spawning variants like DCM (aka Dark Specter) in 2008, with the malware subsequently employed in attacks concentrating on individuals of interest in Hong Kong and the Bigger China spot in 2012 and 2014.
NSPX30, the most current iteration of the implant, is delivered when attempts to obtain application updates from respectable servers working with the (unencrypted) HTTP protocol effects in a method compromise, paving the way for the deployment of a dropper DLL file.
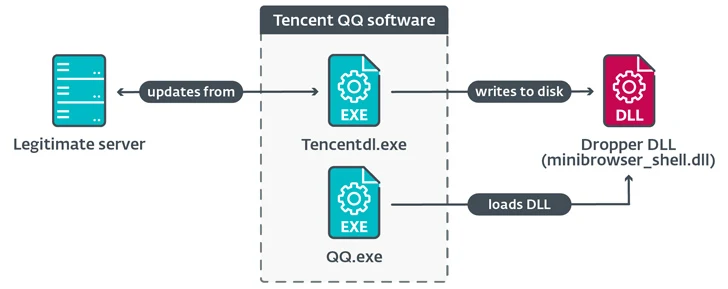
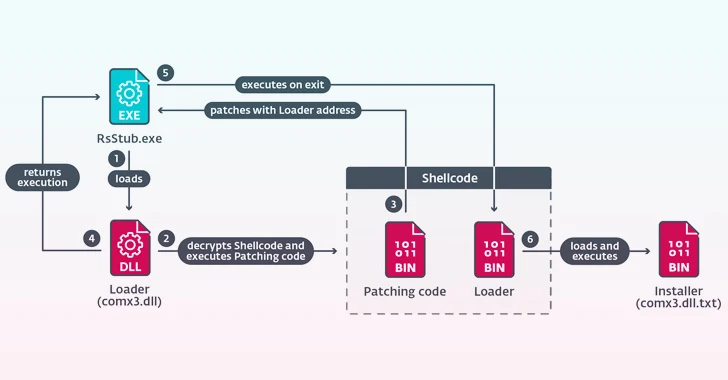
The destructive dropper deployed as section of the compromised update system generates a number of documents on disk and executes “RsStub.exe,” a binary connected with the Growing Antivirus application so as to start “comx3.dll” by taking edge of the reality the former is inclined to DLL aspect-loading.
“comx3.dll” features as a loader to execute a 3rd file named “comx3.dll.txt,” which is an installer library responsible for activating the next-phase attack chain that culminates in the execution of the orchestrator part (“Earn.cfg”).
It truly is currently not recognised how the menace actors supply the dropper in the sort of destructive updates, but Chinese threat actors like BlackTech, Evasive Panda, and Mustang Panda have leveraged compromised routers as a channel to distribute malware in the past.
ESET speculates that the attackers “are deploying a network implant in the networks of the victims, perhaps on susceptible network appliances such as routers or gateways.”
“The fact that we identified no indications of site visitors redirection by means of DNS may well suggest that when the hypothesized network implant intercepts unencrypted HTTP traffic similar to updates, it replies with the NSPX30 implant’s dropper in the sort of a DLL, an executable file, or a ZIP archive containing the DLL.”
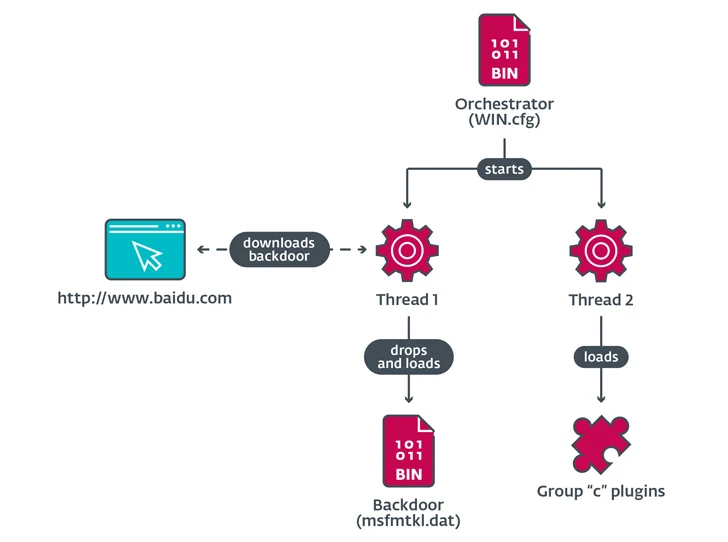
The orchestrator then proceeds to build two threads, a person to attain the backdoor (“msfmtkl.dat”) and yet another to load its plugins and increase exclusions to allowlist the loader DLLs to bypass Chinese anti-malware answers.
The backdoor is downloaded by way of an HTTP request to Baidu’s web site www.baidu[.]com, a legit Chinese search motor, with an unconventional Person-Agent string that masquerades the ask for as originating from the Internet Explorer browser on Windows 98.
The reaction from the server is then saved to a file from which the backdoor element is extracted and loaded into memory.

NSPX30, as section of its initialization period, also generates a passive UDP listening socket for acquiring commands from the controller and exfiltrating data by most likely intercepting DNS query packets in get to anonymize its command-and-handle (C2) infrastructure.
The directions enable the backdoor to build a reverse shell, acquire file details, terminate unique procedures, capture screenshots, log keystrokes, and even uninstall by itself from the contaminated machine.
The disclosure arrives weeks following SecurityScorecard unveiled new infrastructure related to a different Beijing-nexus cyber espionage group regarded as Volt Typhoon (aka Bronze Silhouette) that leverages a botnet produced by exploiting identified security flaws in conclude-of-everyday living Cisco RV320/325 routers (CVE-2019-1652 and CVE-2019-1653) operating throughout Europe, North The usa, and Asia Pacific.
“Close to 30% of them (325 of 1,116 units) communicated with two IP addresses formerly named as proxy routers used for command-and-command (C2) communications, 174.138.56[.]21 and 159.203.113[.]25, in a 30-working day period,” the organization reported.
“Volt Typhoon may purpose to use these compromised equipment to transfer stolen info or link to target organizations’ networks.”
Observed this post intriguing? Stick to us on Twitter and LinkedIn to read far more exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com

 New CherryLoader Malware Mimics CherryTree to Deploy PrivEsc Exploits
New CherryLoader Malware Mimics CherryTree to Deploy PrivEsc Exploits