The 2023/2024 Axur Risk Landscape Report presents a in depth assessment of the most current cyber threats. The info brings together facts from the platform’s surveillance of the Surface, Deep, and Dark Web with insights derived from the in-depth exploration and investigations executed by the Danger Intelligence staff.
Uncover the total scope of digital threats in the Axur Report 2023/2024.
Overview
In 2023, the cybersecurity landscape witnessed a impressive increase in cyberattacks.
A single notable shift was the cyber risk integration with company risk, a principle getting traction in boardrooms around the world. As the magnitude of losses thanks to cyberattacks became evident, corporations started out reevaluating their methods.
Geopolitical aspects played a major purpose in shaping details security. The conflicts amongst nations like Russia and Ukraine experienced ripple outcomes, influencing the methods of cybercriminals. It was a yr in which exterior aspects intertwined with digital threats.
Ransomware assaults, once primarily centered on encryption, took a new turn. Threat actors prioritized details publicity, focusing on organizations with hefty fines for details breaches. The stakes had been increased than ever.

Artificial intelligence emerged as a potent weapon in cyberattacks. From deepfake video clips that includes famous people to automated social engineering, AI’s part in cybercrime has grown significantly.
One particular example is the fake video clips advertising and marketing cryptocurrency cons applying celebs
such as billionaire Elon Musk and Ethereum creator Vitalik Buterin. The films use
images of these executives at gatherings, but the original traces are changed by an
AI-synthesized voice. The photos are only altered to assure lip sync, which is one more perform of this form of AI.
Hacktivist groups also built their mark, aligning with numerous sides all through international conflicts. Their symbolic assaults posed pitfalls to folks and corporations, highlighting the have to have for vigilance in an interconnected environment.
Let’s delve into the platform’s knowledge, below synthesized into 7 key conclusions.
Crucial results:
1. A Threefold Enhance in Leaked Playing cards
The report suggests a troubling escalation in cyber threats. In 2023, a staggering 13.5 million credit score and debit card particulars have been leaked, tripling the quantity from the preceding 12 months. The United States tops the record, accounting for nearly 50 % of all detected card leaks. This surge demonstrates the intensified activities on Deep & Dark Web channels, in which these details are usually traded.
 Top rated 10 International locations with the Most Exposed Cards
Top rated 10 International locations with the Most Exposed Cards
2. Spotlight on Credential Leaks and Info Stealers
Credential leaks, whilst steady at 4.2 billion, have witnessed a change with a surge in pastes and significant leaks as resources. Notably, 15% of these exposed credentials can be considered corporate, highlighting the urgency of robust corporate cybersecurity actions.
Distinctively, credential stealer malware poses a major risk by obtaining 98% of qualifications in simple textual content, bypassing encryption hurdles. These stolen passwords are meticulously cataloged in log files, giving cybercriminals with insights into acquisition methods. Furthermore, credential stealers seize authorization tokens and cookies, possibly compromising multi-variable authentication.
 Resource of Qualifications Leakage in 2023
Resource of Qualifications Leakage in 2023
3. Brand Misuse and Electronic Fraud Panorama
Unconventional use of manufacturer impersonation, such as in social media profiles, applications, and compensated adverts, led to 200,680 detections in 2023, a slight raise from the former calendar year.
 Varieties of Brand Misuse in 2023
Varieties of Brand Misuse in 2023
Take a look at the Risk Landscape Report for slicing-edge insights and alternatives.
4. New Frauds: Evolving Ways
The report has identified a series of novel ways that desire our notice. Notably, menace actors now possess the capability to establish entire e-commerce outlets in just a subject of minutes, leveraging well-known platforms.
Also, the increase of “apphishing” ripoffs has taken middle phase, showcasing the increasing sophistication of up to date cyber fraud. In these frauds, malicious applications masquerade as legit browsers, loading cloned web pages under the control of cybercriminals. This rising craze highlights the need for heightened vigilance and revolutionary countermeasures to combat these evolving threats properly.
5. Driving the Disruption Metrics: Takedown and Uptime
Very last calendar year, Axur executed 330,612 takedowns (the removing of a web page or web site from the internet) with a impressive good results rate, specifically in countering threats these as phishing (96.85%) and bogus accounts (97.63%). The spotlight of this approach is the automated notification workflows that significantly lower the time among incident identification and service provider notifications.
For instance, Axur initiates notifications for phishing cases within 5 minutes, giving economical managing for entities these as Shopify, Cloudflare, Namecheap, Hostinger, and GoDaddy, typically inside the exact day. When addressing brand name impersonation, accounts can be taken out from platforms like Facebook and Instagram (commonly in just an typical time of 41 minutes and 56 minutes, respectively) following notifications.
 Takedown Response Time by Business and System
Takedown Response Time by Business and System
6. Deep & Dark Web Insights: Monitoring the Underworld
The investigation of 133 million messages and posts on the Deep & Dark Web delivered insights into the techniques and procedures of destructive agents, taking part in a very important part in avoiding cyber threats. This monitoring extends to messaging applications such as Telegram, WhatsApp, and Discord, as properly as deep web forums and illicit marketplaces in which cybercriminals trade leaked facts, compromised computer obtain, and illicit services.
There are far more than 529,965 incidents on monitored Deep & Dark Web sources, concentrating on retail/e-commerce, economic establishments, and technology providers sectors.
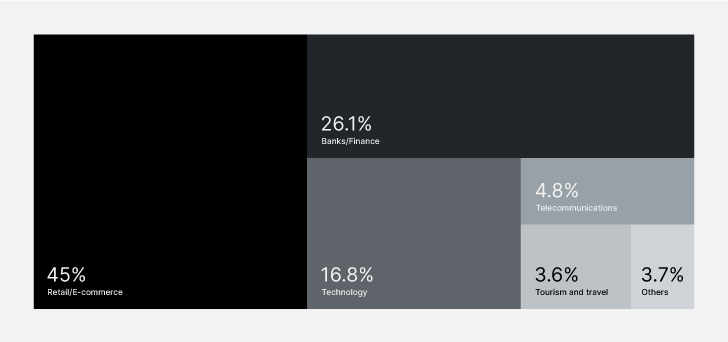 Most Focused Sectors on the Deep & Dark Web in 2023
Most Focused Sectors on the Deep & Dark Web in 2023
Notably, 374,592 incidents resulted from text detections, even though 155,373 incidents had been attributed to audio, online video, or impression detections. Multimedia material assessment is significantly essential as it unveils concealed threats and enhances general danger visibility.
7. Synthetic Intelligence: A New Frontier in Cybercrime
Synthetic Intelligence (AI) resources, effective for program and information development, are now being made use of for destructive purposes. These equipment help scammers to craft extra convincing narratives and interactions, improving the sophistication of fraud. On the other hand, Axur is groundbreaking the use of generative AI in cyber defense, launching Polaris.
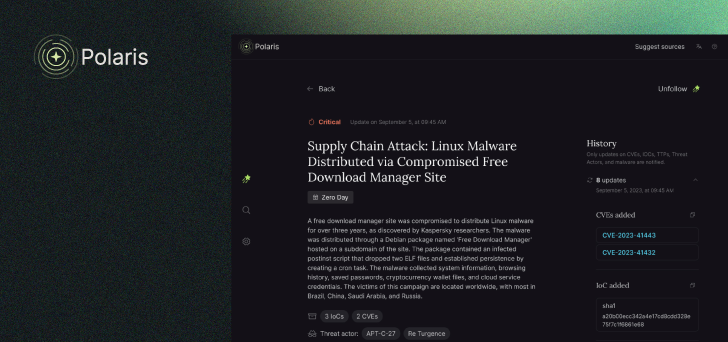
Polaris: AI-driven system to automate threat management
As the core of this AI-driven system, a specialised Massive Language Product sifts via extensive information swimming pools, delivering customized, actionable insights instantly aligned with the organization’s distinctive attack surface area. This innovative approach not only streamlines the menace intelligence system but also makes certain that security teams concentrate on strategic responses, improving productiveness and determination-producing.
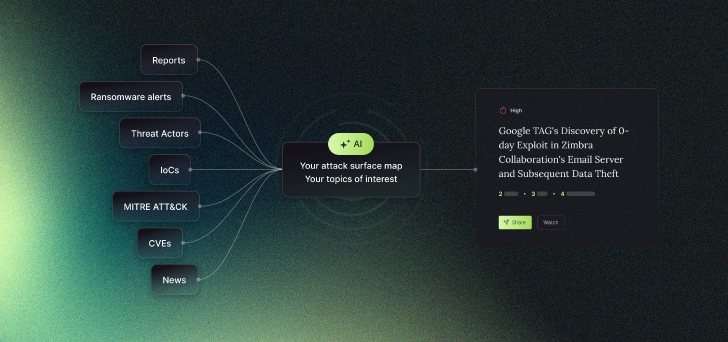
Polaris signifies a departure from the frustrating, fragmented mother nature of standard menace administration by presenting a cohesive and concentrated point of view that facilitates swift, educated steps towards probable threats, radically lessening analysis time and enhancing organizational response capability.

Your Automatic Threat Intel Analyst: Start out Your 15-Day Polaris Demo Now
Conclusion
The Axur Report elucidates the intricate and evolving cyber risk landscape, specifically highlighting the vulnerabilities and troubles confronted in the United States. The data offered underscores an urgent will need for businesses to adapt and fortify their cybersecurity frameworks in reaction to the escalating sophistication of cyber threats.
To navigate the complexities of the recent cybersecurity landscape, companies ought to target on two pivotal methods:
1. In depth Monitoring and Swift Response:
The essence of robust cybersecurity lies in the extended checking of electronic assets and the efficiency of response mechanisms. Companies will have to ensure deep surveillance of their digital ecosystem, such as tracking credential resources, monitoring the proliferation of faux profiles and apps, and vigilant oversight of Deep & Dark Web things to do.
This comprehensive checking have to be coupled with a rapid and decisive reaction to limit the publicity window of probable fraud and digital risks. By identifying and addressing threats promptly, companies can considerably mitigate the impacts of cyber incidents.
2. Harnessing AI for Risk Intelligence and Automation:
Leveraging synthetic intelligence is becoming not just useful but important. As manual function is no for a longer period viable, AI-pushed systems supply unparalleled positive aspects in scaling and automating the detection and neutralization of cyber threats. By adopting AI-powered sophisticated security alternatives, organizations can enrich their threat monitoring and investigation capabilities.
This not only assures a brief and knowledgeable response to cyber incidents but also strengthens the organization’s in general defense framework. Embracing a multi-layered security solution that combines proactive prevention with reactive tactics and AI’s analytical prowess makes sure a more resilient defense from the more and more sophisticated landscape of cyber threats.
Learn A lot more About Axur
Axur is a chopping-edge Exterior Risk Intelligence system renowned for its conclusion-to-close automation, major-tier takedown capabilities, and scalable intelligence. Empowering details security teams, Axur ensures safer digital ordeals by detecting, inspecting, and made up of threats across the exterior perimeter.
Found this short article interesting? Observe us on Twitter and LinkedIn to read far more special written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 China-backed Hackers Hijack Software Updates to Implant “NSPX30” Spyware
China-backed Hackers Hijack Software Updates to Implant “NSPX30” Spyware