A new Go-primarily based malware loader named CherryLoader has been discovered by menace hunters in the wild to supply added payloads on to compromised hosts for adhere to-on exploitation.
Arctic Wolf Labs, which found the new attack software in two latest intrusions, claimed the loader’s icon and identify masquerades as the legitimate CherryTree note-taking application to dupe potential victims into installing it.
“CherryLoader was utilised to drop one of two privilege escalation applications, PrintSpoofer or JuicyPotatoNG, which would then operate a batch file to set up persistence on the target device,” scientists Hady Azzam, Christopher Prest, and Steven Campbell stated.
In a different novel twist, CherryLoader also packs modularized attributes that permit the threat actor to swap exploits without the need of recompiling code.

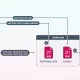
It can be currently not known how the loader is dispersed, but the attack chains examined by the cybersecurity organization clearly show that CherryLoader (“cherrytree.exe”) and its associated files (“NuxtSharp.Details,” “Spof.Details,” and “Juicy.Data”) are contained in a RAR archive file (“Packed.rar”) hosted on the IP deal with 141.11.187[.]70.
Downloaded alongside with the RAR file is an executable (“main.exe”) that’s utilized to unpack and launch the Golang binary, which only proceeds if the 1st argument passed to it matches a difficult-coded MD5 password hash.
The loader subsequently decrypts “NuxtSharp.Knowledge” and writes its contents to a file named “File.log” on disk that, in turn, is created to decode and operate “Spof.Details” as “12.log” employing a fileless system acknowledged as process ghosting that first came to mild in June 2021.
“This procedure is modular in style and will allow the menace actor to leverage other exploit code in position of Spof.Data,” the scientists explained. “In this case, Juicy.Knowledge which contains a different exploit, can be swapped in location without having recompiling File.log.”

The procedure associated with “12.log” is connected to an open-source privilege escalation tool named PrintSpoofer, although “Juicy.Data” is a further privilege escalation device named JuicyPotatoNG.
A successful privilege escalation is adopted by the execution of a batch file script termed “user.bat” to set up persistence on the host and disarm Microsoft Defender.
“CherryLoader is [a] newly discovered multi-phase downloader that leverages different encryption approaches and other anti-assessment strategies in an attempt to detonate choice, publicly accessible privilege escalation exploits with out possessing to recompile any code,” the researchers concluded.
Discovered this post exciting? Observe us on Twitter and LinkedIn to go through extra unique material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Tech Giant HP Enterprise Hacked by Russian Hackers Linked to DNC Breach
Tech Giant HP Enterprise Hacked by Russian Hackers Linked to DNC Breach