Technology, investigate, and federal government sectors in the Asia-Pacific area have been focused by a risk actor called BlackTech as component of a new cyber attack wave.
The intrusions pave the way for an updated variation of modular backdoor dubbed Waterbear as perfectly as its enhanced successor referred to as Deuterbear.
“Waterbear is known for its complexity, as it uses a variety of evasion mechanisms to decrease the opportunity of detection and examination,” Development Micro researchers Cyris Tseng and Pierre Lee claimed in an analysis very last week.
“In 2022, Earth Hundun commenced working with the hottest model of Waterbear — also recognised as Deuterbear — which has many modifications, such as anti-memory scanning and decryption routines, that make us contemplate it a distinctive malware entity from the unique Waterbear.”

The cybersecurity company is monitoring the danger actor below the moniker Earth Hundun, which is recognized to be energetic since at the very least 2007. It also goes by other names these as Circuit Panda, HUAPI, Manga Taurus, Palmerworm, Red Djinn, and Temp.Overboard.
In a joint advisory published previous September, cybersecurity and intelligence businesses from Japan and the U.S. attributed the adversary to China, describing its potential to modify router firmware and exploit routers’ domain-have faith in interactions to pivot from international subsidiaries to their corporate headquarters primarily based in the two nations around the world.
“BlackTech actors use custom made malware, twin-use equipment, and residing-off-the-land techniques, this kind of as disabling logging on routers, to conceal their functions,” the governments said.
“On attaining an original foothold into a goal network and attaining administrator access to network edge products, BlackTech cyber actors typically modify the firmware to disguise their exercise throughout the edge devices to even more retain persistence in the network.”
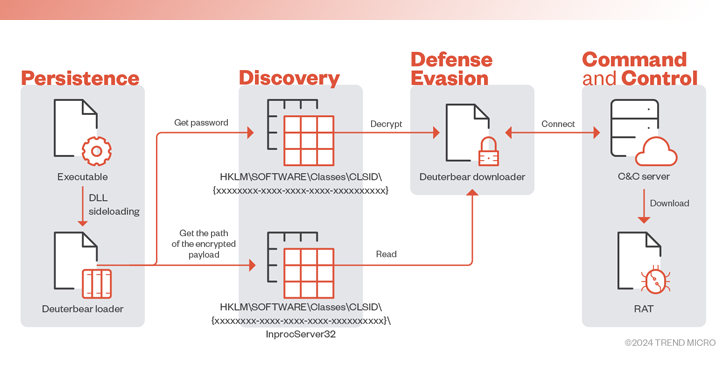
A person of the crucial equipment in its multifaceted arsenal is Waterbear (aka DBGPRINT), which has been put to use considering that 2009 and has been persistently up-to-date over the years with enhanced protection evasion options.
The core distant obtain trojan is fetched from a command-and-regulate (C2) server by usually means of a downloader, which is introduced utilizing a loader that, in convert, is executed via a known strategy referred to as DLL side-loading.
The most recent edition of the implant supports nearly 50 instructions, enabling it to complete a large variety of things to do, including course of action enumeration and termination, file operations, window administration, get started and exit distant shell, screenshot capture, and Windows Registry modification, amongst many others.

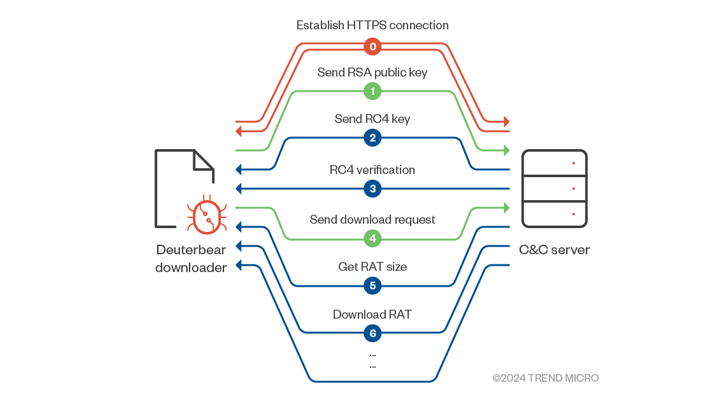
Also delivered applying a equivalent an infection movement considering that 2022 is Deuterbear, whose downloader implements an array of obfuscation techniques to resist anti-evaluation and takes advantage of HTTPS for C2 communications.
“Because 2009, Earth Hundun has consistently advanced and refined the Waterbear backdoor, as well as its many variants and branches,” the scientists explained.
“The Deuterbear downloader employs HTTPS encryption for network targeted visitors defense and implements several updates in malware execution, such as altering the functionality decryption, examining for debuggers or sandboxes, and modifying website traffic protocols.”
Discovered this short article intriguing? Abide by us on Twitter and LinkedIn to read through additional unique written content we put up.
Some parts of this article are sourced from:
thehackernews.com

 How Attackers Can Own a Business Without Touching the Endpoint
How Attackers Can Own a Business Without Touching the Endpoint