Millions of computer software repositories on GitHub are most likely susceptible to an attack called RepoJacking, a new study has exposed.
This involves repositories from organizations this sort of as Google, Lyft, and a number of others, Massachusetts-based cloud-native security company Aqua stated in a Wednesday report.
The provide chain vulnerability, also identified as dependency repository hijacking, is a class of assaults that would make it feasible to get about retired corporations or person names and publish trojanized variations of repositories to operate malicious code.
“When a repository proprietor improvements their username, a link is produced concerning the aged identify and the new identify for any person who downloads dependencies from the aged repository,” scientists Ilay Goldman and Yakir Kadkoda reported. “Having said that, it is achievable for everyone to make the old username and break this hyperlink.”

Alternatively, a identical situation could crop up when a repository ownership is transferred to a further consumer and the original account is deleted, thus allowing a poor actor to create an account with the previous username.
Aqua explained a menace actor could leverage web sites like GHTorrent to extract GitHub metadata related with any community commits and pull requests to compile a record of one of a kind repositories.
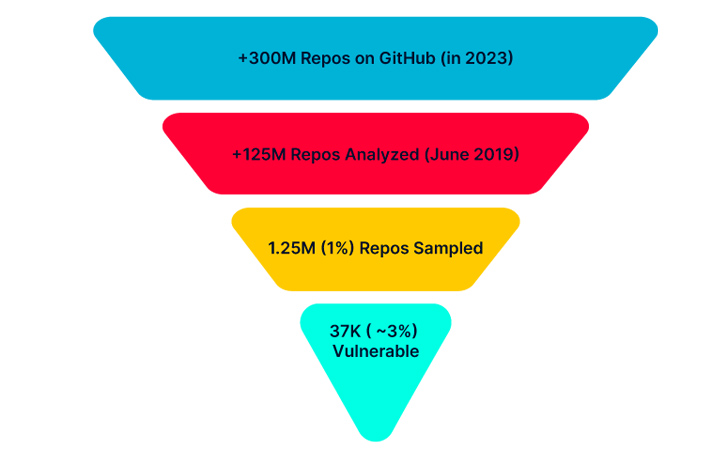
An evaluation of a subset of 1.25 million repositories for the month of June 2019 disclosed that as numerous as 36,983 repositories were being vulnerable to RepoJacking, denoting a 2.95% accomplishment fee.
With GitHub that contains more than 330 million repositories, the results counsel that tens of millions of repositories could be vulnerable to a very similar attack.
A person these types of repository is google/mathsteps, which was earlier under the possession of Socratic (socraticorg/mathsteps), a corporation that was acquired by Google in 2018.
Upcoming WEBINAR🔐 Mastering API Security: Knowledge Your True Attack Floor
Uncover the untapped vulnerabilities in your API ecosystem and just take proactive actions in direction of ironclad security. Join our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:immediately aftershow:inline-block.look at_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px solid #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-right-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-measurement:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-best:2px reliable #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-bodyweight:900textual content-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-size:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-size:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-pounds:500letter-spacing:.2px
“When you accessibility https://github.com/socraticorg/mathsteps, you are becoming redirected to https://github.com/google/mathsteps so finally the person will fetch Google’s repository,” the researchers explained.
“Having said that, for the reason that the socraticorg corporation was offered, an attacker could open the socraticorg/mathsteps repository and customers next Google’s directions will clone the attacker’s repository in its place. And because of the npm put in this will direct to arbitrary code execution on the buyers.”
This is not the initial time this sort of problems have been elevated. In October 2022, GitHub moved to near a security loophole that could have been exploited to develop destructive repositories and mount offer chain assaults by circumventing popular repository namespace retirement.
To mitigate this kind of risks, it truly is recommended that customers periodically examine their code for inbound links that may well be retrieving resources from external GitHub repositories.
“If you alter your group title, guarantee that you nevertheless possess the preceding name as nicely, even as a placeholder, to stop attackers from making it,” the scientists mentioned.
Observed this write-up exciting? Stick to us on Twitter and LinkedIn to read through additional exceptional articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Camaro Dragon Hackers Strike with USB-Driven Self-Propagating Malware
Camaro Dragon Hackers Strike with USB-Driven Self-Propagating Malware