Cybersecurity researchers have determined a set of 116 destructive offers on the Python Deal Index (PyPI) repository that are intended to infect Windows and Linux techniques with a custom made backdoor.
“In some situations, the remaining payload is a variant of the notorious W4SP Stealer, or a easy clipboard monitor to steal cryptocurrency, or each,” ESET scientists Marc-Etienne M.Léveillé and Rene Holt said in a report published before this 7 days.
The packages are estimated to have been downloaded over 10,000 occasions since Could 2023.
The menace actors behind the exercise have been observed working with a few approaches to bundle malicious code into Python packages, particularly via a exam.py script, embedding PowerShell in set up.py file, and incorporating it in obfuscated kind in the __init__.py file.
Future WEBINAR Beat AI-Driven Threats with Zero Have confidence in – Webinar for Security Gurus
Common security actions won’t minimize it in modern environment. It’s time for Zero Belief Security. Secure your info like by no means prior to.
Sign up for Now
Irrespective of the system utilized, the end goal of the campaign is to compromise the focused host with malware, generally a backdoor capable of remote command execution, info exfiltration, and using screenshots. The backdoor module is carried out in Python for Windows and in Go for Linux.
Alternately, the attack chains also culminate in the deployment of W4SP Stealer or a clipper malware developed to retain close tabs on a victim’s clipboard activity and swapping the original wallet handle, if present, with an attacker-managed address.
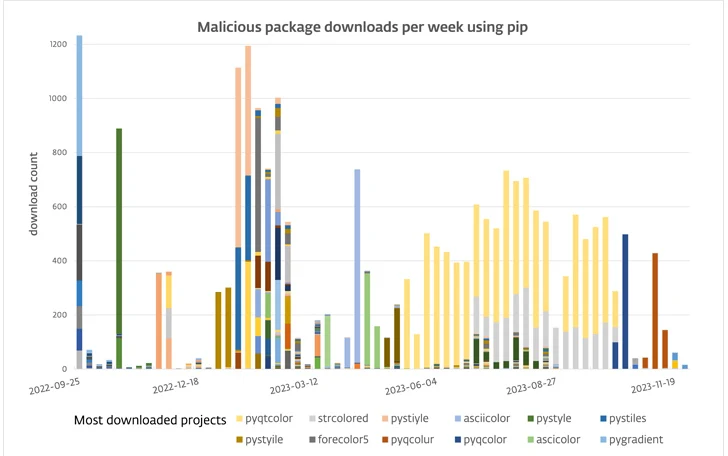
The development is the most recent in a wave of compromised Python offers attackers have launched to poison the open up-resource ecosystem and distribute a medley of malware for offer chain attacks.
It is really also the latest addition to a continual stream of bogus PyPI offers that have acted as a stealthy channel for distributing stealer malware. In May 2023, ESET discovered yet another cluster of libraries that have been engineered to propagate Sordeal Stealer, which borrows its functions from W4SP Stealer.
Then, last month, destructive packages masquerading as seemingly innocuous obfuscation applications ended up discovered to deploy a stealer malware codenamed BlazeStealer.

“Python builders should really comprehensively vet the code they down load, primarily examining for these procedures, right before setting up it on their systems,” the scientists cautioned.
The disclosure also follows the discovery of npm deals that have been discovered concentrating on an unnamed financial institution as component of an “highly developed adversary simulation training.” The names of the modules, which contained an encrypted blob, have been withheld to protect the identification of the group.
“This decrypted payload incorporates an embedded binary that cleverly exfiltrates person qualifications to a Microsoft Teams webhook that is interior to the concentrate on corporation in dilemma,” application supply chain security firm Phylum disclosed previous week.
Identified this report exciting? Follow us on Twitter and LinkedIn to read a lot more distinctive articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 New Pierogi++ Malware by Gaza Cyber Gang Targeting Palestinian Entities
New Pierogi++ Malware by Gaza Cyber Gang Targeting Palestinian Entities