A novel multi-platform menace identified as NKAbuse has been discovered making use of a decentralized, peer-to-peer network connectivity protocol regarded as NKN (small for New Variety of Network) as a communications channel.
“The malware utilizes NKN technology for details trade amongst friends, working as a strong implant, and outfitted with each flooder and backdoor capabilities,” Russian cybersecurity firm Kaspersky reported in a Thursday report.
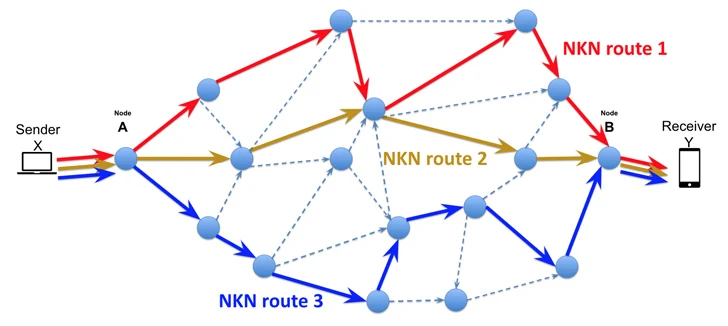
NKN, which has in excess of 62,000 nodes, is explained as a “computer software overlay network developed on major of present-day Internet that allows end users to share unused bandwidth and get paid token benefits.” It incorporates a blockchain layer on top rated of the present TCP/IP stack.
Upcoming WEBINAR Conquer AI-Run Threats with Zero Have confidence in – Webinar for Security Industry experts
Conventional security actions will never lower it in today’s entire world. It truly is time for Zero Belief Security. Protected your knowledge like never ever in advance of.
Join Now
Whilst threat actors are regarded to consider advantage of rising conversation protocols for command-and-regulate (C2) purposes and evade detection, NKAbuse leverages blockchain technology to carry out distributed denial-of-service (DDoS) assaults and function as an implant within compromised devices.
Precisely, it takes advantage of the protocol to converse to the bot master and receive/deliver instructions. The malware is carried out in the Go programming language, and evidence points to it being applied generally to single out Linux devices, which include IoT equipment.
It really is at present not recognised how popular the assaults are, but a single occasion discovered by Kaspersky entails the exploitation of a 6-year-old critical security flaw in Apache Struts (CVE-2017-5638, CVSS score: 10.) to breach an unnamed monetary company.
Profitable exploitation is followed by the shipping and delivery of an original shell script that’s liable for downloading the implant from a distant server, but not ahead of examining the running method of the target host. The server hosting the malware houses eight distinct variations of NKAbuse to support a variety of CPU architectures: i386, arm64, arm, amd64, mips, mipsel, mips64, and mips64el.
Another noteworthy facet is its absence of a self-propagation system, meaning the malware desires to be delivered to a target by another original accessibility pathway, these as via the exploitation of security flaws.

“NKAbuse helps make use of cron employment to survive reboots,” Kaspersky claimed. “To obtain that, it requirements to be root. It checks that the recent user ID is and, if so, proceeds to parse the current crontab, including by itself for each and every reboot.”
NKAbuse also incorporates a bevy of backdoor characteristics that let it to periodically send a heartbeat concept to the bot learn, which incorporates information and facts about the process, seize screenshots of the present-day screen, conduct file functions, and operate program commands.
“This distinct implant appears to have been meticulously crafted for integration into a botnet, yet it can adapt to working as a backdoor in a particular host,” Kaspersky claimed. “Also, its use of blockchain technology guarantees both reliability and anonymity, which implies the possible for this botnet to develop steadily more than time, seemingly devoid of an identifiable central controller.”
Discovered this post interesting? Stick to us on Twitter and LinkedIn to browse a lot more distinctive content material we article.
Some parts of this article are sourced from:
thehackernews.com


 116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems
116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems