A pro-Hamas danger actor recognised as Gaza Cyber Gang is targeting Palestinian entities making use of an up-to-date model of a backdoor dubbed Pierogi.
The results arrive from SentinelOne, which has supplied the malware the identify Pierogi++ owing to the reality that it can be executed in the C++ programming language compared with its Delphi- and Pascal-centered predecessor.
“Recent Gaza Cybergang activities exhibit steady targeting of Palestinian entities, with no noticed major improvements in dynamics because the begin of the Israel-Hamas war,” security researcher Aleksandar Milenkoski claimed in a report shared with The Hacker News.
Gaza Cyber Gang, thought to be energetic given that at the very least 2012, has a background of placing targets through the Center East, significantly Israel and Palestine, frequently leveraging spear-phishing as a approach of initial accessibility.
Upcoming WEBINAR Defeat AI-Driven Threats with Zero Belief – Webinar for Security Gurus
Traditional security measures will never lower it in modern entire world. It is really time for Zero Have confidence in Security. Secure your facts like under no circumstances in advance of.
Sign up for Now
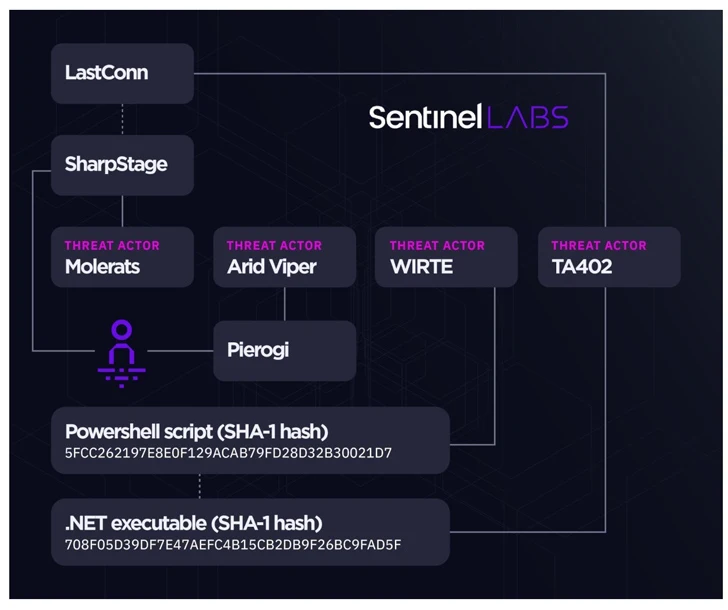
Some of the notable malware families in its arsenal involve BarbWire, DropBook, LastConn, Molerat Loader, Micropsia, NimbleMamba, SharpStage, Spark, Pierogi, PoisonIvy, and XtremeRAT among the other individuals.
The menace actor is assessed to be a composite of numerous sub-teams that share overlapping victimology footprints and malware, this kind of as Molerats, Arid Viper, and a cluster referred to as Operation Parliament by Kaspersky.
In latest months, the adversarial collective has been connected to a collection of attacks that provide improvised variants of its Micropsia and Arid Gopher implants as very well as a new original accessibility downloader dubbed IronWind.
The newest set of intrusions mounted by Gaza Cyber Gang has been discovered to leverage Pierogi++ and Micropsia. The initially recorded use of Pierogi++ goes again to late 2022.
Attack chains are characterized by the use of decoy documents prepared in Arabic or English and pertaining to issues of curiosity to Palestinians to produce the backdoors.
Cybereason, which shed light-weight on Pierogi in February 2020, described it as an implant that enables attackers to spy on focused victims and that the “commands employed to communicate with the [command-and-control] servers and other strings in the binary are created in Ukrainian.”

“The backdoor might have been received in underground communities rather than property-grown,” it assessed at the time.
Equally Pierogi and Pierogi++ are geared up to just take screenshots, execute instructions, and obtain attacker-delivered information. Another notable factor is that the current artifacts no extended attribute any Ukrainian strings in the code.
SentinelOne’s investigation into Gaza Cyber Gang’s functions have also yielded tactical connections between two disparate campaigns referred to as Major Bang and Operation Bearded Barbie, in addition to reinforcing ties among the threat actor and WIRTE, as beforehand disclosed by Kaspersky in November 2021.
The sustained concentration on Palestine notwithstanding, the discovery of Pierogi++ underscores that the team continues to refine and retool its malware to be certain successful compromise of targets and to keep persistent accessibility to their networks.
“The noticed overlaps in targeting and malware similarities across the Gaza Cybergang sub-groups immediately after 2018 indicates that the team has most likely been going through a consolidation process,” Milenkoski explained.
“This perhaps contains the formation of an inside malware improvement and maintenance hub and/or streamlining source from external vendors.”
Uncovered this report intriguing? Stick to us on Twitter and LinkedIn to browse extra unique material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Iranian State-Sponsored OilRig Group Deploys 3 New Malware Downloaders
Iranian State-Sponsored OilRig Group Deploys 3 New Malware Downloaders