A critical security flaw in the Bricks theme for WordPress is staying actively exploited by risk actors to run arbitrary PHP code on vulnerable installations.
The flaw, tracked as CVE-2024-25600 (CVSS rating: 9.8), permits unauthenticated attackers to realize distant code execution. It impacts all versions of the Bricks up to and which includes 1.9.6.
It has been resolved by the theme developers in version 1.9.6.1 introduced on February 13, 2024, merely times soon after WordPress security supplier Snicco noted the flaw on February 10.
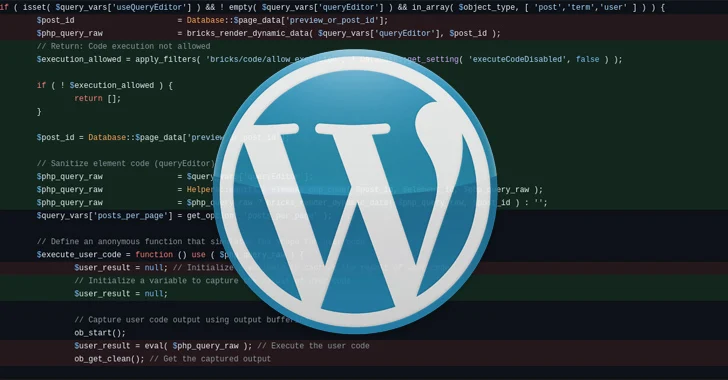
When a proof-of-principle (PoC) exploit has not been unveiled, specialized details have been unveiled by both equally Snicco and Patchstack, noting that the underlying susceptible code exists in the prepare_query_vars_from_configurations() functionality.
Precisely, it problems the use of security tokens known as “nonces” for verifying permissions, which can then be employed to pass arbitrary instructions for execution, efficiently letting a risk actor to seize regulate of a targeted web site.
The nonce value is publicly obtainable on the frontend of a WordPress web-site, Patchstack reported, including there are no enough purpose checks applied.

“Nonces should really hardly ever be relied on for authentication, authorization, or accessibility command,” WordPress cautions in its documentation. “Defend your features utilizing latest_person_can(), and always assume nonces can be compromised.”
WordPress security firm Wordfence claimed it detected around a few dozen attack attempts exploiting the flaw as of February 19, 2024. Exploitation makes an attempt are claimed to have commenced on February 14, a day soon after public disclosure.
A vast majority of the assaults are from the next IP addresses –
- 200.251.23[.]57
- 92.118.170[.]216
- 103.187.5[.]128
- 149.202.55[.]79
- 5.252.118[.]211
- 91.108.240[.]52
Bricks is believed to have close to 25,000 currently energetic installations. Buyers of the plugin are advisable to apply the newest patches to mitigate likely threats.
Observed this posting intriguing? Comply with us on Twitter and LinkedIn to read through far more distinctive articles we post.
Some parts of this article are sourced from:
thehackernews.com

 Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative
Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative