Hackers backed by Iran and Hezbollah staged cyber attacks designed to undercut general public support for the Israel-Hamas war soon after Oct 2023.
This includes destructive attacks versus critical Israeli organizations, hack-and-leak operations concentrating on entities in Israel and the U.S., phishing campaigns created to steal intelligence, and information operations to transform community impression towards Israel.
Iran accounted for nearly 80% of all governing administration-backed phishing action focusing on Israel in the 6 months leading up to the Oct 7 assaults, Google stated in a new report.
“Hack-and-leak and facts operations remain a vital ingredient in these and related danger actors’ attempts to telegraph intent and capacity all over the war, each to their adversaries and to other audiences that they seek to influence,” the tech large reported.
But what is actually also noteworthy about the Israel-Hamas conflict is that the cyber functions seem to be executed independently of the kinetic and battlefield actions, as opposed to observed in the circumstance of the Russo-Ukrainian war.
These types of cyber abilities can be swiftly deployed at a reduced price tag to have interaction with regional rivals with no direct military confrontation, the firm added.
One of the Iran-affiliated groups, dubbed GREATRIFT (aka UNC4453 or Plaid Rain), is claimed to have propagated malware via fake “lacking folks” web-site targeting people searching for updates on kidnapped Israelis. The danger actor also used blood donation-themed entice documents as a distribution vector.

At least two hacktivist personas named Karma and Handala Hack, have leveraged wiper malware strains this sort of as BiBi-Windows Wiper, BiBi-Linux Wiper, ChiLLWIPE, and COOLWIPE to stage destructive attacks towards Israel and delete files from Windows and Linux methods, respectively.
A different Iranian country-state hacking team known as Charming Kitten (aka APT42 or CALANQUE) focused media and non-governmental businesses (NGOs) with a PowerShell backdoor known as POWERPUG as part of a phishing campaign observed in late October and November 2023.
POWERPUG is also the most current addition to the adversary’s extended record of backdoors, which includes PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho), NokNok, and BASICSTAR.

Hamas-linked groups, on the other hand, focused Israeli application engineers with coding assignment decoys in an attempt to dupe them into downloading SysJoker malware months ahead of the October 7 attacks. The marketing campaign has been attributed to a menace actor referred to as BLACKATOM.
“The attackers […] posed as workers of legitimate corporations and arrived at out by way of LinkedIn to invite targets to implement for computer software enhancement freelance opportunities,” Google stated. “Targets provided program engineers in the Israeli military, as nicely as Israel’s aerospace and defense industry.”
The tech big described the strategies adopted by Hamas cyber actors as uncomplicated but helpful, noting their use of social engineering to deliver remote accessibility trojans and backdoors like MAGNIFI to focus on consumers in both of those Palestine and Israel, which has been linked to BLACKSTEM (aka Molerats).
Incorporating yet another dimension to these strategies is the use of spy ware targeting Android phones that are able of harvesting delicate details and exfiltrating the information to attacker-controlled infrastructure.
The malware strains, termed MOAAZDROID and LOVELYDROID, are the handiwork of the Hamas-affiliated actor DESERTVARNISH, which is also tracked as Arid Viper, Desert Falcons, Renegade Jackal, and UNC718. Specifics about the spy ware were formerly documented by Cisco Talos in October 2023.

State-sponsored teams from Iran, these kinds of as MYSTICDOME (aka UNC1530), have also been observed targeting cell devices in Israel with the MYTHDROID (aka AhMyth) Android distant accessibility trojan as very well as a bespoke spy ware called SOLODROID for intelligence collection.
“MYSTICDOME distributed SOLODROID utilizing Firebase tasks that 302-redirected users to the Enjoy retail outlet, the place they had been prompted to set up the spy ware,” stated Google, which has due to the fact taken down the applications from the digital marketplace.
Google even further highlighted an Android malware named REDRUSE – a trojanized version of the legitimate Red Inform application utilised in Israel to warn of incoming rocket assaults – that exfiltrates contacts, messaging info, and place. It was propagated by way of SMS phishing messages that impersonated the law enforcement.
The ongoing war has also experienced an affect on Iran, with its critical infrastructure disrupted by an actor named Gonjeshke Darande (indicating Predatory Sparrow in Persian) in December 2023. The persona is considered to be connected to the Israeli Armed service Intelligence Directorate.
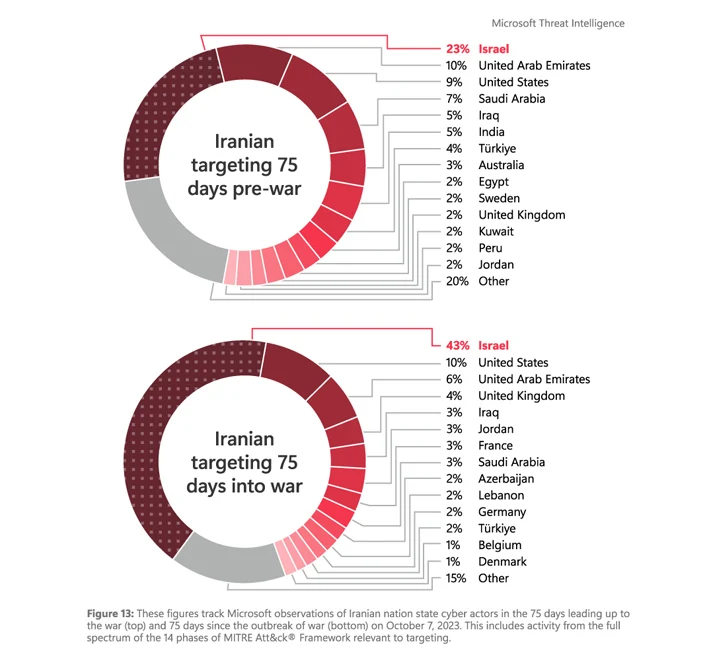
The results appear as Microsoft revealed that Iranian federal government-aligned actors have “released a sequence of cyberattacks and impact operations (IO) supposed to aid the Hamas lead to and weaken Israel and its political allies and organization partners.”
Redmond described their early-stage cyber and affect operations as reactive and opportunistic, when also corroborating with Google’s assessment that the assaults grew to become “ever more focused and harmful and IO strategies grew ever more subtle and inauthentic” next the outbreak of the war.

Beside ramping up and increasing their attack emphasis beyond Israel to encompass countries that Iran perceives as aiding Israel, like Albania, Bahrain, and the U.S., Microsoft claimed it observed collaboration amid Iran-affiliated teams such as Pink Sandstorm (aka Agrius) and Hezbollah cyber models.
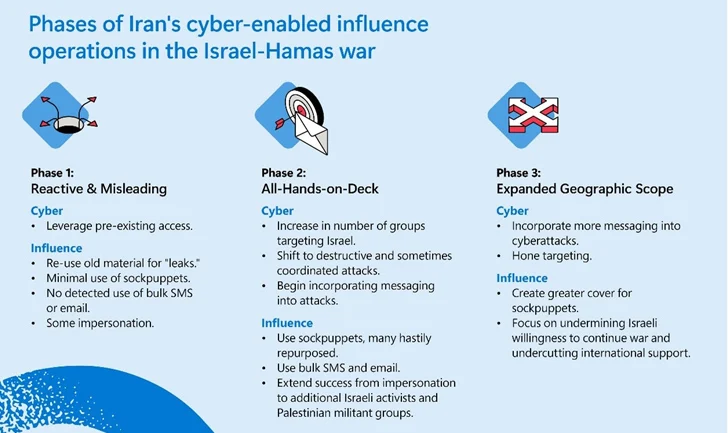
“Collaboration lowers the barrier to entry, making it possible for each group to contribute current capabilities and gets rid of the want for a one team to produce a entire spectrum of tooling or tradecraft,” Clint Watts, common manager at the Microsoft Danger Evaluation Middle (MTAC), reported.
Final week, NBC Information claimed that the U.S. recently introduced a cyber attack from an Iranian armed service ship named MV Behshad that experienced been accumulating intelligence on cargo vessels in the Crimson Sea and the Gulf of Aden.
An assessment from Recorded Upcoming very last month detailed how hacking personas and entrance teams in Iran are managed and operated by way of a range of contracting firms in Iran, which have out intelligence gathering and info functions to “foment instability in concentrate on nations around the world.”
“Even though Iranian teams rushed to perform, or merely fabricate, functions in the early times of the war, Iranian groups have slowed their the latest functions making it possible for them far more time to get preferred entry or build additional elaborate influence functions,” Microsoft concluded.
Uncovered this report intriguing? Observe us on Twitter and LinkedIn to browse a lot more exceptional articles we article.
Some parts of this article are sourced from:
thehackernews.com


 LockBit Ransomware’s Darknet Domains Seized in Global Law Enforcement Raid
LockBit Ransomware’s Darknet Domains Seized in Global Law Enforcement Raid