Cybersecurity researchers have in depth an current version of an innovative fingerprinting and redirection toolkit termed WoofLocker which is engineered to conduct tech assistance ripoffs.
The subtle targeted visitors redirection scheme was 1st documented by Malwarebytes in January 2020, leveraging JavaScript embedded in compromised internet websites to carry out anti-bot and web visitors filtering checks to provide next-stage JavaScript that redirects consumers to a browser locker (aka browlock).
This redirection system, in flip, can make use of steganographic methods to conceal the JavaScript code within a PNG image which is served only when the validation phase is successful. Should really a user be detected as a bot or not exciting visitors, a decoy PNG file without the need of the malicious code is utilised.
WoofLocker is also identified as 404Browlock owing to the actuality that going to the browlock URL immediately devoid of the suitable redirection or a person-time session token effects in a 404 mistake web page.
The cybersecurity firm’s most recent evaluation shows that the campaign is even now ongoing.

“The methods and tactics are incredibly comparable, but the infrastructure is now far more strong than prior to to defeat opportunity takedown makes an attempt,” Jérôme Segura, director of risk intelligence at Malwarebytes, said.
“It is just as hard to reproduce and analyze the redirection system now as it was then, particularly in mild of new fingerprinting checks” to detect the existence of virtual machines, particular browser extensions, and security instruments.
A majority of the web pages loading WoofLocker are adult web sites, with the infrastructure making use of hosting suppliers in Bulgaria and Ukraine that give the menace actors more robust protection versus takedowns.
The most important target of browser lockers is to get focused victims to contact for help to take care of (non-existent) laptop or computer challenges and obtain distant regulate in excess of the laptop or computer to draft an bill that recommends affected individuals to spend for a security alternative to deal with the dilemma.
“This is handled by 3rd-functions via fraudulent contact facilities,” Segura mentioned again in 2020. “The risk actor behind the website traffic redirection and browlock will get compensated for every single productive direct.”

The specific identification of the threat actor continues to be unknown and there is proof preparations for the marketing campaign have been underway as early as 2017.
“Compared with other strategies that depend on purchasing adverts and actively playing whack-a-mole with hosting providers and registrars, WoofLocker is a incredibly stable and lower routine maintenance company,” Segura mentioned. “The websites hosting the malicious code have been compromised for several years whilst the fingerprinting and browser locker infrastructure seems to be utilizing stable registrar and hosting suppliers.”
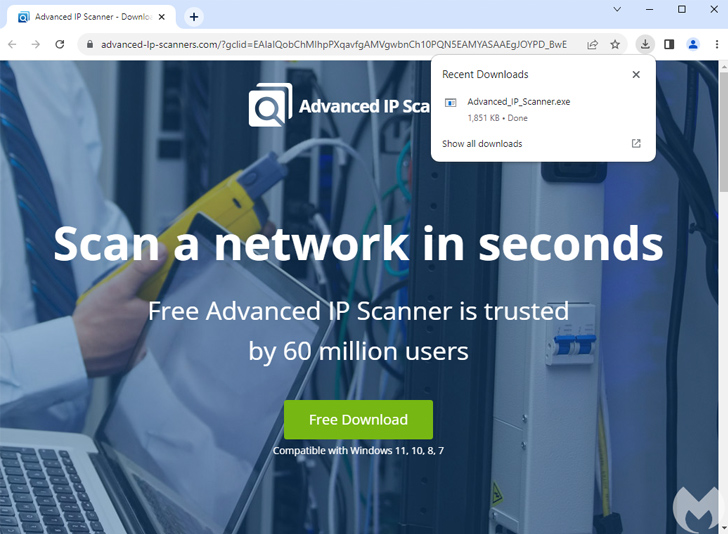
The disclosure arrives as the organization detailed a new malvertising infection chain that requires employing bogus adverts on lookup engines to direct users searching for remote accessibility programs and scanners to booby-trapped internet websites that direct to the deployment of stealer malware.

What sets this campaign apart is its capacity to fingerprint site visitors working with the WEBGL_debug_renderer_information API to collect the victim’s graphics driver properties to form actual browsers from crawlers and digital equipment and exfiltrate the knowledge to a distant server in buy to figure out the following class of action.
“By using much better filtering right before redirecting potential victims to malware, threat actors be certain that their destructive advertisements and infrastructure stay on line lengthier,” Segura explained. “Not only does it make it much more tricky for defenders to establish and report this kind of situations, it also most likely has an impression on takedown actions.”
The enhancement also follows new study which found that internet websites belonging to U.S. government organizations, top universities, and qualified companies have been hijacked more than the last 5 a long time and used to press scam features and promotions through “poison PDF” information uploaded to the portals.
A lot of of these ripoffs are aimed at small children and endeavor to trick them into downloading applications, malware, or publishing personal specifics in exchange for non-existent rewards in on the internet gaming platforms these types of as Fortnite and Roblox.
Discovered this posting attention-grabbing? Observe us on Twitter and LinkedIn to go through a lot more unique content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 New Juniper Junos OS Flaws Expose Devices to Remote Attacks – Patch Now
New Juniper Junos OS Flaws Expose Devices to Remote Attacks – Patch Now