The menace actors at the rear of the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and focusing on action aimed at Taiwan-based mostly organizations and a U.S. military procurement method.
Other than recompiling malware samples for unique architectures, the artifacts are claimed to have been hosted on new virtual private servers (VPSs), Lumen Black Lotus Labs reported in a report printed final 7 days.
The cybersecurity agency described the action cluster as “brazen” and “one of the most audacious,” indicating no indicators of slowing down. The id and the origin of the risk actors are presently mysterious.
Targets included industrial corporations, these as semiconductor and chemical manufacturers, and at the very least one municipal government firm in Taiwan as well as a U.S. Division of Protection (DoD) server affiliated with submitting and retrieving proposals for defense contracts.

HiatusRAT was initial disclosed by the cybersecurity organization in March 2023 as possessing targeted business enterprise-quality routers to covertly spy on victims mostly situated in Latin America and Europe as element of a marketing campaign that commenced in July 2022.
As quite a few as 100 edge networking gadgets globally had been infected to passively accumulate targeted traffic and renovate them into a proxy network of command-and-command (C2) infrastructure.
The newest established of attacks, noticed from mid-June by means of August 2023, entail the use of pre-crafted HiatusRAT binaries specifically made for Arm, Intel 80386, and x86-64 architectures, along with MIPS, MIPS64, and i386.
A telemetry assessment to establish connections manufactured to the server hosting the malware has revealed that “above 91% of the inbound connections stemmed from Taiwan, and there appeared to be a preference for Ruckus-manufactured edge equipment.”
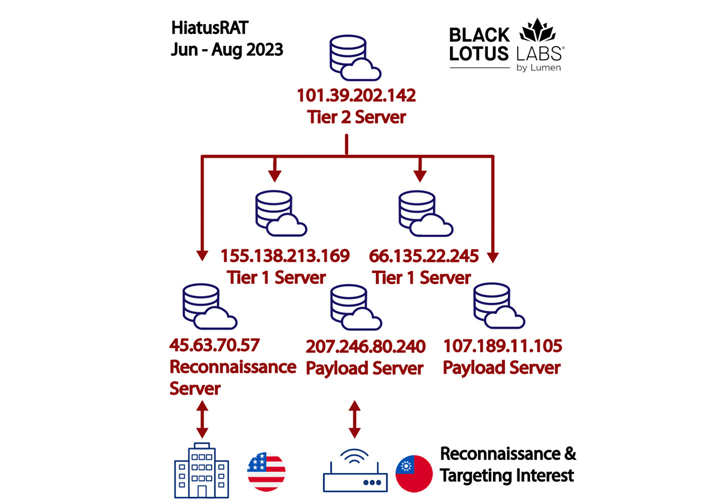
The HiatusRAT infrastructure is composed of payload and reconnaissance servers, which instantly connect with the victim networks. These servers are commandeered by Tier 1 servers, which, in turn, are operated and managed by Tier 2 servers.

The attackers have been identified as using two different IP addresses 207.246.80[.]240 and 45.63.70[.]57 to join to the DoD server on June 13 for about a period of time of two several hours. 11 MB of bi-directional data is approximated to have been transferred during the period.
It can be not clear what the end objective is, but it is really suspected that the adversary could have been wanting for publicly out there facts similar to current and future navy contracts for long run targeting.
The targeting of perimeter property these types of as routers has turn out to be a thing of a sample in current months, with danger actors related with China joined to the exploitation of security flaws in unpatched Fortinet and SonicWall appliances to establish extensive-phrase persistence in concentrate on environments.
“Even with prior disclosures of tools and abilities, the risk actor took the most insignificant of actions to swap out present payload servers and carried on with their functions, with no even making an attempt to re-configure their C2 infrastructure,” the firm said.
Observed this short article fascinating? Observe us on Twitter and LinkedIn to examine additional special material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams
WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams