A lately patched security flaw in the well-known WinRAR archiving software has been exploited as a zero-day because April 2023, new findings from Team-IB reveal.
The vulnerability, cataloged as CVE-2023-38831, makes it possible for risk actors to spoof file extensions, thereby creating it achievable to launch destructive scripts contained in just an archive that masquerades as seemingly innocuous picture or textual content files. It was addressed in edition 6.23 produced on August 2, 2023, along with CVE-2023-40477.
In assaults uncovered by the Singapore-based mostly agency in July 2023, specifically crafted ZIP or RAR archive data files distributed by using buying and selling-linked boards these kinds of as Fx Station have been employed to supply a wide variety of malware people this kind of as DarkMe, GuLoader, and Remcos RAT.

“Right after infecting gadgets, the cybercriminals withdraw income from broker accounts,” Group-IB malware analyst Andrey Polovinkin explained, adding as quite a few as 130 traders’ gadgets have been compromised as element of the campaign. The total range of victims and economical losses stemming from this action are presently not obvious.
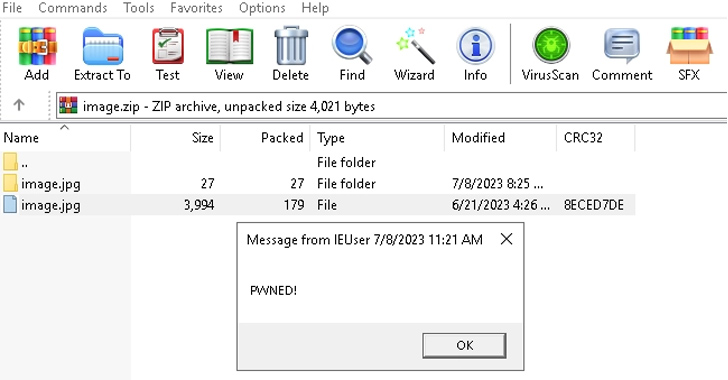
The booby-trapped archive file is produced this sort of that it contains an impression file as effectively as a folder with the similar name.
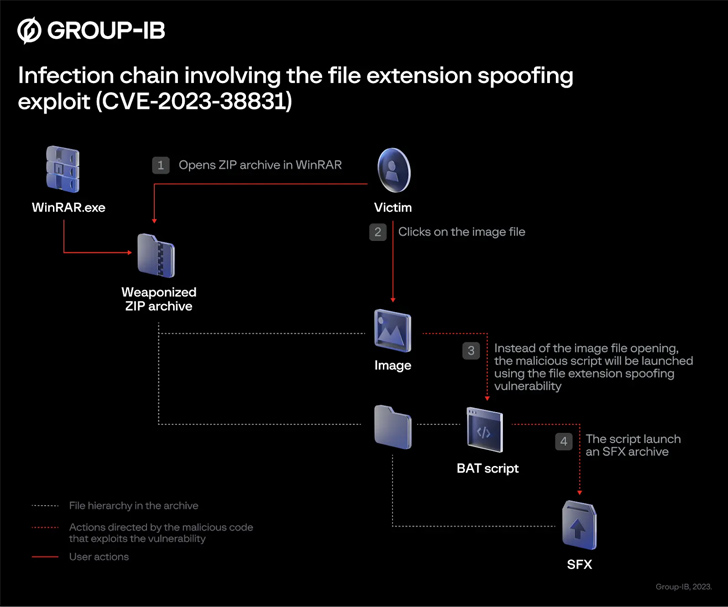
As a final result, when a victim clicks on the image, a batch script current in the folder is executed instead, which is then applied to start the following-phase, an SFX Taxi archive designed to extract and launch further information. At the identical time, the script also masses the decoy image so as not to arouse suspicion.
“CVE-2023-38831 is caused by a processing mistake in opening the file in the ZIP archive,” Polovinkin explained to The Hacker Information. “Weaponized ZIP archives have been dispersed on at least 8 preferred investing discussion boards, so the geolocation of victims is wide, and the assaults are not specific at distinct nations around the world or industries.”

It is really not still regarded who is powering the attacks leveraging the WinRAR flaw. That claimed, DarkMe is a Visible Primary trojan attributed to the EvilNum team, to start with documented by NSFOCUS in September 2022 in connection with a phishing campaign codenamed DarkCasino concentrating on European on-line gambling and trading services.
Also shipped applying this process is a malware strain termed GuLoader (aka CloudEye) that subsequently attempts to fetch Remcos RAT from a remote server.
“The latest cases of exploitation of CVE-2023-38831 remind us of the consistent risks related to software vulnerabilities,” Polovinkin reported. “Danger actors are very resourceful, and they will generally find new methods to find out and subsequently exploit vulnerabilities.”
Found this post intriguing? Stick to us on Twitter and LinkedIn to go through extra distinctive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Thousands of Unpatched Openfire XMPP Servers Still Exposed to High-Severity Flaw
Thousands of Unpatched Openfire XMPP Servers Still Exposed to High-Severity Flaw